[ad_1]
China-based purveyors of SMS phishing kits are having fun with outstanding success changing phished cost card knowledge into cell wallets from Apple and Google. Until just lately, the so-called “Smishing Triad” primarily impersonated toll highway operators and delivery corporations. But specialists say these teams at the moment are immediately concentrating on prospects of worldwide monetary establishments, whereas dramatically increasing their cybercrime infrastructure and assist employees.

An picture of an iPhone system farm shared on Telegram by one of many Smishing Triad members. Image: Prodaft.
If you personal a cell system, the possibilities are glorious that in some unspecified time in the future previously two years you’ve obtained no less than one on the spot message that warns of a delinquent toll highway payment, or a wayward package deal from the U.S. Postal Service (USPS). Those who click on the promoted hyperlink are delivered to a web site that spoofs the USPS or an area toll highway operator and asks for cost card info.
The website will then complain that the customer’s financial institution must “verify” the transaction by sending a one-time code by way of SMS. In actuality, the financial institution is sending that code to the cell quantity on file for his or her buyer as a result of the fraudsters have simply tried to enroll that sufferer’s card particulars right into a cell pockets.
If the customer provides that one-time code, their cost card is then added to a brand new cell pockets on an Apple or Google system that’s bodily managed by the phishers. The phishing gangs usually load a number of stolen playing cards to digital wallets on a single Apple or Android system, after which promote these telephones in bulk to scammers who use them for fraudulent e-commerce and tap-to-pay transactions.
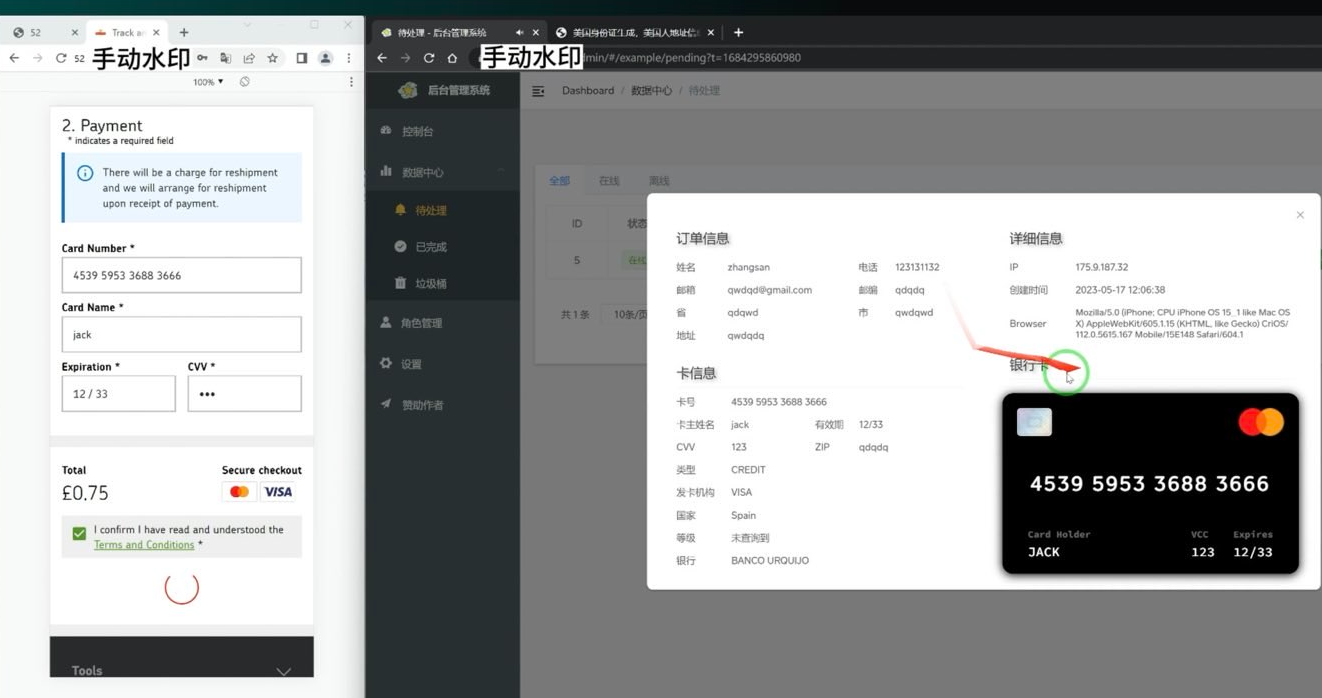
A screenshot of the executive panel for a smishing equipment. On the left is the (take a look at) knowledge entered on the phishing website. On the appropriate we are able to see the phishing equipment has superimposed the provided card quantity onto a picture of a cost card. When the phishing equipment scans that created card picture into Apple or Google Pay, it triggers the sufferer’s financial institution to ship a one-time code. Image: Ford Merrill.
