[ad_1]
Security groups usually have nice visibility over most areas, for instance, the company community, endpoints, servers, and cloud infrastructure. They use this visibility to implement the required safety and compliance necessities. However, this isn’t the case in terms of delicate information sitting in manufacturing or analytic databases, information warehouses or information lakes.
Security groups should depend on information groups to find delicate information and implement entry controls and safety insurance policies. This is a large headache for each the safety and information groups. It weakens the enterprise’s safety and compliance placing it liable to exposing delicate information, giant fines, reputational damages, and extra. Also, in lots of instances, it slows down the enterprise’s capacity to scale up information operations.
This article examines how Satori, an information safety platform, provides management of the delicate information in databases, information warehouses and information lakes to the safety groups.
Satori’s automated information safety platform gives a easy and simple solution to meet safety and compliance necessities whereas decreasing threat publicity.
Why is Securing Data Stores Hard?
Security groups haven’t got good visibility and enforcement of insurance policies relating to entry to DBs, information warehouses or information lakes. Take a have a look at an instance.
Nick is a safety engineering supervisor at ACME group. He is chargeable for maintaining with altering safety and compliance rules resembling HIPAA, SOC2, and ISO. This is a troublesome process since safety and compliance rules are all the time altering and evolving. Nick is sweet at his job and may wade via the complexities of the totally different rules and decide the required safety measures to make sure that ACME stays in compliance. This is vital in order that ACME does not fail an audit, expose delicate information, obtain fines or worse.
Then, someday, Nick is instantly tasked with assembly safety and compliance necessities throughout all of ACME’s analytic and manufacturing information.
Nick faces an issue. Although he has achieved his job and decided the required steps to make sure safety and compliance it is vitally troublesome to really perform these steps and implement the safety insurance policies. There are a number of the explanation why Nick’s job is troublesome and irritating which might be explored in additional element under.
Visibility Over Sensitive Data and Logs
Nick’s lack of visibility limits his capacity to implement and handle safety insurance policies and compliance necessities. Three important sources impede his visibility.
1 — Different logs from totally different sources are “buried.”
Since ACME has delicate information unfold throughout a number of databases, information lakes and information warehouses; there are all kinds of audit logs from all of those totally different sources. Furthermore, Nick has to correlate the log information with recognized areas of delicate information (if he has them).
2 — Changes to the configuration and processes to allow visibility.
It is vital to make sure that all delicate information entry is precisely monitored. Nick might wish to look at why a person was accessing delicate info in a area exterior their service space and forestall this sort of entry from occurring sooner or later. He wants to vary the configuration and ensure that the change management processes are efficient. However, this isn’t so simple as it appears. The lack of visibility signifies that Nick can’t confirm that these modifications are made in real-time.
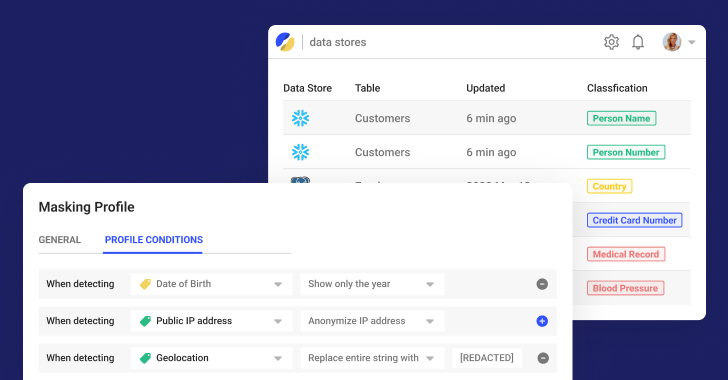
3 — Knowing the kind and site of delicate information.
Nick does not have the power to repeatedly hunt down delicate information. His lack of visibility coupled with the truth that he’s not the proprietor of those information shops means that he’s not capable of search the a number of information shops for delicate information. Instead, he has to depend on the engineering workforce.
