[ad_1]
Authored by Lakshya Mathur and Sriram P
McAfee Intelligence noticed an enormous spike in extortion electronic mail frauds over the previous month. The intent of those fraudulent actions is to intimidate people into paying a specified amount of cash as a ransom.
Figure 1 exhibits the variety of blackmail emails obtained over a month not too long ago.
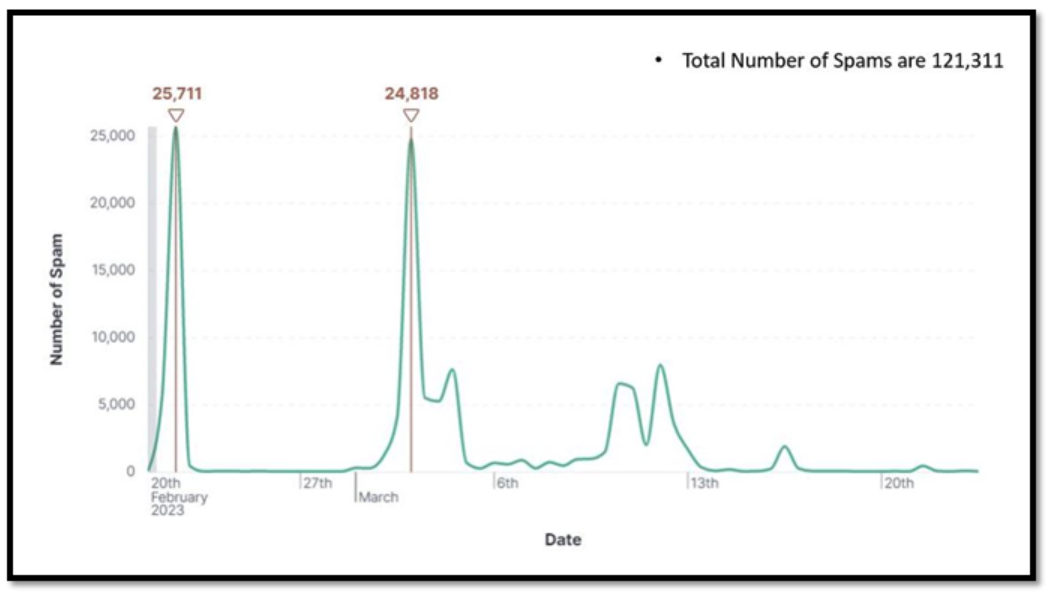
Figure 1 – Stats for 20 February 2023 – 23rd March 2023
In this weblog, we’ll delve into frauds which might be changing into more and more frequent within the digital age. We’ll first outline what these frauds are and supply examples to assist readers higher perceive the character of those frauds. Additionally, we’ll discover how these frauds are on the rise, highlighting the explanations behind this development and the influence it has on people.
Finally, we’ll present sensible recommendation to assist shoppers shield themselves from most of these assaults. This will embrace a dialogue of among the only measures people can take to safeguard their private and monetary info from fraudsters.
What are Extortion Frauds?
Extortion emails are a sort of rip-off the place cybercriminals ship threatening messages to people or organizations—demanding cost in trade for not releasing delicate or embarrassing info. These emails sometimes declare that the sender has compromising info, corresponding to non-public pictures or private knowledge, and threaten to share it with the recipient’s pals, household, or the general public until a cost is made. The cost is often requested within the type of cryptocurrency, corresponding to Bitcoin within the latest spam, which is troublesome to hint and may be transferred shortly and anonymously. The purpose of those emails is to scare the recipient into paying the demanded quantity, though there won’t be any compromising info to launch.
Examples of Extortion fraud
Scammers use completely different scareware sentiments like dangerous web shopping habits, hacking for Wi-Fi, and hacking of networks due to {hardware} vulnerabilities. We’ll now look at numerous illustrations of extortion emails and analyze scammers’ methods to intimidate victims into offering cost. By presenting numerous real-life examples, we will reveal how scammers use scareware techniques to control and intimidate their victims into complying with their calls for. By instilling worry, the scammers hope to impress a way of urgency within the sufferer, growing the probability that they’ll pay the demanded ransom.
