[ad_1]

A brand new examine Networks discovered that, on common, organizations depend on over 30 instruments for total safety, and that diploma of complexity is making for much less safety, no more.
Over 60% of organizations have been working in a cloud surroundings for 3 or extra years, however technical complexities and sustaining complete safety nonetheless hamper their cloud migration efforts, in accordance with the 2023 State of Cloud-Native Security Report.
SEE: CrowdStrike: Attackers specializing in cloud exploits, knowledge theft (TechRepublic)
Three quarters of respondents to Palo Alto Networks’ survey reported the variety of cloud safety instruments they use creates blind spots that have an effect on their potential to prioritize threat and stop threats. Over three quarters stated they battle to establish what safety instruments are obligatory to realize their targets.
90% of C-Suites respondents stated they might not detect, comprise and resolve cyberthreats inside an hour, and about half conceded {that a} majority of their workforce doesn’t perceive their safety obligations.
Jump to:
Top challenges to offering complete safety, high to backside, left to proper
Respondents to the Palo Alto Networks’ survey named the highest challenges to offering complete safety, which embrace the next:
Managing safety holistically throughout groups
It isn’t sufficient to undertake a accountability mannequin between cloud service suppliers and customers; firms must look inward, and remove silos insofar as they forestall safety processes that work for improvement, operations and safety.
Embedding safety throughout the cloud-native improvement lifecycle
Embedding the appropriate cloud safety options at each stage of the appliance improvement course of from code to runtime is crucial.
Training IT, improvement and safety workers to make use of safety instruments
Cloud-native software improvement requires securing “exponentially more cloud assets across code, workloads, identities, data, etc., and across multiple execution environments, such as containers, serverless, and platforms,” famous the agency.
Lack of visibility into safety vulnerabilities throughout cloud assets
Palo Alto Networks calls vulnerability administration the “holy grail of application security.” But reaching this implies with the ability to mirror the size, pace and agility of the cloud, in accordance with the corporate. Successfully accomplished, it could possibly reward firms with close to real-time detection of threats and vulnerabilities.
Using the appropriate instruments
In the report, the best cloud safety resolution is scalable and in a position to deal with rapid safety wants and extra use instances as the corporate expands cloud functions and makes use of.
C-Suites executives uncertain about safe cloud deployment
The report is predicated on a survey of two,500 C-level executives worldwide in November and December 2022 that tracked enterprises’ shift from on-premise software program and providers to the cloud and located a typically weak safety posture. A typical theme amongst executives surveyed was that their organizations want to enhance visibility into a number of clouds in addition to incident response and investigation.
“With three out of four organizations deploying new or updated code to production weekly, and almost 40% committing new code daily, no one can afford to overlook the security of cloud workloads,” stated Ankur Shah, senior vp, Prisma Cloud, Palo Alto Networks.
“As cloud adoption and expansion continues, organizations need to adopt a platform approach that secures applications from code to cloud across multicloud environments.”
5 keys to best-in-class safety capabilities and ease of use
According to the survey, the highest elements firms take into account when selecting safety options for his or her cloud functions had been:
- Ease of use.
- Best-in-class capabilities.
- Potential affect on enterprise efficiency.
- Familiarity with vendor or device.
- Competitive pricing and/or value.
The survey discovered that enterprises are break up between a single safety vendor/device method and a a number of safety vendor/device method for every of their safety wants.
Companies preserve too many safety arrows of their quivers
Three quarters of the leaders Palo Alto surveyed stated they struggled to establish which safety instruments had been obligatory to realize their targets, which led to deploying quite a few single level safety options — of the 30-plus safety instruments on common that organizations are utilizing, six to 10 are devoted to cloud safety.
SEE: Open supply code for industrial software program functions is ubiquitous, however so is the danger (TechRepublic)
1 / 4 of respondents reported utilizing each in-house and open supply instruments, with many of the firms polled saying they deploy a number of distributors to safe their clouds, networks and functions (Figure A).
Figure A
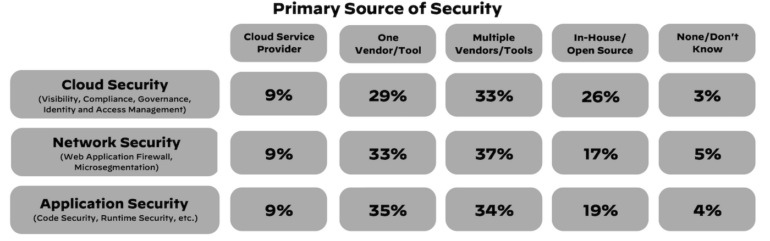
Security gaps persist despite efforts
Palo Alto Networks’ examine reported that solely about 10% of respondents couldn’t detect, comprise and resolve threats in lower than an hour. In addition, 68% of organizations had been unable to even detect a safety incident in lower than an hour, and amongst those who did, 69% couldn’t reply in below an hour (Figure B).
Figure B
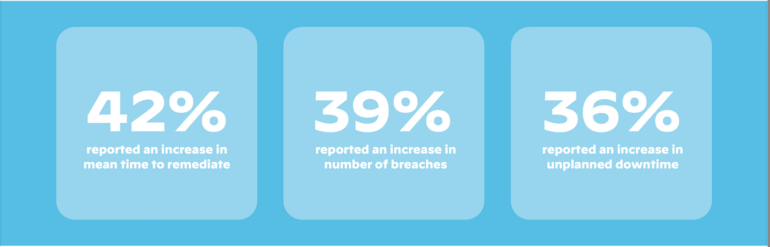
How to keep away from blind spots and poor overview of safety threat
Recommendations from the examine’s authors embrace shortly figuring out anomalous or suspicious behaviors that point out a compromise, and specializing in the means of accelerating near-constant visibility of cloud belongings, partially by eliminating blind spots attributable to the dearth of a holistic method to safety device deployment. The authors additionally instructed:
Incorporate safety in any respect levels
Security groups ought to have a complete understanding of how their firm goes from improvement to manufacturing within the cloud to search out the least disruptive insertion factors for safety instruments.
“Starting by raising visibility and fix-recommendations for software with known vulnerabilities and container image scanning is a great first step towards getting early buy-in from DevOps or platform teams,” the report stated.
Adopt menace prevention strategies
Deployment techniques can actively block zero-day assaults and comprise lateral motion within the occasion of a breach. Also, calculate net-effective permissions throughout cloud assets to make sure finest practices for least-privilege entry.
“At the very least, organizations should consider applying prevention solutions to their mission-critical applications,” stated Palo Alto.
Align cyber techniques with cloud presence
Don’t find yourself with dozens of instruments siloed for particular safety use instances within the cloud, resulting in what Palo Alto Networks calls a “sprawl” of instruments that lavatory down cloud safety groups and go away visibility gaps. The firm suggests reviewing cloud adoption objectives over a two to 5 yr span.
Consolidate instruments the place potential
Unify knowledge and safety controls right into a platform method to acquire a complete view of threat, versus the granular views supplied by a number of siloed instruments.
“By consolidating tools, security teams can automate correlation and tackle the most important security issues across the application lifecycle,” famous the agency.
Acting quick when an incident happens depends upon a robust coverage
Security incidents on computer systems and different units, networks, functions and cloud providers platforms requires a quick response. The sooner one reviews to IT and related safety groups the higher when receiving suspicious messages, noticing uncommon adjustments to system or gadget efficiency, discovering a misdirecting hyperlink or every other suspected assault or infiltration. Download TechRepublic Premium’s Security Incident Response Policy to be taught finest practices for incident response.