The moniker “Smishing Triad” comes from Resecurity, which was amongst the primary to report in August 2023 on the emergence of three distinct cell phishing teams primarily based in China that appeared to share some infrastructure and modern phishing methods. But it’s a little bit of a misnomer as a result of the phishing lures blasted out by these teams usually are not SMS or textual content messages within the standard sense.
Rather, they’re despatched by way of iMessage to Apple system customers, and by way of RCS on Google Android gadgets. Thus, the missives bypass the cell phone networks solely and revel in close to 100% supply charge (no less than till Apple and Google droop the spammy accounts).
In a report printed on March 24, the Swiss menace intelligence agency Prodaft detailed the fast tempo of innovation coming from the Smishing Triad, which it characterizes as a loosely federated group of Chinese phishing-as-a-service operators with names like Darcula, Lighthouse, and the Xinxin Group.
Prodaft mentioned they’re seeing a major shift within the underground economic system, notably amongst Chinese-speaking menace actors who’ve traditionally operated within the shadows in comparison with their Russian-speaking counterparts.
“Chinese-speaking actors are introducing innovative and cost-effective systems, enabling them to target larger user bases with sophisticated services,” Prodaft wrote. “Their approach marks a new era in underground business practices, emphasizing scalability and efficiency in cybercriminal operations.”
A new report from researchers on the safety agency SilentPush finds the Smishing Triad members have expanded into promoting cell phishing kits concentrating on prospects of world monetary establishments like CitiGroup, MasterCard, PayPal, Stripe, and Visa, in addition to banks in Canada, Latin America, Australia and the broader Asia-Pacific area.

Phishing lures from the Smishing Triad spoofing PayPal. Image: SilentPush.
SilentPush discovered the Smishing Triad now spoofs recognizable manufacturers in quite a lot of business verticals throughout no less than 121 nations and an unlimited variety of industries, together with the postal, logistics, telecommunications, transportation, finance, retail and public sectors.
According to SilentPush, the domains utilized by the Smishing Triad are rotated ceaselessly, with roughly 25,000 phishing domains lively throughout any 8-day interval and a majority of them sitting at two Chinese internet hosting corporations: Tencent (AS132203) and Alibaba (AS45102).
“With nearly two-thirds of all countries in the world targeted by [the] Smishing Triad, it’s safe to say they are essentially targeting every country with modern infrastructure outside of Iran, North Korea, and Russia,” SilentPush wrote. “Our team has observed some potential targeting in Russia (such as domains that mentioned their country codes), but nothing definitive enough to indicate Russia is a persistent target. Interestingly, even though these are Chinese threat actors, we have seen instances of targeting aimed at Macau and Hong Kong, both special administrative regions of China.”
SilentPush’s Zach Edwards mentioned his group discovered a vulnerability that uncovered knowledge from one of many Smishing Triad’s phishing pages, which revealed the variety of visits every website obtained every day throughout 1000’s of phishing domains that had been lively on the time. Based on that knowledge, SilentPush estimates these phishing pages obtained properly greater than one million visits inside a 20-day time span.
The report notes the Smishing Triad boasts it has “300+ front desk staff worldwide” concerned in one in every of their extra common phishing kits — Lighthouse — employees that’s primarily used to assist numerous facets of the group’s fraud and cash-out schemes.
