[ad_1]
The Keksec menace actor has been linked to a beforehand undocumented malware pressure, which has been noticed within the wild masquerading as an extension for Chromium-based net browsers to enslave compromised machines right into a botnet.
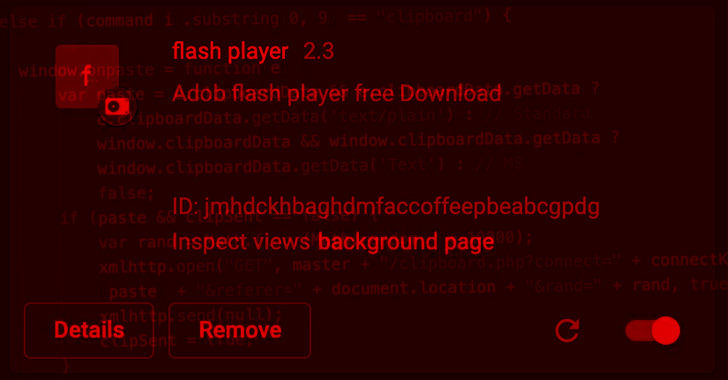
Called Cloud9 by safety agency Zimperium, the malicious browser add-on comes with a variety of options that permits it to siphon cookies, log keystrokes, inject arbitrary JavaScript code, mine crypto, and even enlist the host to hold out DDoS assaults.
The extension “not solely steals the knowledge obtainable throughout the browser session however may also set up malware on a consumer’s system and subsequently assume management of your entire system,” Zimperium researcher Nipun Gupta mentioned in a brand new report.
The JavaScript botnet is not distributed through Chrome Web Store or Microsoft Edge Add-ons, however moderately by means of faux executables and rogue web sites disguised as Adobe Flash Player updates.
Once put in, the extension is designed to inject a JavaScript file known as “marketing campaign.js” on all pages, that means the malware may additionally function as a standalone piece of code on any web site, reputable or in any other case, doubtlessly main watering gap assaults.
The JavaScript code takes duty for cryptojacking operations, abusing the sufferer’s computing assets to illicitly mine cryptocurrencies, in addition to inject a second script named “cthulhu.js.”
This assault chain, in flip, exploits flaws in net browsers similar to Mozilla Firefox (CVE-2019-11708, CVE-2019-9810), Internet Explorer (CVE-2014-6332, CVE-2016-0189), and Edge (CVE-2016-7200) to flee the browser sandbox and deploy malware on the system.
The script additional acts as a keylogger and a conduit for launching further instructions obtained from a distant server, permitting it to steal clipboard knowledge, browser cookies, and launching layer 7 DDoS assaults in opposition to any area.
Zimperium attributed the malware to a menace actor tracked as Keksec (aka Kek Security, Necro, and FreakOut), which has a historical past of creating a variety of botnet malware, together with EnemyBot, for crypto mining and DDoS operations.
The connection to Keksec comes from overlaps within the domains that had been beforehand recognized as utilized by the malware group.
The undeniable fact that Cloud9 is JavaScript-based and is obtainable both without cost or a small price on hacker boards makes it doable for less-skilled cybercriminals to get quick access to low-cost choices for launching assaults focusing on completely different browsers and working programs.
The disclosure comes over three months after Zimperium found a malicious browser add-on dubbed ABCsoup that posed as a Google Translate device to strike Russian customers of Google Chrome, Opera, and Mozilla Firefox browsers.
“Users ought to be skilled on the dangers related to browser extensions exterior of official repositories, and enterprises ought to contemplate what safety controls they’ve in place for such dangers,” Gupta mentioned.
[ad_2]