[ad_1]
The China-aligned Mustang Panda actor has been noticed utilizing a hitherto unseen customized backdoor known as MQsTTang as a part of an ongoing social engineering marketing campaign that commenced in January 2023.
“Unlike a lot of the group’s malware, MQsTTang would not appear to be based mostly on present households or publicly out there tasks,” ESET researcher Alexandre Côté Cyr mentioned in a brand new report.
Attack chains orchestrated by the group have stepped up focusing on of European entities within the wake of Russia’s full-scale invasion of Ukraine final 12 months. The victimology of the present exercise is unclear, however the Slovak cybersecurity firm mentioned the decoy filenames are in keeping with the group’s earlier campaigns that concentrate on European political organizations.
That mentioned, ESET additionally noticed assaults towards unknown entities in Bulgaria and Australia, in addition to a governmental establishment in Taiwan, indicating deal with Europe and Asia.
Mustang Panda has a historical past of utilizing a distant entry trojan dubbed PlugX for reaching its aims, though latest intrusions have seen the group increasing its malware arsenal to incorporate customized instruments like TONEINS, TONESHELL, and PUBLOAD.
In December 2022, Avast disclosed one other set of assaults aimed toward authorities businesses and political NGOs in Myanmar that led to the exfiltration of delicate knowledge, together with e-mail dumps, recordsdata, courtroom hearings, interrogation reviews, and assembly transcripts, utilizing a PlugX variant known as Hodur and a Google Drive uploader utility.
What’s extra, an FTP server linked to the menace actor has been discovered to host a wide range of beforehand undocumented instruments used to distribute malware to contaminated units, together with a Go-based trojan known as JSX and a classy backdoor known as HT3.
The growth of MQsTTang factors to a continuation of that development, even when it is a “barebones” single-stage backdoor sans any obfuscation methods that permits for executing arbitrary instructions obtained from a distant server.
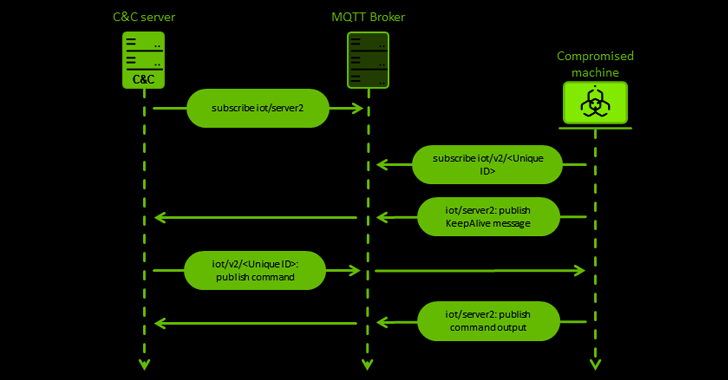
However, an uncommon facet of the implant is using an IoT messaging protocol known as MQTT for command-and-control (C2) communications, which is achieved utilizing an open supply library known as QMQTT, an MQTT shopper for the Qt cross-platform software framework.
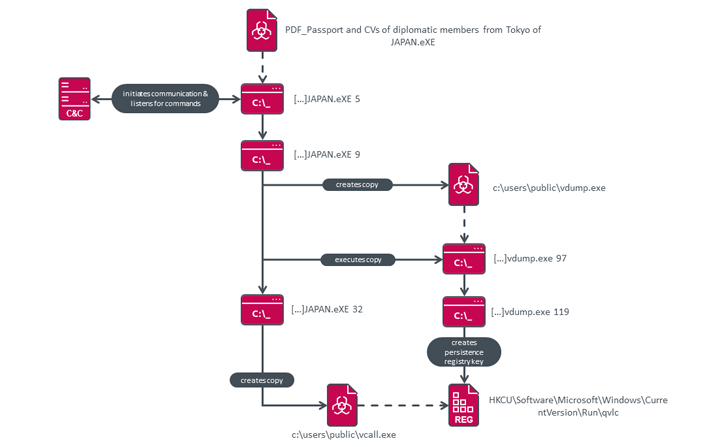
The preliminary intrusion vector for the assaults is spear-phishing, with MQTT distributed by way of RAR archives containing a single executable that options filenames with diplomatic themes (e.g., “PDF_Passport and CVs of diplomatic members from Tokyo of JAPAN.eXE”).
“This new MQsTTang backdoor offers a type of distant shell with none of the bells and whistles related to the group’s different malware households,” Côté Cyr mentioned. “However, it reveals that Mustang Panda is exploring new know-how stacks for its instruments.”