[ad_1]

An replace was added to the top of the article explaining that any Authenticode-signed file, together with executables, will be modified to bypass warnings.
A brand new Windows zero-day permits menace actors to make use of malicious stand-alone JavaScript recordsdata to bypass Mark-of-the-Web safety warnings. Threat actors are already seen utilizing the zero-day bug in ransomware assaults.
Windows features a safety characteristic known as Mark-of-the-Web (MoTW) that flags a file as having been downloaded from the Internet and, due to this fact, must be handled with warning because it could possibly be malicious.
The MoTW flag is added to a downloaded file or e-mail attachment as a particular Alternate Data Stream known as ‘Zone.Identifier,’ which will be seen utilizing the ‘dir /R’ command and opened instantly in Notepad, as proven beneath.
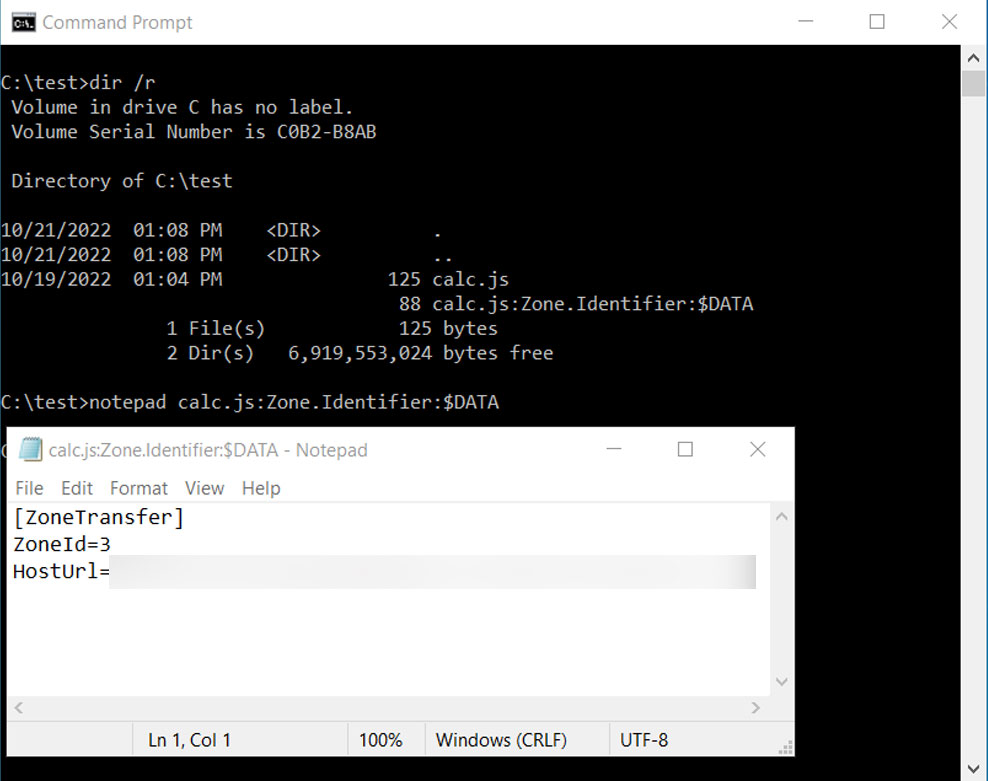
Source: BleepingComputer
This ‘Zone.Identifier’ alternate information stream consists of what URL safety zone the file is from (three equals the Internet), the referrer, and the URL to the file.
When a person makes an attempt to open a file with the Mark-of-the-Web flag, Windows will show a warning that the file must be handled with warning.
“While recordsdata from the Internet will be helpful, this file kind can doubtlessly hurt your laptop. If you don’t belief the supply, don’t open this software program,” reads the warning from Windows.
.jpg)
Source: BleepingComputer
Microsoft Office additionally makes use of the MoTW flag to find out if the file must be opened in Protected View, inflicting macros to be disabled.
Windows MoTW bypass zero-day flaw
The HP menace intelligence workforce not too long ago reported that menace actors are infecting units with Magniber ransomware utilizing JavaScript recordsdata.
