[ad_1]
Cybercriminals impersonate the trusted e-signature model and ship faux Docusign notifications to trick folks into gifting away their private or company knowledge
27 May 2025
•
,
5 min. learn

Remember once you used to should print, signal, scan, electronic mail and/and even fax each time you needed to signal and ship an official doc? Today, a lot of the onerous work is completed behind the scenes by cloud app suppliers like Docusign.
But like all tech manufacturers, as soon as it has reached a crucial mass of customers, cybercriminals will search for methods to abuse it for their very own ends. Docusign claims to have 1.6 million clients around the globe, together with 95% of the Fortune 500, and over one billion customers. That has put it firmly within the crosshairs of risk actors. Read on to know how you can hold your staff protected from Docusign-themed phishing.
How does Docusign phishing work?
Social engineering is among the greatest threats to your enterprise. According to Verizon, phishing is now an preliminary entry vector for 19% of information breaches, whereas a whopping 60% function a “human element.” As a trusted and widely known model, Docusign is a pure alternative for risk actors trying to harvest company logins and doubtlessly monetize assaults in different methods.
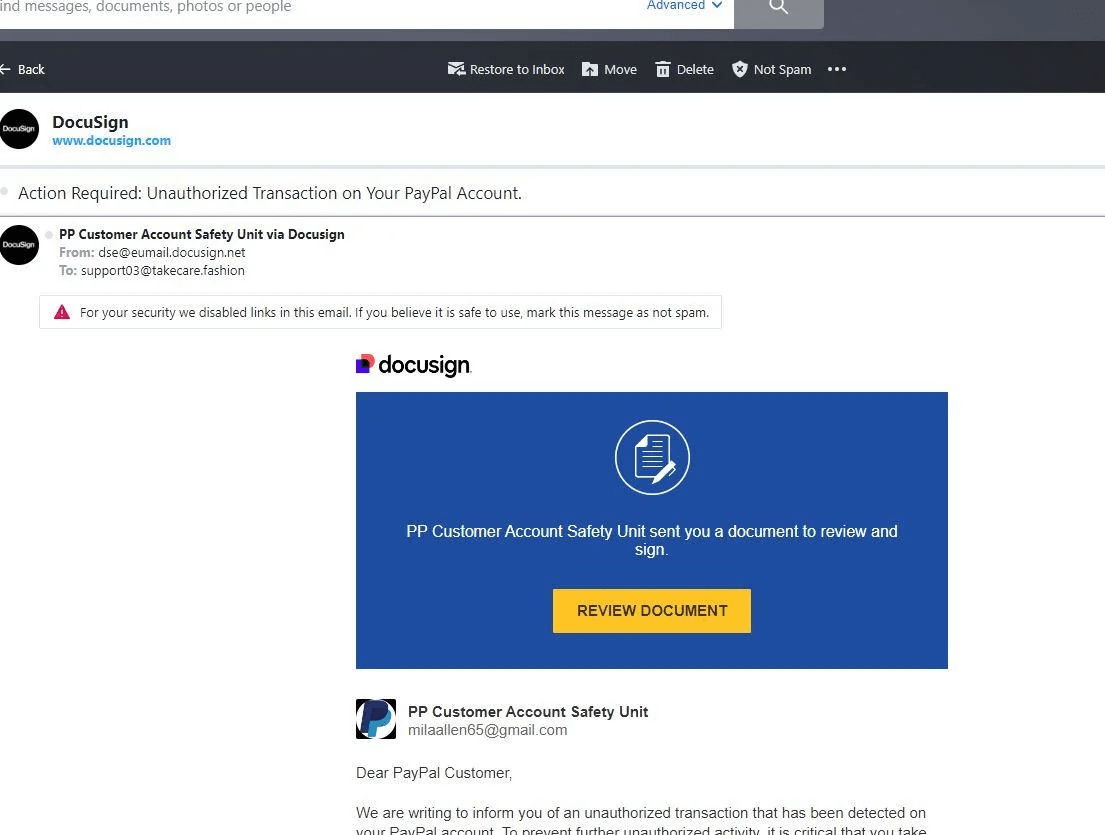
Victims will usually obtain an electronic mail with a spoofed Docusign “envelope” requesting that they click on on a big yellow field to “review document.” There might also be an attachment that includes a QR code. Both actions might result in the identical outcome: the sufferer is taken to a phishing web site equivalent to a faux Microsoft login web page, and requested to enter private and/or monetary info.
