[ad_1]
A China-based financially motivated group is leveraging the belief related to standard worldwide manufacturers to orchestrate a large-scale phishing marketing campaign relationship again so far as 2019.
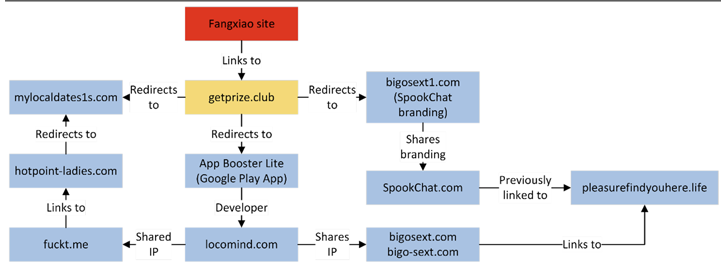
The menace actor, dubbed Fangxiao by Cyjax, is claimed to have registered over 42,000 imposter domains, with preliminary exercise noticed in 2017.
“It targets companies in a number of verticals together with retail, banking, journey, and vitality,” researchers Emily Dennison and Alana Witten stated. “Promised monetary or bodily incentives are used to trick victims into additional spreading the marketing campaign by way of WhatsApp.”
Users clicking on a hyperlink despatched via the messaging app are directed to an actor-controlled web site, which, in flip, sends them to a touchdown area impersonating a widely known model, from the place the victims are as soon as once more taken to websites distributing fraudulent apps and bogus rewards.
These websites immediate the guests to finish a survey to assert money prizes, in alternate for which they’re requested to ahead the message to 5 teams or 20 associates. The closing redirect, nevertheless, hinges on the IP deal with of the sufferer and the browser’s User-Agent string.
More than 400 organizations, together with Emirates, Shopee, Unilever, Indomie, Coca-Cola, McDonald’s, and Knorr, are being imitated as a part of the felony scheme, the researchers stated.
Alternatively, assaults whereby scammy cellular adverts are clicked from an Android machine have been noticed to culminate within the deployment of a cellular trojan known as Triada, which was just lately noticed propagating by way of faux WhatsApp apps.
It’s not simply Triada, as one other vacation spot of the marketing campaign is the Google Play Store itemizing of an app known as “App Booster Lite – RAM Booster” (com.app.booster.lite.phonecleaner.batterysaver.cleanmaster), which has over 10 million downloads.
The app, made by a Czechia-based developer often called LocoMind, is described as a “Powerful Phone Booster,” “Smart Junk Cleaner,” and an “Effective Battery Saver.”
Reviews for the app have known as out the writer for exhibiting too many adverts, and even level out that they “Arrived right here [the Play Store page] from a type of ‘your android is broken x%’ adverts.”
“Our app cannot unfold viruses,” LocoMind responded to the evaluate on October 31, 2022. “Each of our updates is checked by Google Play – they’d have eliminated our app way back for that reason.”
Should the identical motion be carried out from a tool operating iOS, the sufferer is redirected to Amazon by way of an affiliate hyperlink, netting the actor a fee for each buy on the e-commerce platform made in the course of the subsequent 24 hours.
The menace actor’s China connections stem from the presence of Mandarin textual content in an internet service related to aaPanel, a Python-based open supply management panel for internet hosting a number of web sites.
Further evaluation of the TLS certificates issued to the survey domains in 2021 and 2022 reveals {that a} bulk of the registrations overlap with the UTC+08:00 time zone, which corresponds to China Standard Time from 9:00 a.m. to 11:00 p.m.
“The operators are skilled in operating these sorts of imposter campaigns, keen to be dynamic to attain their targets, and technically and logistically able to scaling to increase their enterprise,” the researchers stated.
“The Fangxiao campaigns are efficient lead technology strategies which have been redirected to numerous domains, from malware, to referral hyperlinks, to adverts and adware.”
[ad_2]