[ad_1]
The operators of the Ducktail info stealer have demonstrated a “relentless willingness to persist” and continued to replace their malware as a part of an ongoing financially pushed marketing campaign.
“The malware is designed to steal browser cookies and make the most of authenticated Facebook periods to steal info from the sufferer’s Facebook account,” WithSecure researcher Mohammad Kazem Hassan Nejad stated in a brand new evaluation.
“The operation finally hijacks Facebook Business accounts to which the sufferer has adequate entry. The risk actor makes use of their gained entry to run advertisements for financial achieve.”
Attributed to a Vietnamese risk actor, the Ducktail marketing campaign is designed to focus on companies within the digital advertising and promoting sectors that are lively on the Facebook Ads and Business platform.
Also focused are people inside potential firms which can be prone to have high-level entry to Facebook Business accounts. This consists of advertising, media, and human sources personnel.
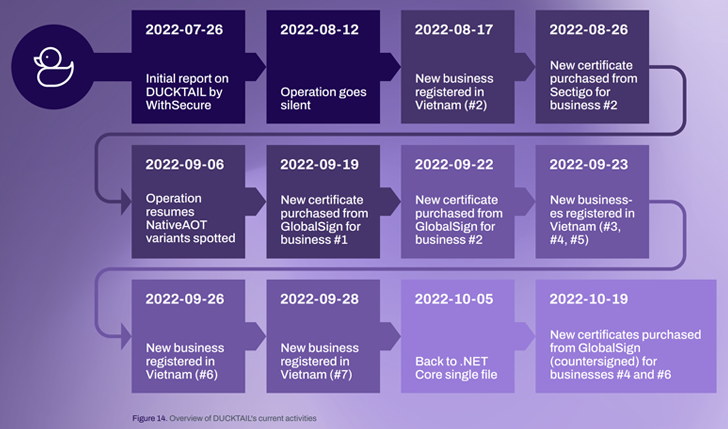
The malicious exercise was first documented by the Finnish cybersecurity firm in July 2022. The operation is believed to be underway because the second half of 2021, though proof factors to the risk actor being lively way back to late 2018.
A subsequent evaluation by Zscaler ThreatLabz final month uncovered a PHP model of the malware distributed as installers for cracked software program. WithSecure, nonetheless, stated the exercise has no connection in any way to the marketing campaign it tracks beneath the Ducktail moniker.
The newest iteration of the malware, which resurfaced on September 6, 2022, after the risk actor was compelled to halt its operations on August 12 in response to public disclosure, comes with a bunch of enhancements integrated to avoid detection.
Infection chains now start with the supply of archive recordsdata containing spreadsheet paperwork hosted on Apple iCloud and Discord by platforms like LinkedIn and WhatsApp, indicating diversification of the risk actor’s spear-phishing techniques.
The Facebook Business account info collected by the malware, which is signed utilizing digital certificates obtained beneath the guise of seven totally different non-existent companies, is exfiltrated utilizing Telegram.
“An attention-grabbing shift that was noticed with the newest marketing campaign is that [the Telegram command-and-control] channels now embody a number of administrator accounts, indicating that the adversary could also be operating an associates program,” Nejad defined.
[ad_2]