QR codes are additionally well-liked as they require the person to scan with their cellular system, which can not have safety software program put in to stop them from being taken to a malicious web page. Either approach, a focused phishing assault like this might additionally allow risk actors to achieve an important foothold in company networks, in addition to for privilege escalation, lateral motion and knowledge exfiltration/ransomware.
Some examples
Over the previous few months, incidents have emerged of:
- “Legitimate” Docusign envelopes that spoof invoices from suppliers, in a bid to trick corporations into transferring cash.
- Fake bill scams impersonating US state and municipal companies and designed to trick suppliers into wiring cash.
- Cybercriminals will not be spoofing faux Docusign emails, however as an alternative registering actual accounts with the corporate, and utilizing its APIs to ship out professional envelopes spoofing well-liked manufacturers.
- Regular phishing emails spoofing the Docusign model and taking the person to phishing login pages. These might mimic company HR and payroll departments, and even exterior entities like municipal authorities.
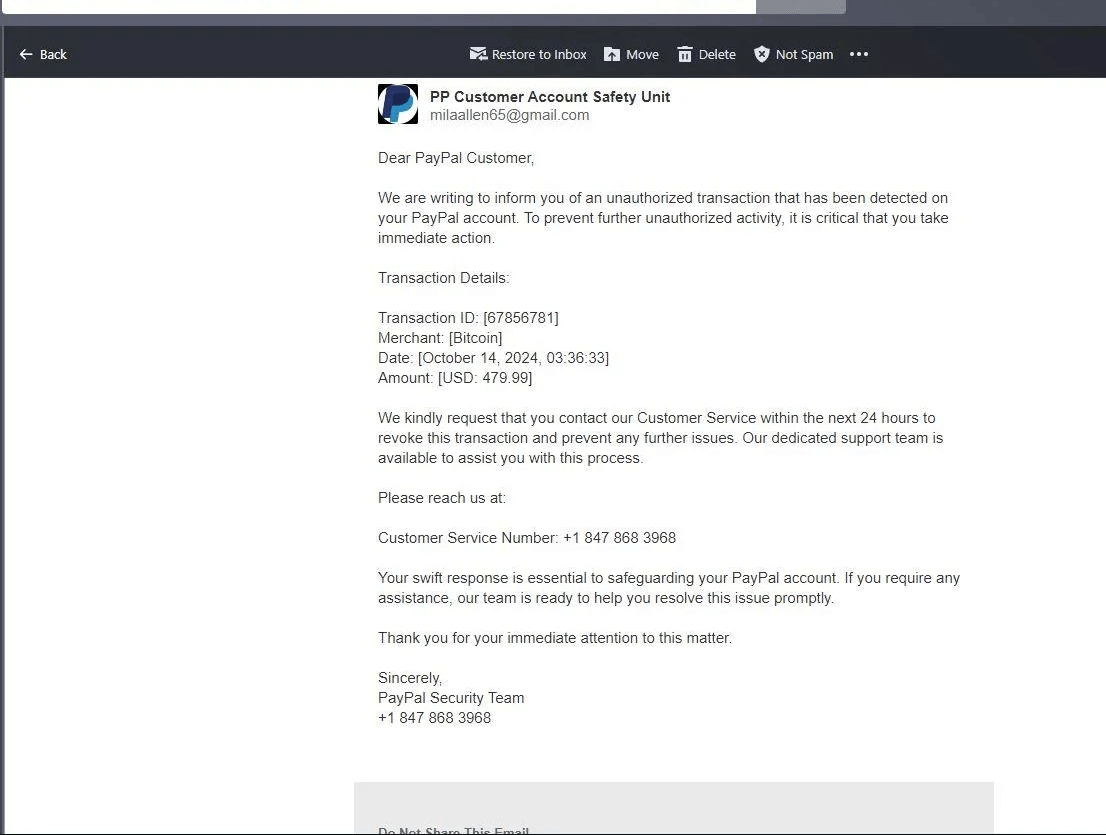
- Refund scams which cite a faux transaction and attempt to drive the sufferer into calling a quantity in the event that they need to cancel it. Once on the telephone, they’ll be persuaded at hand over their private/monetary/card particulars to say the ‘refund’.