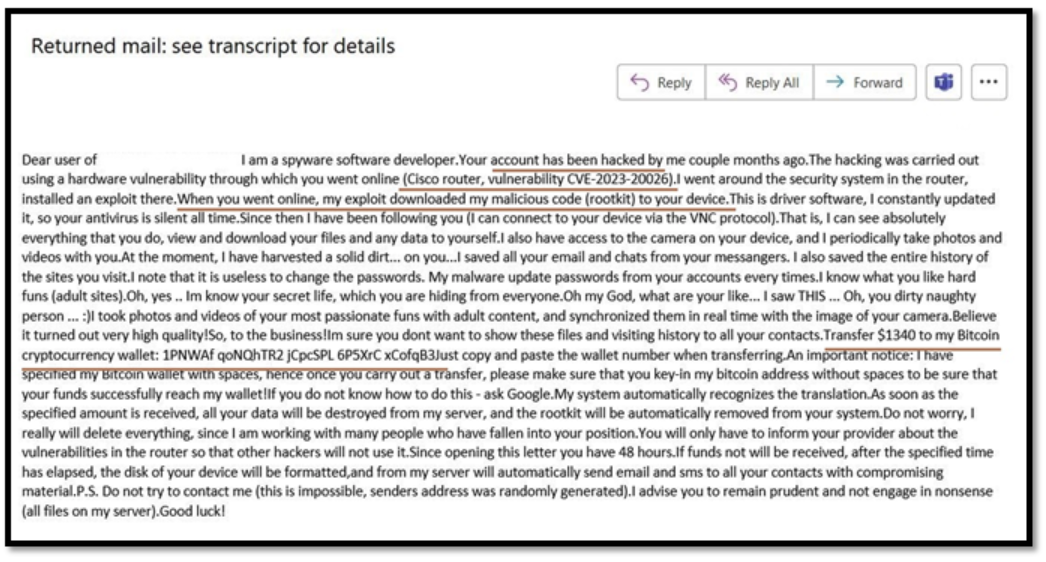
Figure 2 – Extortion fraud Example 1
Figure 2 is an illustration of a typical extortion electronic mail that scammers use to take advantage of their victims. In this occasion, the scammer is claiming to have gained unauthorized entry to the sufferer’s account by means of a safety vulnerability in a Cisco router. The scammer is then threatening to show embarrassing details about the sufferer until a cost of $1,340 is made.
The cost is demanded by means of a Bitcoin pockets handle that the scammer has supplied. In this instance, the scammer has obfuscated the Bitcoin pockets handle by including areas between the characters, which is a tactic used to make it tougher to trace the cost. Now, allow us to look at one other occasion of extortion emails.
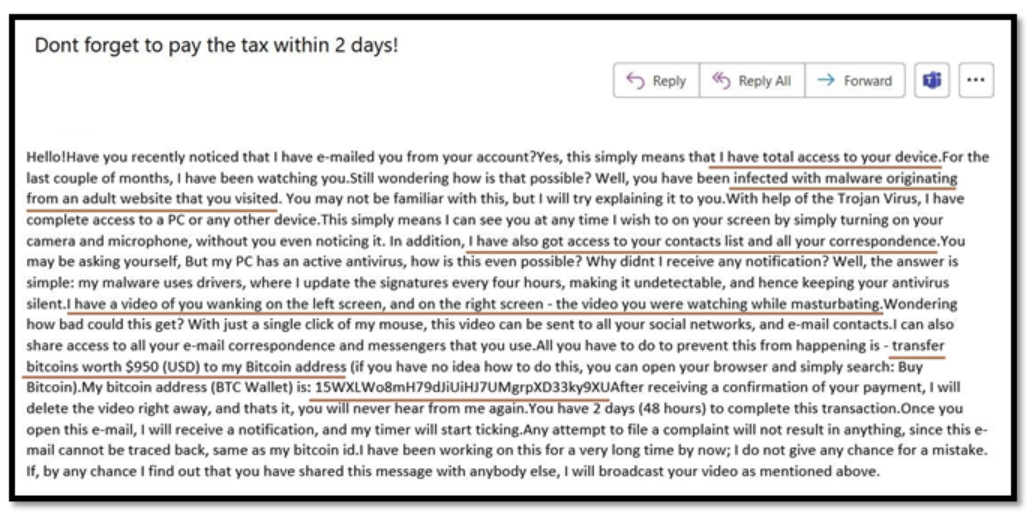
Figure 3 – Extortion fraud instance 2
Figure 3 is one other instance of an extortion electronic mail that scammers use to trick and manipulate their victims. In this case, the attacker is claiming to have gained unauthorized entry to the sufferer’s accounts and has deployed trojans and viruses on the sufferer’s system. The scammer can also be blackmailing the sufferer by alleging that they’ve specific grownup content material in regards to the sufferer and the sufferer’s internet shopping historical past. The function of that is to instill worry and provoke a way of urgency within the sufferer.
