[ad_1]
Learn methods to defend what you are promoting and workers from the MortalKombat ransomware and Laplas Clipper malware.

A brand new assault marketing campaign launched by an unknown risk actor targets the U.S. with two malware households: MortalKombat ransomware and Laplas Clipper. We element how these malware campaigns are executed and methods to maintain what you are promoting protected.
Jump to:
How these cybersecurity assaults are executed
This assault marketing campaign as described by Cisco Talos begins with a phishing e mail (Figure A) that impersonates CoinPayments, a official cryptocurrency cost gateway. The content material may be very temporary, describing a cost in Bitcoin that has been canceled attributable to a time-out drawback. It appears affordable to consider solely individuals making transactions in Bitcoin would open the connected file, which is a ZIP archive file containing a malicious BAT loader script.
Figure A

Once executed, the loader downloads one other ZIP file from a server belonging to the attackers’ infrastructure, whose content material could be MortalKombat ransomware or Laplas Clipper malware (Figure B).
Figure B

What is MortalKombat ransomware?
According to Cisco Talos researcher Chetan Raghuprasad, MortalKombat ransomware was first noticed in January 2023. This 32-bit Windows executable file, as soon as executed, copies itself into the native consumer profile’s non permanent folder earlier than dropping a picture file that will probably be loaded because the victims’ wallpaper (Figure C).
Figure C

The ransomware accommodates an enormous record of file extensions it targets for encryption. Every time there’s a match, the matching file is encrypted. The ransomware additionally checks for logical drives related to the machine it runs on, and searches for a similar file extensions by all folders recursively, encrypting extra information as they’re discovered.
All encrypted information obtain a brand new file extension and the identical ransom word file is created in each folder the place information are encrypted.
Files within the recycle bin folder are having their file identify modified, too, with the identical file extension.
The Cisco Talos researcher discovered similarities between MortalKombat ransomware and a a lot older ransomware dubbed Xorist, which appeared in 2010 and has been broadly used to create ransomware variants. A selected Alcmeter registry key string and a ClassName string X0r157 are markers of the Xorist ransomware and have been discovered within the code of the MortalKombat ransomware. Deeper code evaluation from Talos introduced excessive confidence that the MortalKombat ransomware belongs to the identical household as Xorist.
What is Laplas Clipper malware?
The Laplas Clipper malware model Cisco Talos discovered was developed within the Go programming language, however earlier variations have used different languages together with VB.NET.
The malware embeds encrypted strings which might be decrypted within the preliminary section of execution of the malware. The malware copies itself on the system and establishes persistence earlier than monitoring the customers’ clipboard to search for cryptocurrency pockets addresses. Once a cryptocurrency pockets is detected within the clipboard, it’s changed by an attacker-controlled pockets despatched by the C2 server.
The malware is aware of these cryptocurrencies: Dash, Bitcoin, Bitcoin Cash, Zcash, Litecoin, Ethereum, Binance coin, Dogecoin, Monero, Ripple, Tezos, Ronin, Tron, Cardano and Cosmos.
The malware is marketed on cybercriminals’ underground marketplaces (Figure D) and offered as a service for $59 per 30 days, in keeping with Cyble Research & Intelligence Labs.
Figure D

As a results of the an infection, unsuspecting victims suppose they’re making a cryptocurrency cost with out bother; in truth, they’re being scammed, and their transaction quantity is distributed to an attacker-controlled pockets.
U.S. is the primary goal for this safety risk
The major goal for this assault marketing campaign, as offered by Cisco Talos, is the U.S., adopted by the U.Ok., Turkey and the Philippines (Figure E).
Figure E
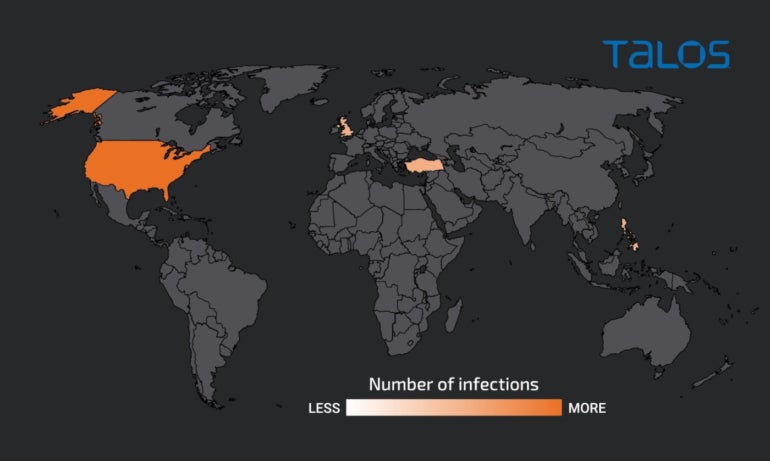
While no intelligence is offered concerning the phishing e mail targets, it’s affordable to consider that the focused emails are most likely from customers coping with cryptocurrency.
How to guard what you are promoting from MortalKombat and Laplas malware
The preliminary an infection depends on social engineering and never vulnerabilities. It is suggested to boost consciousness to all workers by offering them with common safety coaching and tricks to keep away from falling for social engineering-driven infections, particularly through emails.
Plus, all working techniques and software program ought to at all times be updated and patched to stop being compromised by a standard vulnerability and to deploy safety options at each stage of the company infrastructure.
In the case of the Laplas Clipper, because it alters the content material of the clipboard by changing one cryptocurrency pockets for an additional, it’s strongly suggested to at all times test that the consequence from a duplicate/paste operation of a pockets is the very same one because the preliminary one.
Another safety tip is to make common information backups, with backups staying offline, in order that it’s nonetheless attainable to revert to good information when ransomware has hit the infrastructure.
Disclosure: I work for Trend Micro, however the views expressed on this article are mine.
Read subsequent: Security consciousness and coaching coverage (TechRepublic Premium)
[ad_2]