The majority of corporations use handbook processes to scan and uncover delicate information. The handbook scanning of knowledge, when Nick can get the information engineers to cease their tasks and undertake this process, is sluggish and error-prone. This signifies that Nick is commonly anxious about getting the information engineers to repeatedly scan the information to seek out delicate info and identification info.
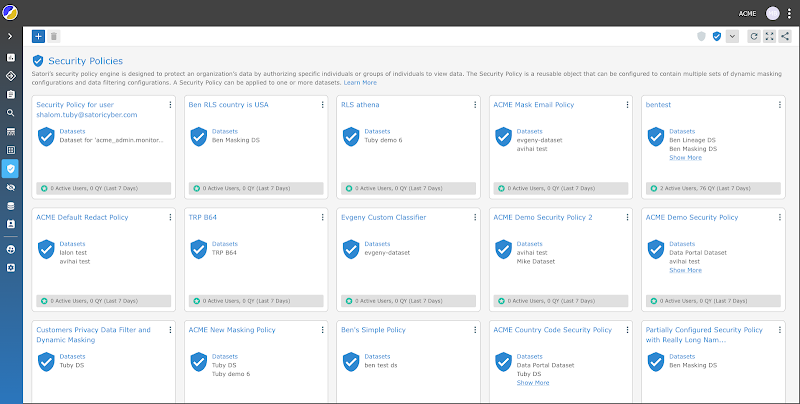
Enforcement of Security Policies
ACME has delicate information that’s unfold throughout quite a lot of various databases, information lakes and information warehouses. Nick is an excellent safety engineer however it’s unlikely that he has the data to know SQL and the inside workings of the databases, information warehouses and lakes that comprise the ACME information stack. Since he doesn’t have the power to really code the required modifications to the safety insurance policies he has to depend on the information engineers to hold out his duties.
Even although information engineers usually want to work on their very own tasks as an alternative of implementing Nick’s safety insurance policies, it’s unlikely that they’d permit Nick to implement them himself, even when he knew how. The engineers who personal the information shops most likely don’t need Nick to meddle with issues like creating objects or altering configurations on their information shops. So even when he needed to, and will, it’s unlikely that Nick has the entry to use and implement the required safety insurance policies, as an alternative, he must depend on the information engineers to do that for him.
Using a Data Security Platform
An overview of utilizing Satori’s automated information safety platform, to beat such challenges follows.
Full Visibility
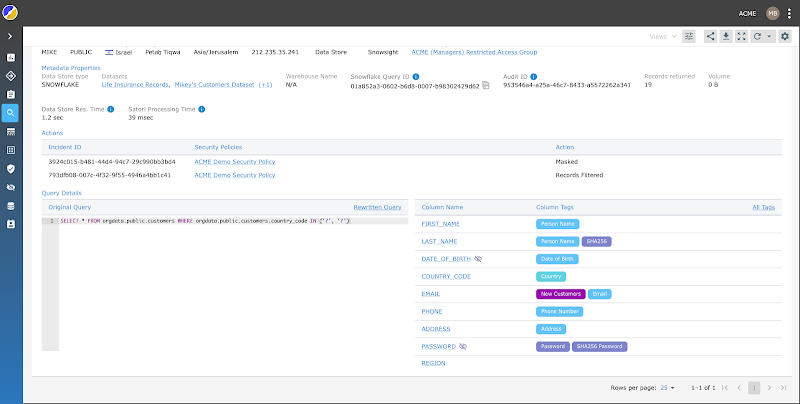
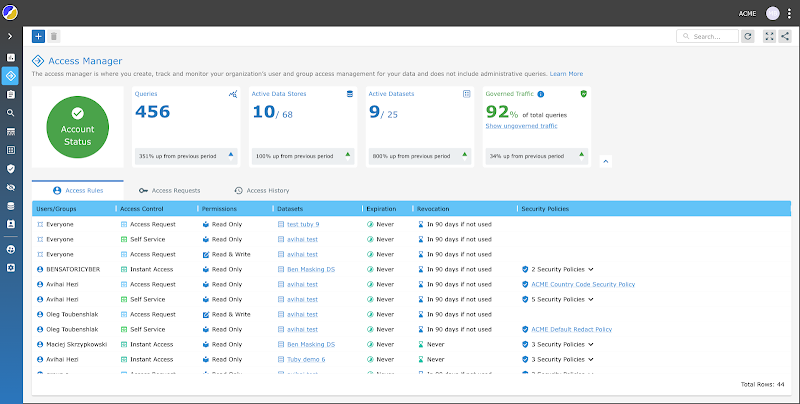
Nick can use Satori’s Access Manager and acquire full visibility over all the carried out safety insurance policies and audit logs from analytics and manufacturing information.
