[ad_1]

Google researchers mentioned on Wednesday they’ve linked a Barcelona, Spain-based IT firm to the sale of superior software program frameworks that exploit vulnerabilities in Chrome, Firefox, and Windows Defender.
Variston IT payments itself as a supplier of tailored Information safety options, together with expertise for embedded SCADA (supervisory management and information acquisition) and Internet of Things integrators, customized safety patches for proprietary programs, instruments for information discovery, safety coaching, and the event of safe protocols for embedded gadgets. According to a report from Google’s Threat Analysis Group, Variston sells one other product not talked about on its web site: software program frameworks that present every part a buyer must surreptitiously set up malware on gadgets they wish to spy on.
Researchers Clement Lecigne and Benoit Sevens mentioned the exploit frameworks have been used to use n-day vulnerabilities, that are these which were patched just lately sufficient that some targets have not but put in them. Evidence suggests, they added, that the frameworks have been additionally used when the vulnerabilities have been zero-days. The researchers are disclosing their findings in an try and disrupt the marketplace for spyware and adware, which they mentioned is booming and poses a menace to numerous teams.
“TAG’s research underscores that the commercial surveillance industry is thriving and has expanded significantly in recent years, creating risk for Internet users around the globe,” they wrote. “Commercial spyware puts advanced surveillance capabilities in the hands of governments who use them to spy on journalists, human rights activists, political opposition, and dissidents.”
The researchers went on to catalog the frameworks, which they obtained from an nameless supply via Google’s Chrome bug reporting program. Each one got here with directions and an archive containing the supply code. The frameworks got here with the names Heliconia Noise, Heliconia Soft, and Files. The frameworks contained “mature source code capable of deploying exploits for Chrome, Windows Defender, and Firefox” respectively.
Included within the Heliconia Noise framework was code for cleansing up binary recordsdata earlier than they’re produced by the framework to make sure they don’t comprise strings that would incriminate the builders. As the picture of the cleansing script exhibits, the listing of unhealthy strings included “Variston.”
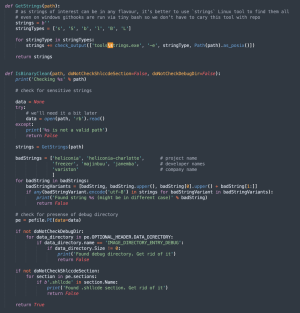
Officials from Variston didn’t reply to an electronic mail searching for remark for this put up.
The frameworks exploited vulnerabilities that Google, Microsoft, and Firefox mounted in 2021 and 2022. Heliconia Noise included each an exploit for the Chrome renderer, together with an exploit for escaping the Chrome safety sandbox, which is designed to maintain untrusted code contained in a protected surroundings that may’t entry delicate elements of an working system. Because the vulnerabilities have been found internally, there aren’t any CVE designations.
Heliconia Noise could possibly be configured by the shopper to set issues like the utmost variety of instances to serve the exploits, an expiration date, and guidelines specifying when a customer must be thought-about a legitimate goal.
Heliconia Soft included a booby-trapped PDF file that exploited CVE-2021-42298, a bug within the JavaScript engine of Microsoft Defender Malware Protection that was mounted in November 2021. Simply sending somebody the doc was sufficient to achieve coveted system privileges on Windows as a result of Windows Defender routinely scanned incoming recordsdata.
The Files framework contained a completely documented exploit chain for Firefox working on Windows and Linux. It exploits CVE-2022-26485, a use-after-free vulnerability that Firefox mounted final March. The researchers mentioned Files possible exploited the code-execution vulnerability since a minimum of 2019, lengthy earlier than it was publicly recognized or patched. It labored in opposition to Firefox variations 64 to 68. The sandbox escape Files relied on was mounted in 2019.
The researchers painted an image of an exploit market that’s more and more uncontrolled. They wrote:
TAG’s analysis has proven the proliferation of business surveillance and the extent to which business spyware and adware distributors have developed capabilities that have been beforehand solely obtainable to governments with deep pockets and technical experience. The progress of the spyware and adware business places customers in danger and makes the Internet much less protected, and whereas surveillance expertise could also be authorized below nationwide or worldwide legal guidelines, they’re usually utilized in dangerous methods to conduct digital espionage in opposition to a spread of teams. These abuses symbolize a severe danger to on-line security which is why Google and TAG will proceed to take motion in opposition to, and publish analysis about, the business spyware and adware business.
Variston joins the ranks of different exploit sellers, together with NSO Group, Hacking Team, Accuvant, and Candiru.
[ad_2]
