[ad_1]
Two long-running surveillance campaigns have been discovered concentrating on the Uyghur group in China and elsewhere with Android adware instruments designed to reap delicate info and monitor their whereabouts.
This encompasses a beforehand undocumented malware pressure known as BadBazaar and up to date variants of an espionage artifact dubbed MOONSHINE by researchers from the University of Toronto’s Citizen Lab in September 2019.
“Mobile surveillance instruments like BadBazaar and MOONSHINE can be utilized to trace most of the ‘pre-criminal’ actions, actions thought of indicative of non secular extremism or separatism by the authorities in Xinjiang,” Lookout mentioned in an in depth write-up of the operations.
The BadBazaar marketing campaign, based on the safety agency, is claimed so far way back to late 2018 and comprise 111 distinctive apps that masquerade as benign video gamers, messengers, non secular apps, and even TikTok.
While these samples have been distributed by means of Uyghur-language social media platforms and communication channels, Lookout famous it discovered a dictionary app named “Uyghur Lughat” on the Apple App Store that communicates with a server utilized by its Android counterpart to collect primary iPhone info.
The iOS app continues to be accessible on the App Store.
“Since BadBazaar variants typically purchase their surveillance capabilities by downloading updates from their [command-and-control server], it’s doable the risk actor is hoping to later replace the iOS pattern with comparable surveillance performance,” the researchers identified.
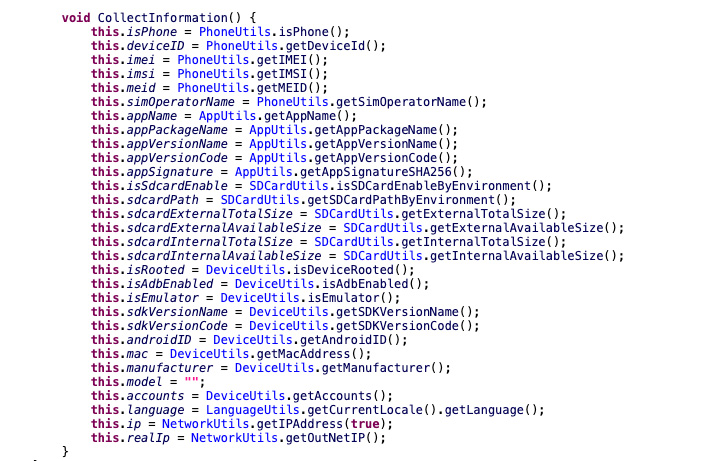
BadBazaar, as soon as put in, comes with a number of options that enable it to gather name logs, GPS areas, SMS messages, and information of curiosity; file cellphone calls; take footage; and exfiltrate substantial system metadata.
Further evaluation of BadBazaar’s infrastructure has revealed overlaps with one other adware operation aimed on the ethnic minority that got here to mild in July 2020 and which made use of an Android toolset known as DoubleAgent.
Attacks using MOONSHINE, in an identical vein, have employed over 50 malicious apps since July 2022 which might be engineered to amass private knowledge from the contaminated gadgets, along with recording audio and downloading arbitrary information.
“The majority of those samples are trojanized variations of well-liked social media platforms, like WhatsApp or Telegram, or trojanized variations of Muslim cultural apps, Uyghur-language instruments, or prayer apps,” the researchers mentioned.
Prior malicious cyber actions leveraging the MOONSHINE Android adware equipment have been attributed to a risk actor tracked as POISON CARP (aka Evil Eye or Earth Empusa), a China-based nation-state collective identified for its assaults in opposition to Uyghurs.
The findings come just a little over a month after Check Point disclosed particulars of one other long-standing surveillanceware operation aimed on the Turkic Muslim group that deployed a trojan named MobileOrder since at the very least 2015.
“BadBazaar and these new variants of MOONSHINE add to the already intensive assortment of distinctive surveillanceware utilized in campaigns to surveil and subsequently detain people in China,” Lookout mentioned.
“The large distribution of each BadBazaar and MOONSHINE, and the speed at which new performance has been launched point out that growth of those households is ongoing and that there’s a continued demand for these instruments.”
The growth additionally follows a report from Google Project Zero final week, which uncovered proof of an unnamed business surveillance vendor weaponizing three zero-day safety flaws in Samsung telephones with an Exynos chip working kernel model 4.14.113. The safety holes have been plugged by Samsung in March 2021.
That mentioned, the search large mentioned the exploitation mirrored a sample much like latest compromises the place malicious Android apps have been abused to focus on customers in Italy and Kazakhstan with an implant known as Hermit, which has been linked to Italian firm RCS Lab.