Now Nick can see who accessed which delicate information and when in a single body. He can view all information entry and audit logs throughout all platforms, so delicate information entry is now not “buried”. Nick also can see which safety insurance policies have been utilized and simply replace the safety insurance policies and entry necessities.
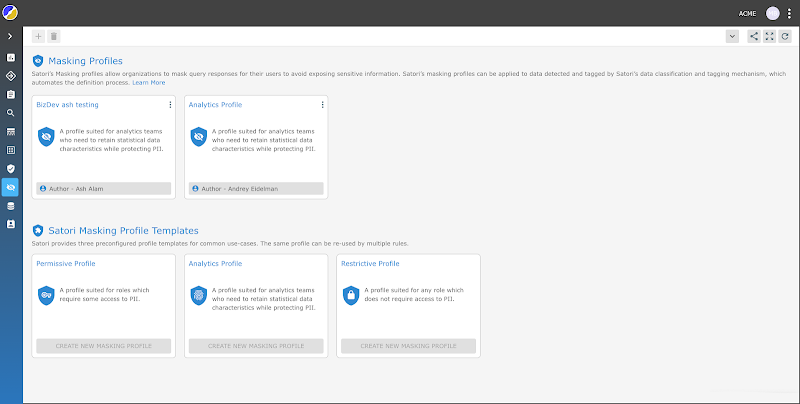
Implementing Security and Compliance Policies
Satori is definitely carried out and may get Nick up and working throughout ACME’s databases, information warehouses and lakes in days or hours as an alternative of months.
This is as a result of Satori doesn’t change something in ACME’s information shops, so there isn’t a further coding essential, or modifications to the information; solely the safety insurance policies and necessities should be utilized.
Check how simple it’s to set and implement safety insurance policies and compliance necessities with Satori and take a take a look at drive.
Fully Automated
Satori automates the method of discovering and classifying delicate information, making use of the relevant safety insurance policies, after which granting and revoking entry controls. The capacity to robotically discover delicate information is invaluable to Nick as a result of he’s not the precise proprietor of the databases, information warehouses or lakes the place the information is saved.
Nick now can management the implementation of safety insurance policies, when rules are up to date, and everyone knows this occurs. He can shortly and simply implement the up to date necessities and scale back the probability of failing an audit or worse.
Nick is completely happy as a result of he can simply implement the required necessities. The information customers are completely happy as a result of utilizing Satori will increase the extent of safety, however does not change or delay their person expertise. As a bonus, the information engineers are additionally completely happy as a result of they do not have to fret about Nick’s nagging to continuously replace and implement safety insurance policies.
Is a Data Security Platform a Good Fit?
Not everybody requires an information safety platform, in some instances, it’s less complicated and simpler to proceed with enterprise as regular. However, if a enterprise has any of the next situations, then an information safety platform is required to safe information.
- Sensitive information
- Multiple information customers
- Multiple databases, information warehouses or information lakes
Satori’s Data Security Platform
Satori’s automated information safety platform helped Nick acquire possession over the information he’s chargeable for. This enabled him to give attention to the safety and compliance elements of his job. Nick can automate all processes from seeking out delicate information to making use of and implementing safety insurance policies. He all the time has full visibility of knowledge entry and may overview the audit and safety logs shortly and simply.
To strive Satori for your self, take a take a look at drive or e-book a demo assembly with Satori.