Like the earlier instance, the scammer has supplied a Bitcoin pockets handle for the sufferer to make a ransom cost of $950. Additionally, the attacker has defined that the virus they’ve deployed is undetectable by antivirus software program as a result of they’ve used drivers that replace the virus each few hours.
Use of Cryptocurrency
Cryptocurrency instruments are the commonest manner these scammers ask for a ransom. They use this tactic as a result of it’s troublesome to hint and may be despatched shortly and anonymously to different platforms. We seen that scammers have been demanding ransom funds by means of Bitcoin wallets. So, we tried to collect statistics on the variety of distinctive Bitcoin wallets we got here throughout prior to now month.
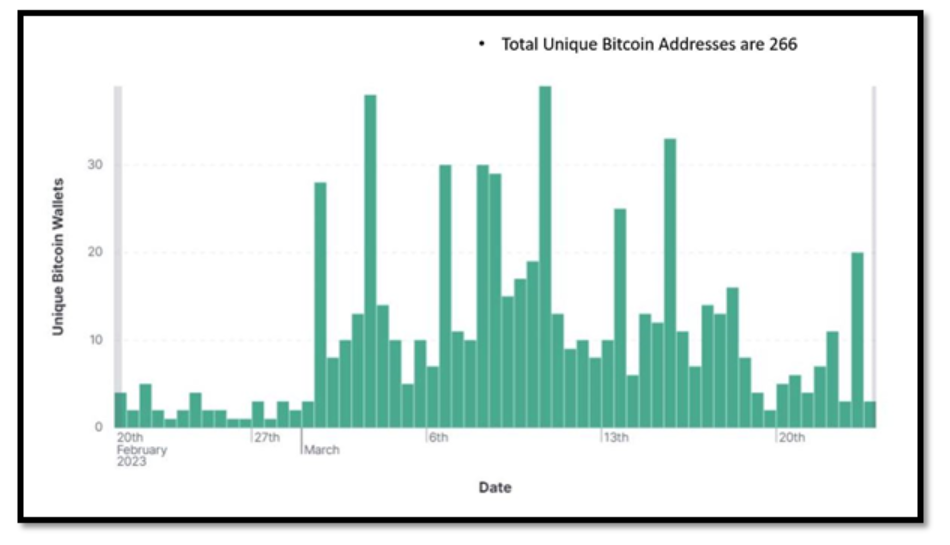
Figure 4 – Unique Bitcoin Stats for 20th February 2023 – 23rd March 2023
We checked these Bitcoin addresses to see what their transactions actions are and their popularity on the blockchain and Bitcoin abuse database. Below are some snapshots of the transaction of those addresses.
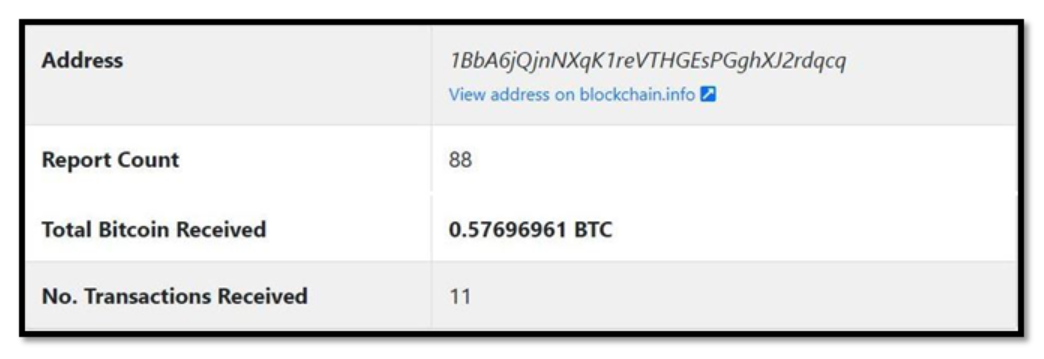
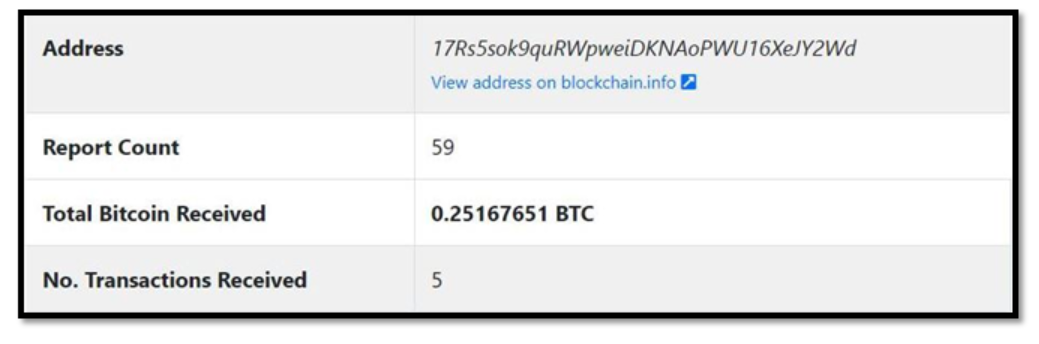
Figure 5 – Bitcoin obtained, and abuse report depend for Bitcoin handle
As illustrated in Figure 5, it’s clear that the Bitcoin addresses talked about in these extortion emails have quite a few abuse stories in opposition to them. Additionally, some ransom funds have been obtained by means of these addresses. Our intelligence additionally collected weekly tendencies on how a lot cash that they had inside them.