The Smishing Triad members preserve their very own Chinese-language gross sales channels on Telegram, which ceaselessly provide movies and images of their employees laborious at work. Some of these photographs embrace huge partitions of telephones used to ship phishing messages, with human operators seated immediately in entrance of them able to obtain any time-sensitive one-time codes.
As famous in February’s story How Phished Data Turns Into Apple and Google Wallets, a kind of cash-out schemes includes an Android app known as Z-NFC, which might relay a legitimate NFC transaction from one in every of these compromised digital wallets to anyplace on the earth. For a $500 month subscription, the shopper can wave their cellphone at any cost terminal that accepts Apple or Google pay, and the app will relay an NFC transaction over the Internet from a stolen pockets on a cellphone in China.
Chinese nationals had been just lately busted attempting to make use of these NFC apps to purchase high-end electronics in Singapore. And within the United States, authorities in California and Tennessee arrested Chinese nationals accused of utilizing NFC apps to fraudulently buy present playing cards from retailers.
The Prodaft researchers mentioned they had been capable of finding a beforehand undocumented backend administration panel for Lucid, a smishing-as-a-service operation tied to the XinXin Group. The panel included sufferer figures that recommend the smishing campaigns preserve a mean success charge of roughly 5 %, with some domains receiving over 500 visits per week.
“In one observed instance, a single phishing website captured 30 credit card records from 550 victim interactions over a 7-day period,” Prodaft wrote.
Prodaft’s report particulars how the Smishing Triad has achieved such success in sending their spam messages. For instance, one phishing vendor seems to ship out messages utilizing dozens of Android system emulators operating in parallel on a single machine.
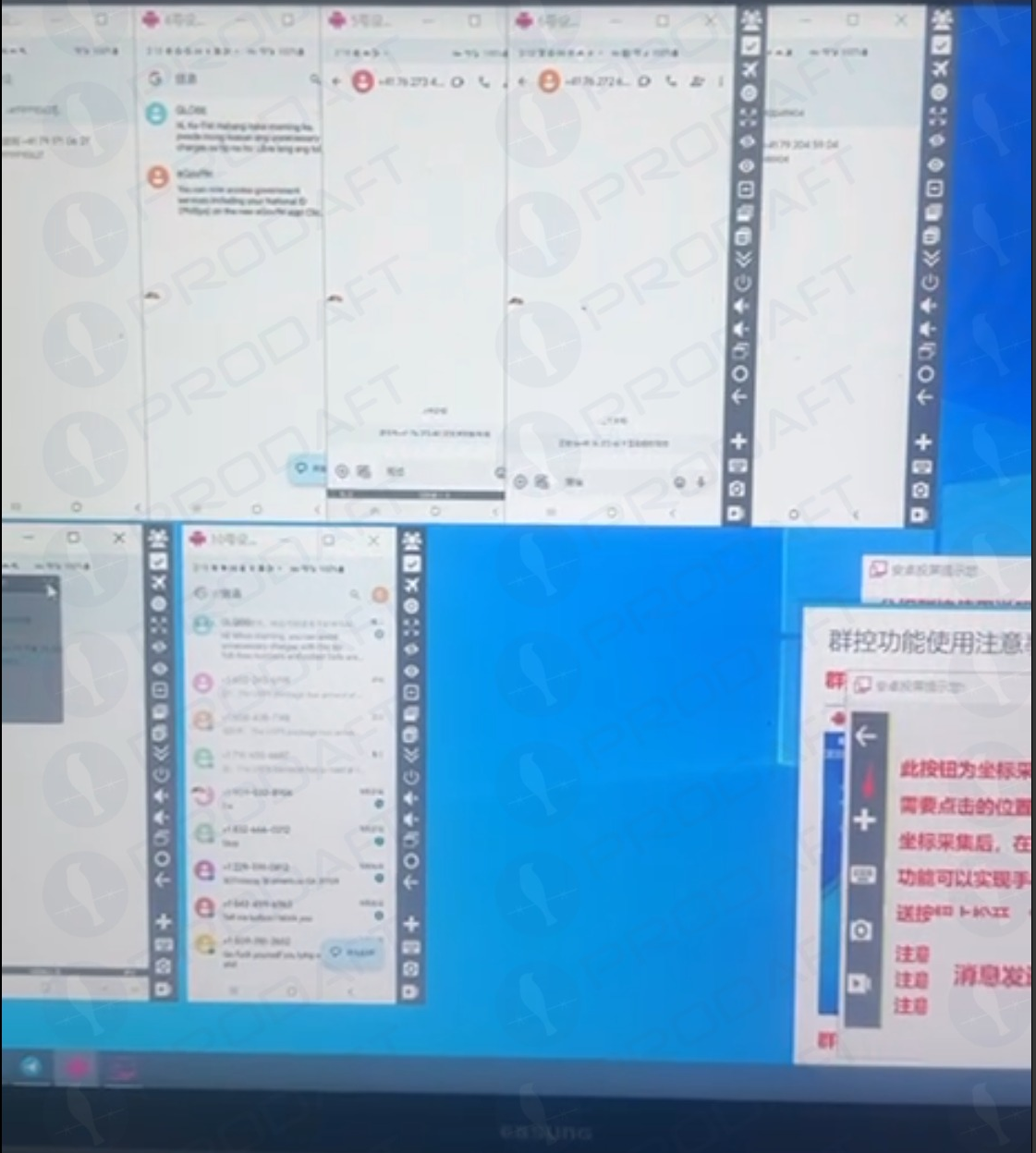
Phishers utilizing a number of virtualized Android gadgets to orchestrate and distribute RCS-based rip-off campaigns. Image: Prodaft.
According to Prodaft, the menace actors first purchase cellphone numbers by means of numerous means together with knowledge breaches, open-source intelligence, or bought lists from underground markets. They then exploit technical gaps in sender ID validation inside each messaging platforms.