To be clear, we’re not speaking about JavaScript recordsdata generally used on nearly all web sites, however .JS recordsdata distributed by menace actors as attachments or downloads that may run exterior of an internet browser.
The JavaScript recordsdata seen distributed by the Magniber menace actors are digitally signed utilizing an embedded base64 encoded signature block as described on this Microsoft assist article.
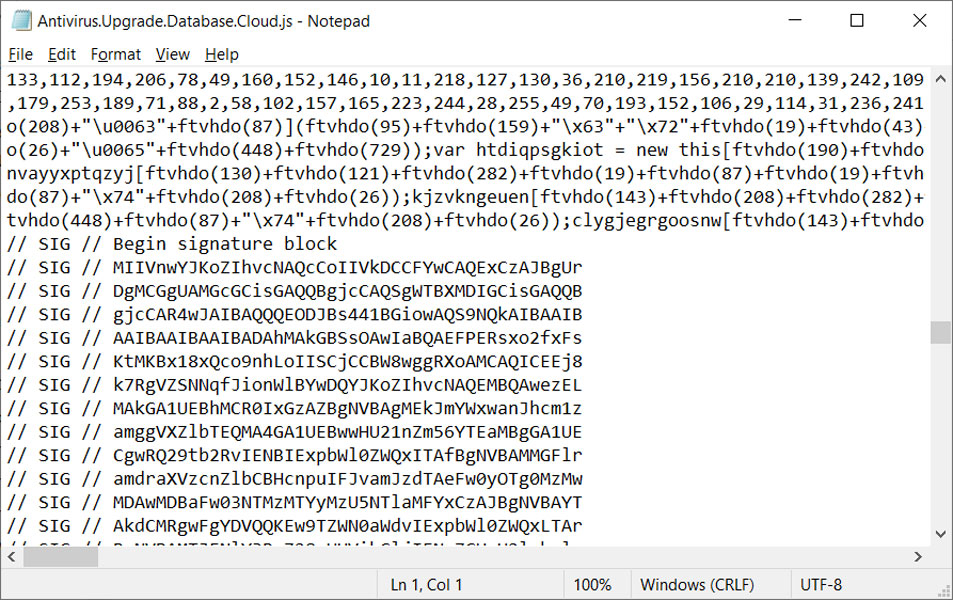
Source: BleepingComputer
After being analyzed by Will Dormann, a senior vulnerability analyst at ANALYGENCE, he found that the attackers signed these recordsdata with a malformed key.
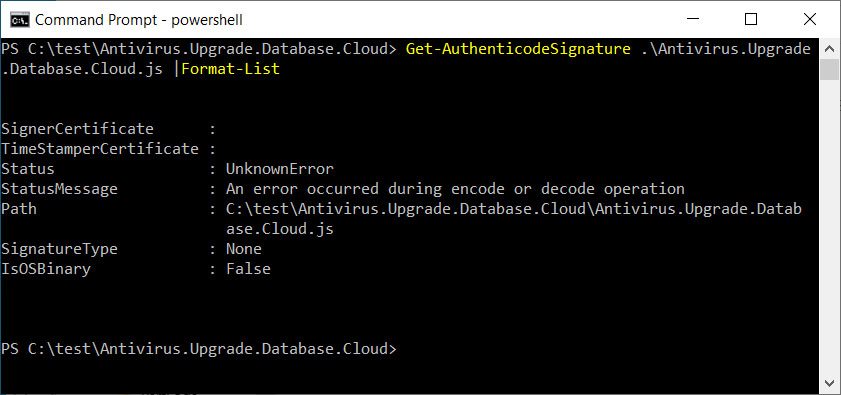
Source: BleepingComputer
When signed on this method, although the JS file was downloaded from the Internet and obtained a MoTW flag, Microsoft wouldn’t show the safety warning, and the script would routinely execute to put in the Magniber ransomware.
Dormann additional examined the usage of this malformed signature in JavaScript recordsdata and was capable of create proof-of-concept JavaScript recordsdata that might bypass the MoTW warning.
Both of those JavaScript (.JS) recordsdata have been shared with BleepingComputer, and as you’ll be able to see beneath, they each obtained a Mark-of-the-Web, as indicated by the purple packing containers, when downloaded from an internet site.
