[ad_1]
A malicious Python bundle uploaded to the Python Package Index (PyPI) has been discovered to include a fully-featured data stealer and distant entry trojan.
The bundle, named colourfool, was recognized by Kroll’s Cyber Threat Intelligence staff, with the corporate calling the malware Colour-Blind.
“The ‘Colour-Blind’ malware factors to the democratization of cybercrime that might result in an intensified menace panorama, as a number of variants could be spawned from code sourced from others,” Kroll researchers Dave Truman and George Glass mentioned in a report shared with The Hacker News.
colourfool, like different rogue Python modules found in latest months, conceals its malicious code within the setup script, which factors to a ZIP archive payload hosted on Discord.
The file comprises a Python script (code.py) that comes with totally different modules designed to log keystrokes, steal cookies, and even disable safety software program.
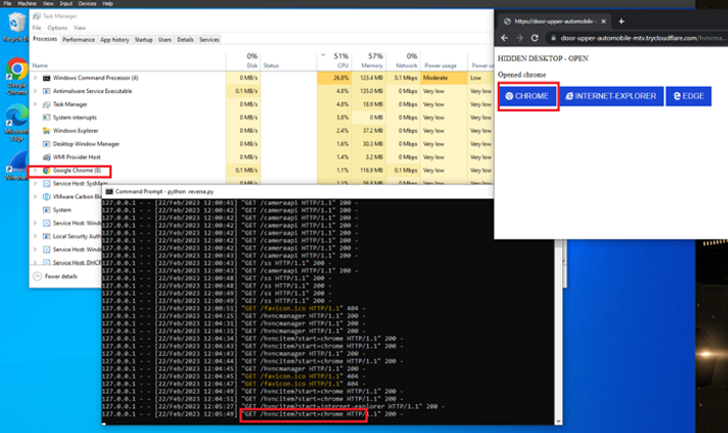
The malware, moreover performing protection evasion checks to find out if it is being executed in a sandbox, establishes persistence by the use of a Visual Basic script and makes use of switch[.]sh for information exfiltration.
“As a technique of distant management, the malware begins a Flask internet software, which it makes accessible to the web by way of Cloudflare’s reverse tunnel utility ‘cloudflared,’ bypassing any inbound firewall guidelines,” the researchers mentioned.
The use of Cloudflare tunnels mirrors one other marketing campaign that was disclosed by Phylum final month which made use of six fraudulent packages to distribute a stealer-cum-RAT dubbed poweRAT.
“There are sturdy similarities between the malware in that they each use Flask and Cloudflare,” Truman advised The Hacker News. “However, while the Phylum researched malware depends on PowerShell for a lot of its key performance, ‘Colour-Blind’ is sort of completely written in Python.”
“Combine this with the performance introduced by the Flask internet software performing totally different actions, reasonably than the newer malware including to the performance of the older, it may imply that the connection is extra within the type of the totally different menace actors sharing concepts, sources or code, reasonably than an evolution of a code base being developed by a single actor,” Truman added.
The trojan is function wealthy and is able to gathering passwords, terminating functions, taking screenshots, logging keystrokes, opening arbitrary internet pages on a browser, executing instructions, capturing crypto pockets information, and even snooping on victims by way of the net digicam.
The findings come as menace actors are leveraging the supply code related to W4SP stealer to spawn copycat variations which might be distributed by way of Python packages like ratebypass, imagesolverpy, and 3m-promo-gen-api.
Discover the Latest Malware Evasion Tactics and Prevention Strategies
Ready to bust the 9 most harmful myths about file-based assaults? Join our upcoming webinar and grow to be a hero within the battle in opposition to affected person zero infections and zero-day safety occasions!
What’s extra, Phylum found three extra packages – known as pycolured, pycolurate, and colurful – which were used to ship a Go-based distant entry trojan known as Spark.
Adding to the assaults focusing on PyPI, the software program provide chain safety agency additionally revealed particulars of an enormous assault marketing campaign whereby unknown menace actors revealed as many as 1,138 packages to deploy a Rust executable, which is then used to drop further malware binaries.
“The threat/reward proposition for attackers is effectively definitely worth the comparatively minuscule effort and time, if they’ll land a whale with a fats crypto pockets,” the Phylum analysis staff mentioned.
“And the loss of some bitcoin pales compared to the potential injury of the lack of a developer’s SSH keys in a big enterprise reminiscent of a company or authorities.”