“For iMessage, this involves creating temporary Apple IDs with impersonated display names, while RCS exploitation leverages carrier implementation inconsistencies in sender verification,” Prodaft wrote. “Message supply happens by means of automated platforms utilizing VoIP numbers or compromised credentials, usually deployed in exactly timed multi-wave campaigns to maximise effectiveness.
In addition, the phishing hyperlinks embedded in these messages use time-limited single-use URLs that expire or redirect primarily based on system fingerprinting to evade safety evaluation, they discovered.
“The economics strongly favor the attackers, as neither RCS nor iMessage messages incur per-message costs like traditional SMS, enabling high-volume campaigns at minimal operational expense,” Prodaft continued. “The overlap in templates, target pools, and tactics among these platforms underscores a unified threat landscape, with Chinese-speaking actors driving innovation in the underground economy. Their ability to scale operations globally and evasion techniques pose significant challenges to cybersecurity defenses.”
Ford Merrill works in safety analysis at SecAlliance, a CSIS Security Group firm. Merrill mentioned he’s noticed no less than one video of a Windows binary that wraps a Chrome executable and can be utilized to load in goal cellphone numbers and blast messages by way of RCS, iMessage, Amazon, Instagram, Facebook, and WhatsApp.
“The evidence we’ve observed suggests the ability for a single device to send approximately 100 messages per second,” Merrill mentioned. “We also believe that there is capability to source country specific SIM cards in volume that allow them to register different online accounts that require validation with specific country codes, and even make those SIM cards available to the physical devices long-term so that services that rely on checks of the validity of the phone number or SIM card presence on a mobile network are thwarted.”
Experts say this fast-growing wave of card fraud persists as a result of far too many monetary establishments nonetheless default to sending one-time codes by way of SMS for validating card enrollment in cell wallets from Apple or Google. KrebsOnSecurity interviewed a number of safety executives at non-U.S. monetary establishments who spoke on situation of anonymity as a result of they weren’t approved to talk to the press. Those banks have since carried out away with SMS-based one-time codes and at the moment are requiring prospects to log in to the financial institution’s cell app earlier than they will hyperlink their card to a digital pockets.
[ad_2]
