[ad_1]
DevOps platform CircleCI on Wednesday urged its prospects to rotate all their secrets and techniques following an unspecified safety incident.
The firm stated an investigation is at present ongoing, however emphasised that “there are not any unauthorized actors energetic in our programs.” Additional particulars are anticipated to be shared within the coming days.
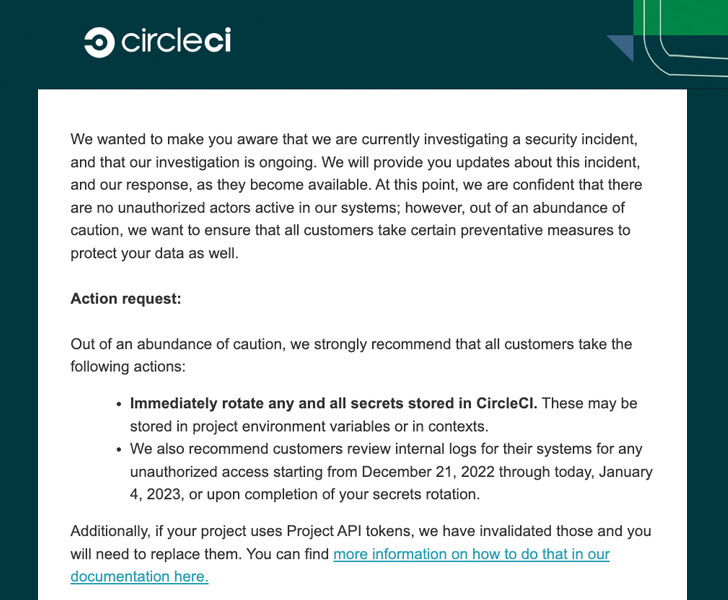
“Immediately rotate any and all secrets and techniques saved in CircleCI,” CircleCI’s chief expertise officer, Rob Zuber, stated in a terse advisory. “These could also be saved in undertaking setting variables or in contexts.”
CircleCI can be recommending customers to evaluate inner logs for indicators of any unauthorized entry ranging from December 21, 2022, to January 4, 2023, or till when the secrets and techniques are rotated.
The software program improvement service didn’t disclose any additional specifics concerning the breach, however stated it has additionally invalidated all Project API tokens and that they should be changed.
The disclosure comes weeks after the corporate introduced that it had launched reliability updates to the service on December 21, 2022, to resolve underlying “systemic points.” CircleCI famous that the 2 occasions should not associated.
It’s additionally the most recent breach to hit CircleCI lately. The firm, in September 2019, revealed “uncommon exercise” associated to a third-party analytics vendor that resulted in unauthorized entry to usernames and e-mail addresses related to GitHub and Bitbucket.
Then final 12 months, it alerted customers that faux CircleCI e-mail notifications have been getting used to steal GitHub credentials and two-factor authentication (2FA) codes.
Slack’s GitHub Code Repositories Stolen
It’s simply not CircleCI, as Slack disclosed on December 31, 2022, that it grew to become conscious of a safety situation that entailed unauthorized entry to a subset of its supply code repositories on GitHub.
The situation, which got here to mild on December 29, 2022, resulted within the theft of a restricted variety of Slack worker tokens that have been then used to entry its GitHub repository, in the end allowing the adversary to obtain the supply code.
Slack, nevertheless, stated no buyer motion is required and that the breach was rapidly contained. The credentials have since been invalidated.
“No downloaded repositories contained buyer information, means to entry buyer information, or Slack’s main codebase,” the Salesforce-owned firm stated. “The menace actor didn’t entry different areas of Slack’s setting, together with the manufacturing setting, and they didn’t entry different Slack assets or buyer information.”
The on the spot messaging service didn’t share extra info on how the worker tokens have been stolen, however harassed the “unauthorized entry didn’t end result from a vulnerability inherent to Slack.”
[ad_2]