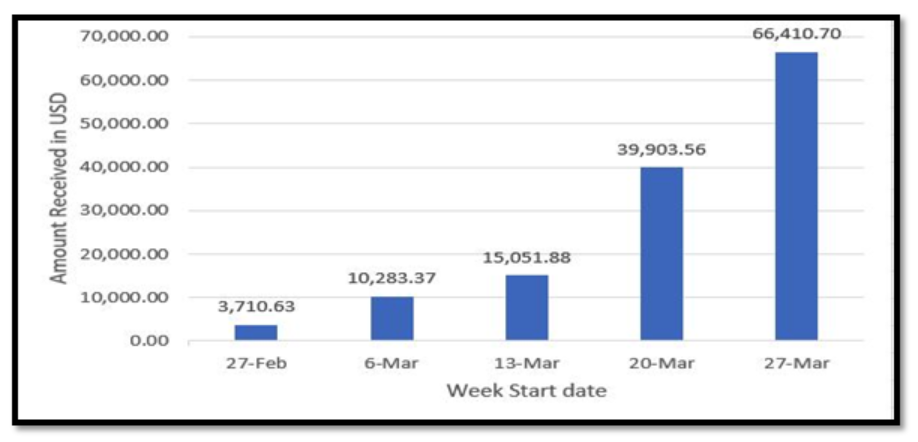
Figure 6 – Total Amount obtained (US Dollars) in that week
Figure 6 exhibits that the amount of cash obtained in these Bitcoin addresses is growing weekly. This implies that scammers are efficiently extorting cash from extra shoppers.
How to keep away from these frauds?
If you obtain extortion emails, observe the steps outlined under.
- Don’t make any choices shortly and don’t panic. If you panic that will probably be a win for these scammers.
- Mostly the stuff they scare you about within the mail is at all times false. As quickly as you obtain such assume twice earlier than sending cost emails, to dam them and delete them.
- Try to look necessary key phrases in your search engines like google, for instance, if scammers are claiming to take advantage of Cisco router vulnerabilities search that vulnerability with key phrases like ‘BTC’, ‘hack’, and another key phrases from the e-mail, and one can find many outcomes which can allow you to to know that the scammer’s claims are solely false.
- Try to find extra in regards to the electronic mail you bought, you possibly can seek for the sender’s handle, the topic of the mail, and even sure paragraphs from the mail on the web. You will certainly get info on how these emails are solely scareware.
- Keep your self educated on such scams so to shield your self.
- Keep your antivirus up to date and do well timed full scans of your machines.
- Don’t surf on questionable internet pages or obtain unlawful/cracked software program.
Despite developments in expertise, extortion frauds proceed to extend as seen on this weblog. However, the most effective protection in opposition to such scams is to stay calm, and knowledgeable, and to make others conscious of such frauds. By following the steps talked about above, corresponding to not responding to or paying any ransom calls for, retaining your system and software program up to date, utilizing sturdy passwords, and being cautious of surprising emails or hyperlinks, you possibly can shield your self from falling sufferer to those frauds. It is necessary to remain vigilant and to report any questionable exercise to the applicable authorities. By taking these precautions, you possibly can assist forestall your self and others from changing into victims of extortion fraud.