Example of a rip-off abusing folks’s belief in Docusign for knowledge theft (Source: Reddit)
Staying protected
Fortunately, there’s loads you are able to do to maintain your self and your organization protected from Docusign threats. From an organization’s perspective, the primary plan of action is to concentrate on the dangers and replace your phishing consciousness packages to make sure workers are capable of spot the warning indicators of a rip-off electronic mail. Simulation instruments needs to be customizable sufficient to assist this.
Things staff needs to be taught to look out for embrace:
- Destination URLs: hover over any hyperlinks/buttons in Docusign emails to test the vacation spot URLs are professional.
- Security codes: these ought to function on any professional Docusign electronic mail (within the “alternate sign in method” part) and permit the person to entry a doc instantly on the Docusign web site slightly than observe hyperlinks in an electronic mail.
- Attachments: there needs to be no attachments in an preliminary Docusign electronic mail. Only as soon as a doc has been signed will you obtain a completed model of it by way of attachment.
- Spelling, grammatical and tonal errors: are one other tell-tale signal of a phishing electronic mail.
- An electronic mail signature and sender identify/electronic mail handle that don’t match.
Layer up defenses on high of the safety consciousness piece by together with issues like:
- Multi-factor authentication (MFA) for all company accounts, which can make it tougher for hackers to entry your knowledge, even when they do handle to steal your logins.
- Password hygiene, together with use of sturdy, distinctive passwords for every account, saved in a password supervisor.
- A multi-layered safety device from a good vendor like ESET, which, amongst different issues, detects malicious attachments, prevents customers from following hyperlinks to phishing websites, and allows directors to manually outline electronic mail filtering situations and actions.
- Updated coverage to induce customers to not open attachments or observe hyperlinks in any unsolicited emails, and solely entry Docusign docs by way of the safety code.
- Changing inner enterprise processes relating to fund transfers, in order that any massive sums are topic to additional scrutiny.
- Encouraging customers to report all suspicious Docusign-themed emails to your IT/safety group and to spam@docusign.com.
What to do if you happen to fall sufferer
If the worst occurs and an worker does click on by means of on a Docusign rip-off, you as an admin might want to work by means of a selected set of actions, together with:
- Reset passwords for the impacted person, together with any accounts that they might have reused credentials throughout
- Run a malware scan on the sufferer’s machine to detect and take away any malicious code
- Isolate the system from the community to include the “blast radius” of an assault
- Monitor the darkish net for indicators of data theft/leakage
- Monitor the sufferer’s accounts for uncommon exercise
- Dig deeper with forensics to know what the attacker needed and whether or not they managed to achieve elevated inner entry
- Use the occasion as a studying second for workers: encouraging them to report suspicious emails quickly and to be on their guard on the whole about unsolicited emails
Of course, Docusign isn’t simply utilized by companies. You might need been uncovered to it in a private capability when shopping for a home or finishing tax paperwork. In that case, lots of the ideas above will nonetheless stand you in good stead. Electronic signing apps are an ideal time-saver. But be sure you don’t get caught out by scammers exploiting your belief in these apps.
[ad_2]