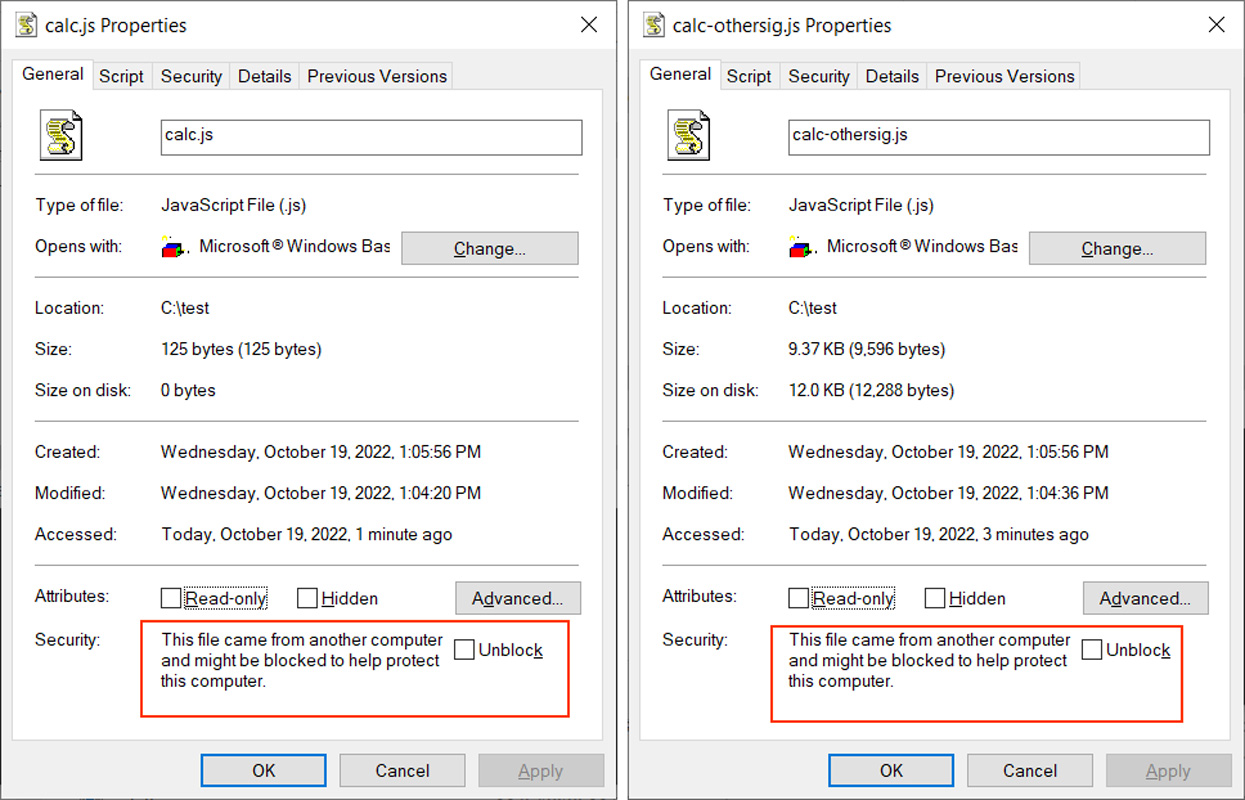
Source: BleepingComputer
The distinction between the 2 recordsdata is that one is signed utilizing the identical malformed key from the Magniber recordsdata, and the opposite incorporates no signature in any respect.
