[ad_1]
Learn how this cryptocurrency marketing campaign operates and its scope. Then, get tips about defending susceptible Kubernetes situations from this cybersecurity risk.

The cybersecurity firm CrowdStrike has noticed the first-ever Dero cryptojacking marketing campaign. The assault targets Kubernetes clusters that have been accessible on the web and allowed nameless entry to the Kubernetes API.
Jump to:
What is Dero?
Dero is a privacy-focused blockchain platform that goals to offer quick and safe transactions with enhanced privateness options.
Dero makes use of a number of applied sciences, together with CryptoNote, Bulletproofs and its personal proof of labor algorithm to supply personal and nameless transactions with out compromising pace or scalability. Dero makes use of ring signatures and stealth addresses to make sure transactions can’t be traced again to their origin.
Dero additionally offers low switch charges, and the platform is open supply. Dero’s native cryptocurrency is known as DERO.
Some cybercriminals seeing these specs have began utilizing DERO as an alternative of different standard cryptocurrencies which can be used broadly by cybercriminals, equivalent to Bitcoin and Monero.
How does this cryptojacking assault function?
With this cryptojacking assault, the risk actor scans for Kubernetes situations with the authentication parameter set as “–anonymous-auth=true”. Also, as acknowledged by CrowdStrike researchers Benjamin Grap and Manoj Ahuje, “a user with sufficient privileges who runs ‘kubectl proxy’ can unintentionally expose a secure Kubernetes API on the host where kubectl is running, which is a less obvious way to expose the secure Kubernetes cluster bypassing authentication.”
SEE: Remote entry coverage (TechRepublic Premium)
Once a susceptible Kubernetes cluster is discovered, the risk actor deploys a Kubernetes DaemonSet named “proxy-api.” That motion deploys a malicious pod on each node of the cluster, enabling the attacker to run cryptojacking on all nodes from the cluster on the identical time (Figure A).
Figure A
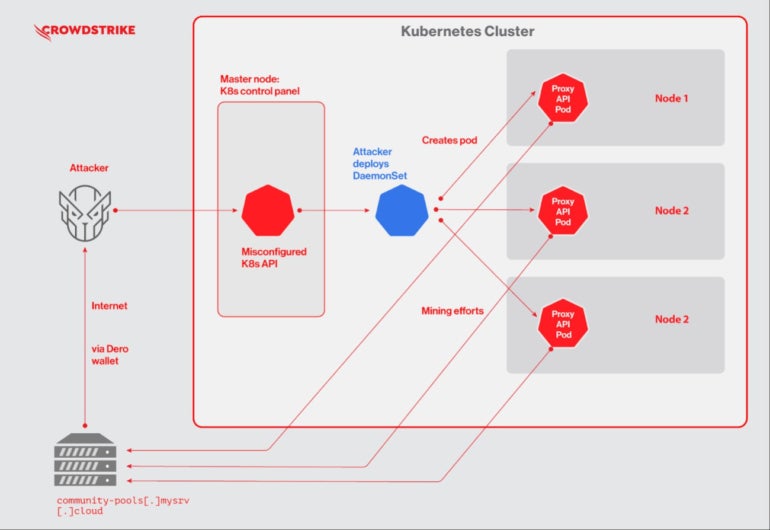
Once it’s all set, mining begins on each pod, producing Dero cash which can be then distributed to a group pool.
What is that this cryptojacking assault’s scope?
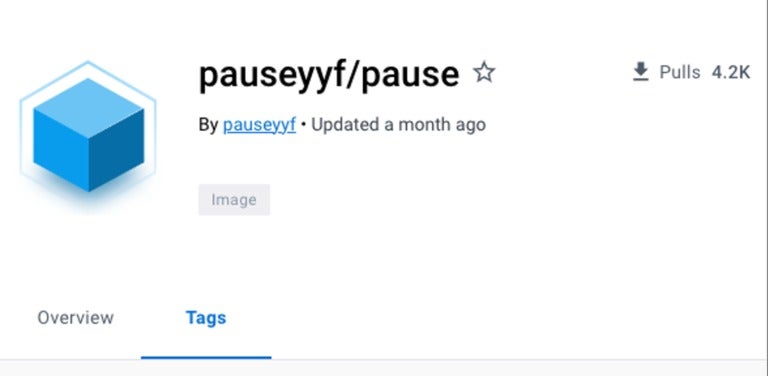
The risk actor makes use of the Docker picture “pauseyyf/pause” that’s hosted on Docker Hub. The Docker picture has greater than 4,200 pulls on the time of this analysis (Figure B), revealing what number of potential miner situations have been deployed.
Figure B
A script file named “entrypoint.sh” runs a Dero coin miner binary named “pause,” utilizing a pockets handle and mining pool as arguments.
Attackers have most likely named the miner “pause” as a result of pause containers in authentic Kubernetes situations are used to bootstrap pods. That naming possible helps attackers keep away from apparent detection.
As famous by researchers, attackers don’t try to maneuver laterally or pivot in any method across the Kubernetes situations, that means they don’t seem to be serious about something aside from mining sources for producing Dero cash.
Unlike different cryptocurrencies, equivalent to Bitcoin, it’s not doable to examine the steadiness of the pockets handle used within the assault marketing campaign.
A brand new Monero cryptocurrency assault
In February 2023, one other marketing campaign hit susceptible Kubernetes situations, this time aiming at mining Monero cryptocurrency.
The new marketing campaign began by deleting present Kubernetes DaemonSets named “proxy-api,” which was particular to the Dero cryptojacking marketing campaign. In different phrases, the risk actor deploying the brand new marketing campaign knew in regards to the present Dero cryptojacking operation and needed to knock it off.
In addition to deleting the proxy-api DaemonSets, the attacker additionally deleted DaemonSets named “api-proxy” and “k8s-proxy,” which have been probably chargeable for different assault campaigns.
The Monero marketing campaign is extra subtle than the Dero marketing campaign, because it deploys a privileged pod and mounted a “host” listing in makes an attempt to flee the container. It additionally created a cron job to run a payload and use a rootkit to cover the mining course of.
How to guard your Kubernetes situations
It is crucial to guard Kubernetes situations which can be accessible from the web. Follow the following pointers for optimum safety:
For starters, no Kubernetes occasion ought to permit nameless entry. Strong authentication needs to be enforced to entry Kubernetes, equivalent to multi-factor authentication to make sure solely approved customers can entry the occasion.
You must also deploy role-based entry management to regulate entry to Kubernetes sources based mostly on person roles and permissions.
On a wider scale, whether or not it’s for Kubernetes or Docker, container photos ought to solely be downloaded from trusted sources like official repositories or respected distributors. Even then, photos ought to nonetheless be scanned for vulnerabilities.
From there, allow logging and monitor exercise on all Kubernetes situations with the intention to detect suspicious exercise or entry makes an attempt.
Finally, hold all software program updated and patched to handle recognized vulnerabilities and safety points.
Read subsequent: Security danger evaluation guidelines (TechRepublic Premium)
Disclosure: I work for Trend Micro, however the views expressed on this article are mine.
[ad_2]
