[ad_1]

Researchers at Guardio Labs have found a brand new malvertizing marketing campaign pushing Google Chrome extensions that hijack searches and insert affiliate hyperlinks into webpages.
Because all these extensions supply colour customization choices and arrive on the sufferer’s machine with no malicious code to evade detection, the analysts named the marketing campaign “Dormant Colors.”
According to the Guardio report, by mid-October 2022, 30 variants of the browser extensions had been out there on each the Chrome and the Edge internet shops, amassing over one million installs.

(Guardio)
More than hijacking
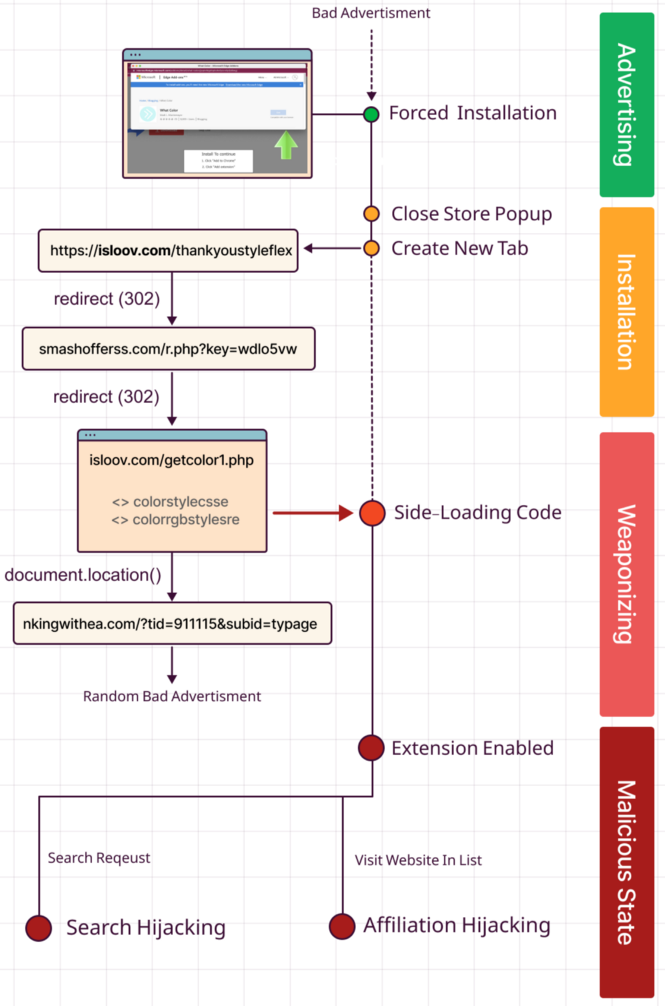
The an infection begins with ads or redirects when visiting internet pages that provide a video or obtain.
However, when making an attempt to obtain this system or watch the video, you might be redirected to a different website stating you will need to set up an extension to proceed, as demonstrated beneath.
When the customer clicks on the ‘OK’ or ‘Continue’ button, they’re then prompted to put in an innocuous-looking color-changing extension.
However, when these extensions are first put in, they may redirect customers to varied pages that side-load malicious scripts that instruct the extension on the best way to carry out search hijacking and on what websites to insert affiliate hyperlinks.
“The first one dynamically creates parts on the web page whereas attempting desperately to obfuscate the JavaScript API calls,” explains the Guardio report.
“Both of these HTML parts (colorstylecsse and colorrgbstylesre) embrace content material (InnerText) that for the primary is a ‘#’ separated listing of strings and regexes and the final is a comma-separated listing of 10k+ domains.”
“To end it up, it additionally assigns a brand new URL to the situation object so you might be redirected to the commercial that finalizes this move as it’s was simply one other commercial popup.”
(Guardia)
When performing search hijacking, the extension will redirect search queries to return outcomes from websites affiliated with the extension’s developer, thus producing revenue from advert impressions and the sale of search information.
Dormant Colors goes past this by additionally hijacking the sufferer’s searching on an in depth listing of 10,000 web sites by mechanically redirecting customers to the identical web page however this time with affiliate hyperlinks appended to the URL.
Once the affiliate tags are appended to the URL, any buy made on the location will generate a fee for the builders.
Guardio has additionally shared a video demonstrating the affiliation hijacking part, proven beneath.
Potential for extra
The researchers warn that utilizing the identical stealthy malicious code side-loading method, the operators of Dormant Colors might obtain doubtlessly nastier issues than hijacking affiliations.
The researchers say it’s potential to redirect victims to phishing pages to steal credentials for Microsoft 365, Google Workspace, financial institution websites, or social media platforms.
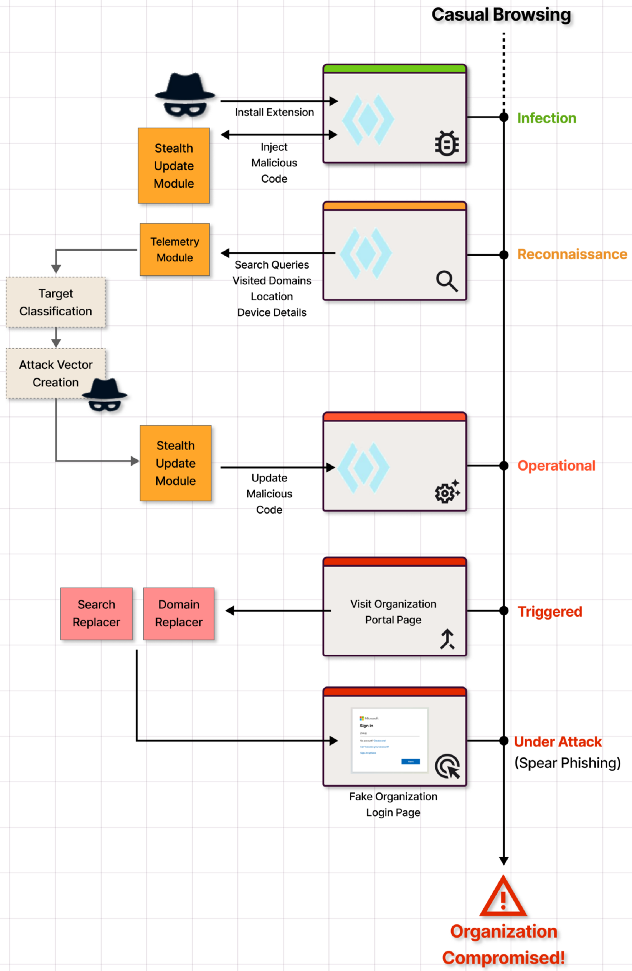
While there are not any indicators that the campaigns are performing this extra malicious conduct, the researchers say it might be enabled just by side-loading further scripts.
The extensions and the web sites listed within the report’s IoCs part have been eliminated/taken offline, however the researchers warn that the operation is consistently renewed with new add-on names and domains.
