[ad_1]
Remote entry trojans resembling StrRAT and Ratty are being distributed as a mixture of polyglot and malicious Java archive (JAR) information, as soon as once more highlighting how menace actors are constantly discovering new methods to fly beneath the radar.
“Attackers now use the polyglot approach to confuse safety options that do not correctly validate the JAR file format,” Deep Instinct safety researcher Simon Kenin mentioned in a report.
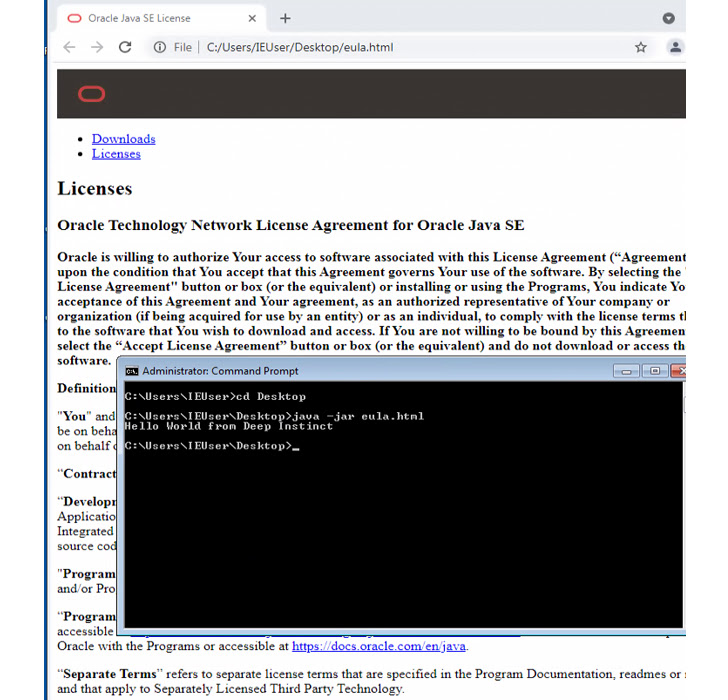
Polyglot information are information that mix syntax from two or extra totally different codecs in a way such that every format might be parsed with out elevating any error.
One such 2022 marketing campaign noticed by the cybersecurity agency is using JAR and MSI codecs – i.e., a file that is legitimate each as a JAR and an MSI installer – to deploy the StrRAT payload. This additionally implies that the file might be executed by each Windows and Java Runtime Environment (JRE) primarily based on the way it’s interpreted.
Another occasion includes using CAB and JAR polyglots to ship each Ratty and StrRAT. The artifacts are propagated utilizing URL shortening providers resembling cutt.ly and rebrand.ly, with a few of them hosted on Discord.
“What’s particular about ZIP information is that they are recognized by the presence of an finish of central listing report which is situated on the finish of the archive,” Kenin defined. “This implies that any ‘junk’ we append at first of the file might be ignored and the archive continues to be legitimate.”
The lack of enough validation of the JAR information ends in a situation the place malicious appended content material can bypass safety software program and keep undetected till they’re executed on the compromised hosts.
This shouldn’t be the primary time such malware-laced polyglots have been detected within the wild. In November 2022, Berlin-based DCSO CyTec unearthed an data stealer dubbed StrelaStealer that is unfold as a DLL/HTML polyglot.
“The correct detection for JAR information needs to be each static and dynamic,” Kenin mentioned. “It’s inefficient to scan each file for the presence of an finish of central listing report on the finish of the file.”
“Defenders ought to monitor each ‘java’ and ‘javaw’ processes. If such a course of has ‘-jar’ as an argument the filename handed as an argument needs to be handled as a JAR file whatever the file extension or the output of the Linux ‘file’ command.”
[ad_2]