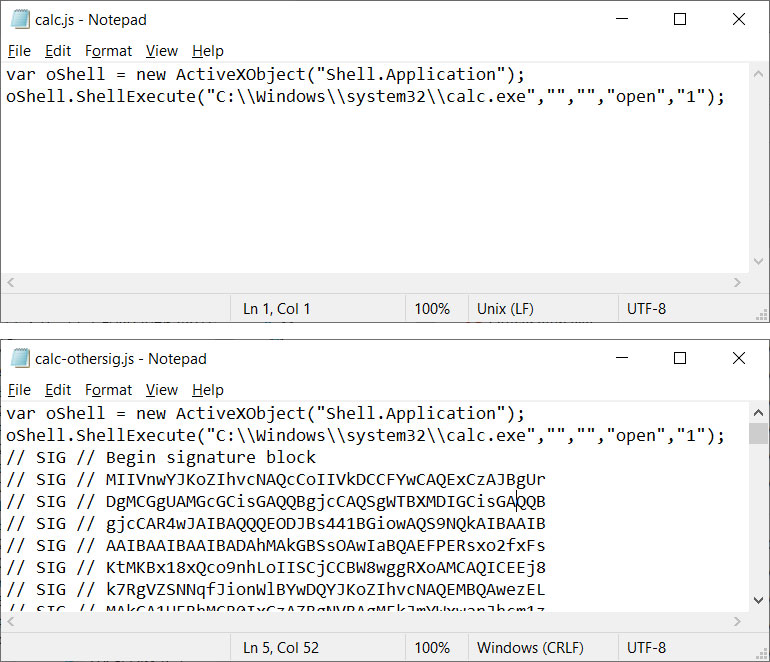
Source: BleepingComputer
When the unsigned file is opened in Windows 10, a MoTW safety warning is correctly displayed.
However, when double-clicking the ‘calc-othersig.js,’ which is signed with a malformed key, Windows doesn’t show a safety warning and easily executes the JavaSript code, as demonstrated beneath.
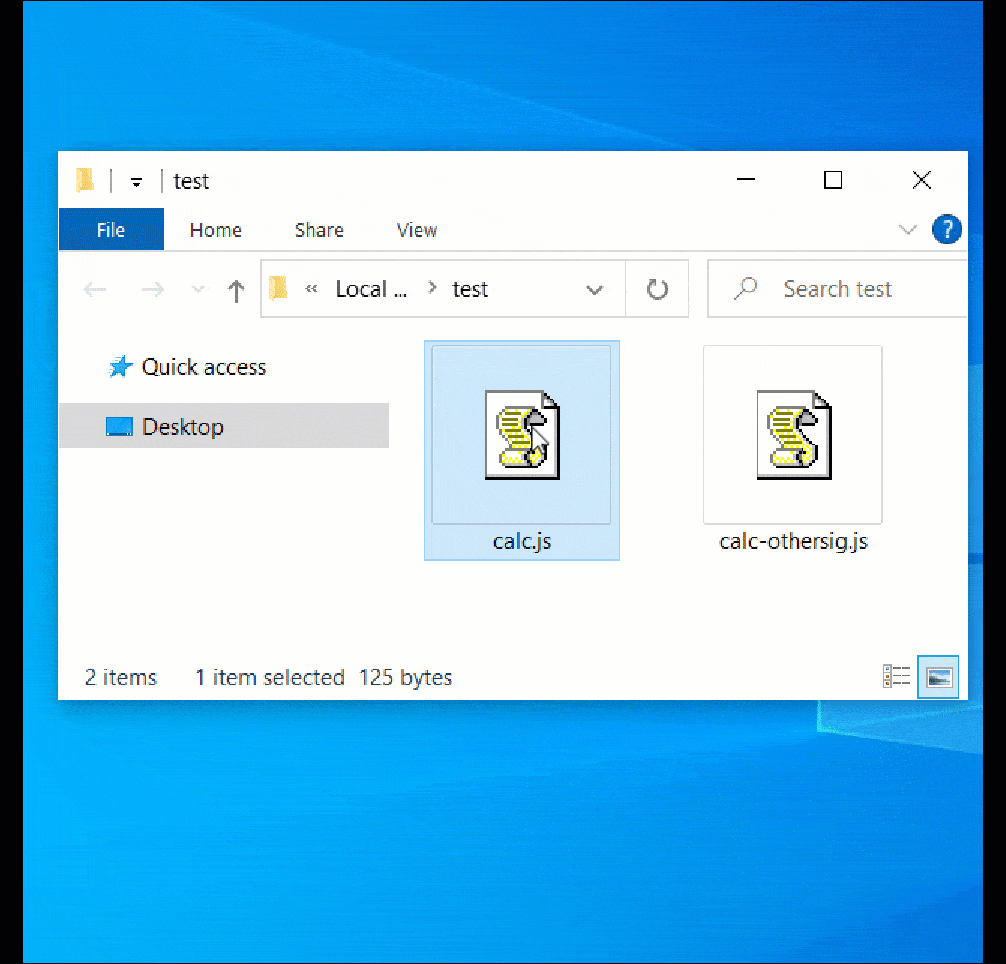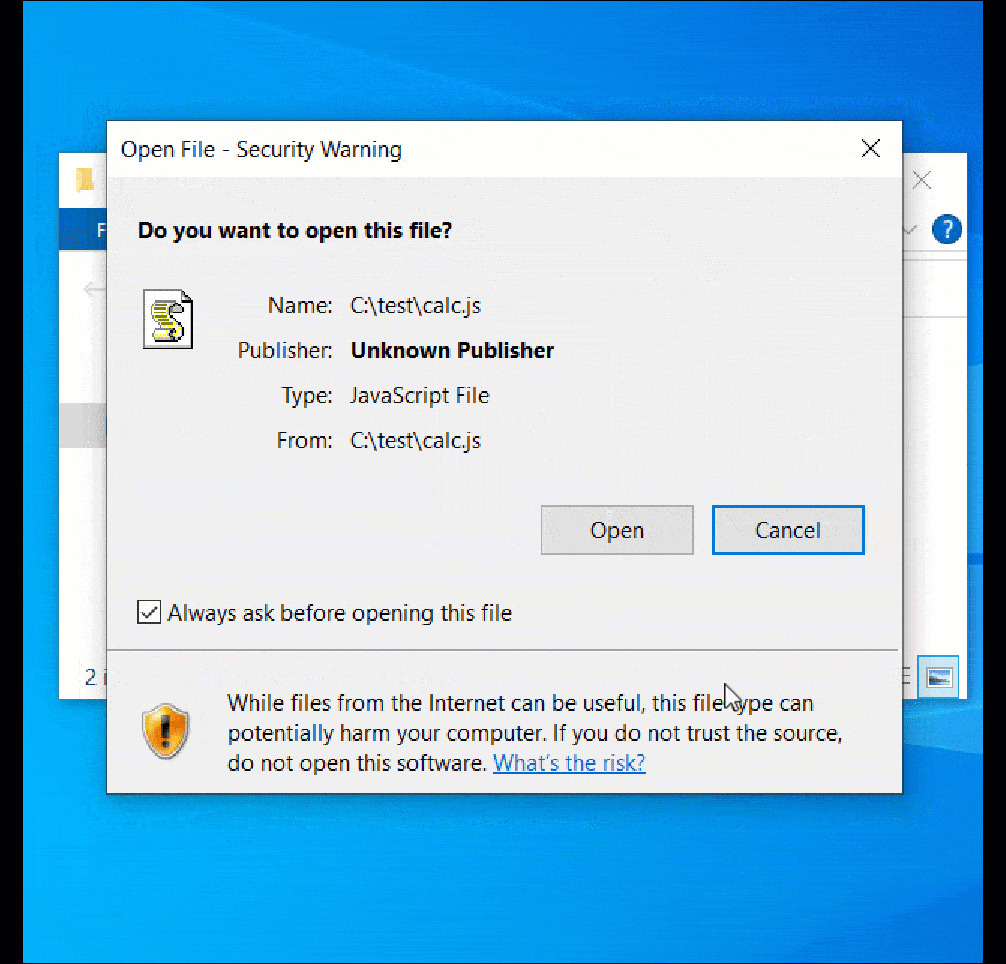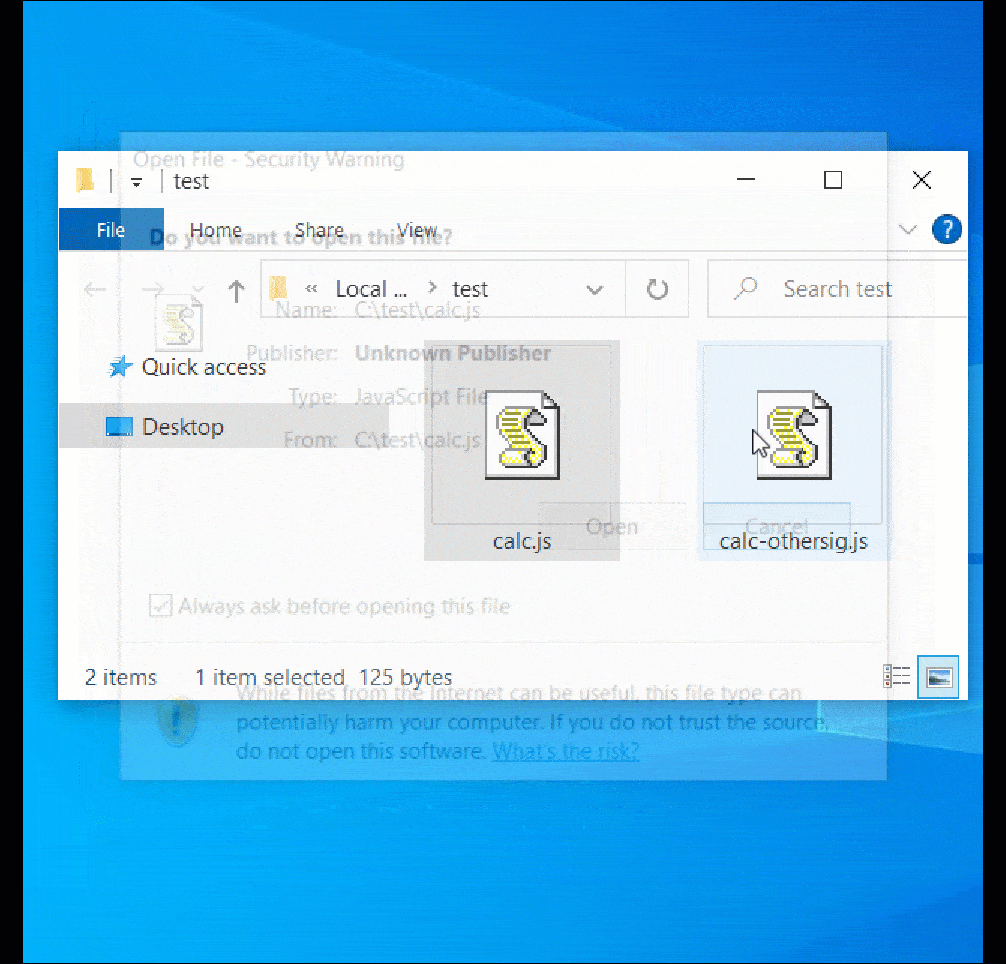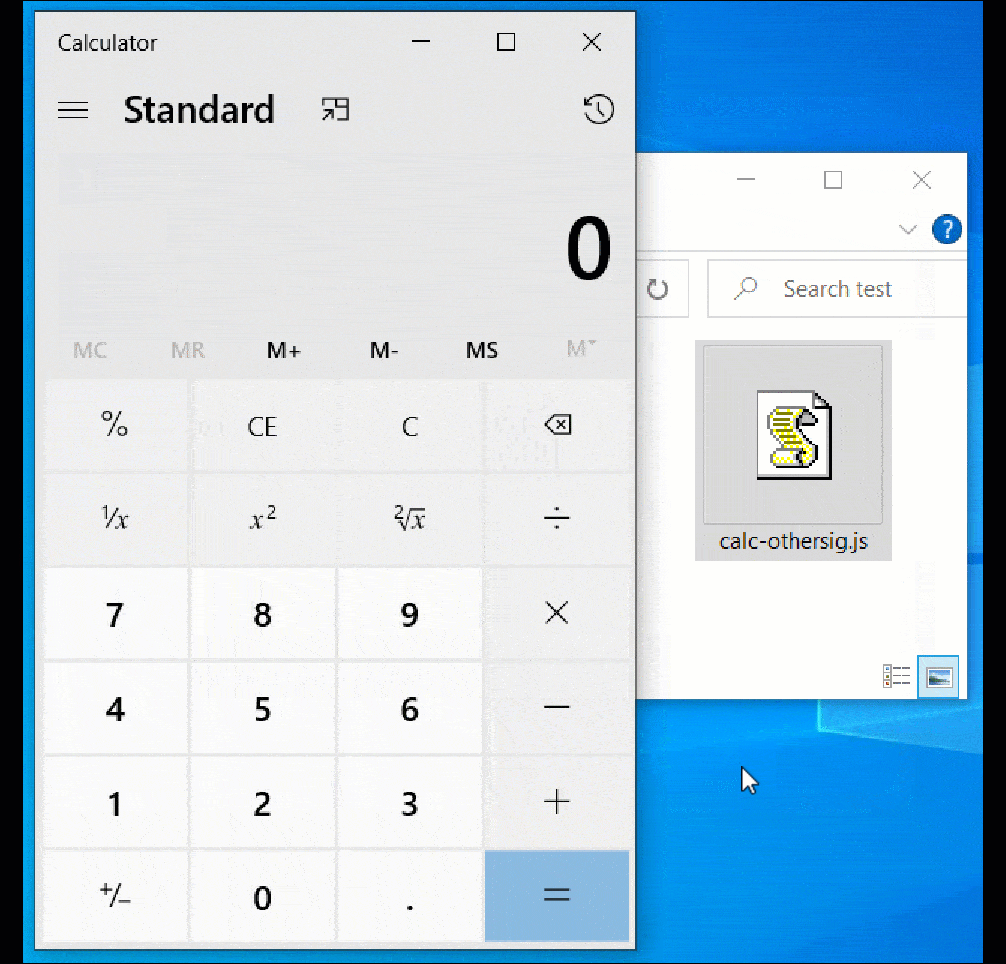
Source: BleepingComputer
Using this system, menace actors can bypass the traditional safety warnings proven when opening downloaded JS recordsdata and routinely execute the script.
BleepingComputer was capable of reproduce the bug in Windows 10. However, for Windows 11, the bug would solely set off when operating the JS file instantly from an archive.
