[ad_1]
Historically, enterprise organizations haven’t sufficiently monitored their staff’ actions inside inside enterprise functions. They had been primarily (and blindly) trusting their staff. This belief has sadly brought on extreme enterprise injury because of the actions of some malicious insiders.
Monitoring is difficult when current options for detecting malicious actions in enterprise functions are primarily primarily based on guidelines that must be written and maintained individually for every utility. This is as a result of every utility has a bespoke set of actions and log codecs. Rules-based detection options additionally generate many false positives (i.e., false alerts) and false negatives (i.e., malicious actions go undetected).
Detection must be agnostic to the that means of an utility’s actions so it may be utilized to any enterprise utility.
The answer to this problem lies is in analyzing sequences of actions as an alternative of analyzing every exercise by itself. This means we must always analyze consumer journeys (i.e., periods) to watch authenticated customers in enterprise functions. A detection engine learns all typical journeys for every consumer, or cohort, and makes use of them to detect a journey that deviates from typical journeys.
The two primary challenges a detection engine wants to handle are:
- Each utility has a unique set of actions and log format.
- We must precisely study typical consumer journeys in every utility and throughout functions.
Standardizing the Detection Model
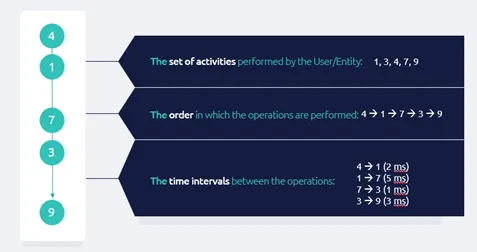
In order to use one detection mannequin to any utility layer log, we are able to extracting from every journey the next three sequence-based options (i.e., traits):
- The set of actions, every denoted by numeric codes.
- The order wherein actions had been carried out within the session.
- Time intervals between actions in the course of the session.
These three traits may be utilized to any utility session, and even to periods throughout functions.
The determine beneath illustrates the three traits of a consumer journey primarily based on 5 actions, every denoted by a quantity, because the exercise is a numeric code from the mannequin’s perspective.
Learning Typical User Journeys Across Apps
As defined above, the detection of irregular journeys relies on studying all typical consumer journeys. Clustering expertise teams comparable information factors to study these consumer journeys and generate a typical consumer journey for every group of comparable journeys. This course of runs constantly as new log information turns into out there.
Once the system learns the journeys typical to the consumer, the detection answer can examine each new journey to see whether or not it’s much like a previously-learned one. If the present journey doesn’t resemble previous periods, the answer flags it as an anomaly. It’s additionally potential to check the present journey in opposition to journeys related to the cohort the consumer belongs to.
A detection answer have to be primarily based on an especially correct clustering engine tailor-made for sequence clustering, whereas nonetheless remaining virtually linear within the variety of journeys it clusters and never requiring prior data as to what number of clusters to generate. In addition, it has to detect outliers, take away them from the info set to reinforce clustering accuracy, and determine these outliers as anomalies. That’s how the clustering engine that generates teams of comparable consumer journeys may also detect irregular consumer journeys in historic information and report them as anomalies.