Dormann advised BleepingComputer that he believes this bug was first launched with the discharge of Windows 10, as a totally patched Windows 8.1 machine shows the MoTW safety warning as anticipated.
And fully-patched 8.1 will get it proper.
So I’ll say it is honest to say that this bug was launched with the discharge of Windows 10. pic.twitter.com/jJbP9quvL6— Will Dormann (@wdormann) October 20, 2022
According to Dormann, the bug stems from Windows 10’s new ‘Check apps and recordsdata’ SmartScreen characteristic beneath Windows Security > App & Browser Control > Reputation-based safety settings.
“This challenge is within the new-as-of-Win10 SmartScreen characteristic. And disabling “Check apps and recordsdata” reverts Windows to the legacy habits, the place MotW prompts are unrelated to Authenticode signatures,” Dormann advised BleepingComputer.
“So that entire setting is sadly at present a tradeoff. On one hand, it does scan for baddies which are downloaded.”
“On the opposite, baddies that benefit from this bug can get a LESS-SECURE habits from Windows in comparison with when the characteristic is disabled.”
The zero-day vulnerability is especially regarding as we all know menace actors are actively exploiting it in ransomware assaults.
Dormann shared the proof-of-concept with Microsoft, who mentioned they might not reproduce the MoTW safety warning bypass.
However, Microsoft advised BleepingComputer that they’re conscious of the reported challenge and are investigating it.
Update 10/22/22
After the publication of this text, Dormann advised BleepingComputer that menace actors may modify any Authenticode-signed file, together with executables (.EXE), to bypass the MoTW safety warnings.
To do that, Dormann says {that a} signed executable will be modified utilizing a hex editor to alter among the bytes within the signature portion of the file and thus corrupt the signature.
Can we do the identical trick with a signed EXE file?
Sure! Why not?
We have a VM with out web connectivity, so we’ll see a SmartScreen warning once we know it is being checked.
Signed calcxp.exe – (Checked w/ SmartScreen)
Modified a byte in sig – (No SmartScreen test)
pic.twitter.com/4WwdDBpU0a— Will Dormann (@wdormann) October 18, 2022
Once the signature is corrupted, Windows won’t test the file utilizing SmartScreen, as if a MoTW flag was not current, and permit it to run.
“Files which have a MotW are handled as if there have been no MotW if the signature is corrupt. What real-world distinction that makes will depend on what kind of file it’s,” defined Dormann.
