[ad_1]
A wave of Gootkit malware loader assaults has focused the Australian healthcare sector by leveraging respectable instruments like VLC Media Player.
Gootkit, additionally known as Gootloader, is identified to make use of SEO (web optimization) poisoning ways (aka spamdexing) for preliminary entry. It sometimes works by compromising and abusing respectable infrastructure and seeding these websites with widespread key phrases.
Like different malware of its type, Gootkit is able to stealing information from the browser, performing adversary-in-the-browser (AitB) assaults, keylogging, taking screenshots, and different malicious actions.
Trend Micro’s new findings reveal that the key phrases “hospital,” “well being,” “medical,” and “enterprise settlement” have been paired with varied metropolis names in Australia, marking an malware’s growth past accounting and regulation companies.
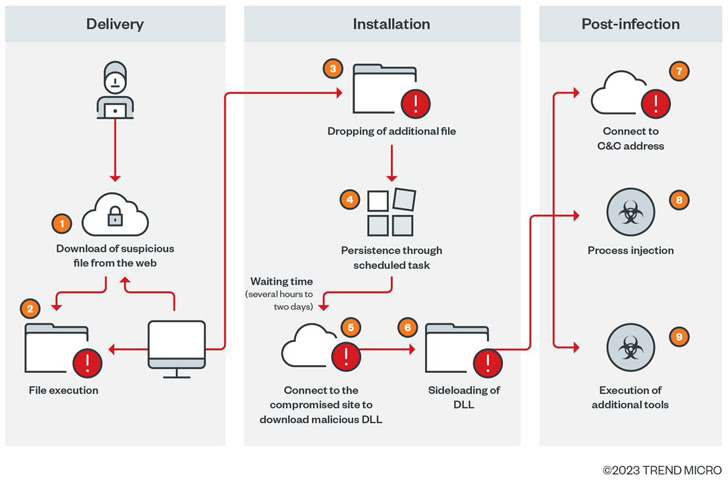
The start line of the cyber assault is to direct customers looking out for a similar key phrases to an contaminated WordPress weblog that methods them into downloading malware-laced ZIP recordsdata.
“Upon accessing the location, the person is introduced with a display that has been made to appear like a respectable discussion board,” Trend Micro researchers mentioned. “Users are led to entry the hyperlink in order that the malicious ZIP file may be downloaded.”
What’s extra, the JavaScript code that is used to tug off this trickery is injected into a sound JavaScript file at random sections on the breached web site.
The downloaded ZIP archive, for its half, additionally accommodates a JavaScript file that, upon execution, not solely employs obfuscation to evade evaluation, however is additional used to ascertain persistence on the machine by the use of a scheduled activity.
The execution chain subsequently results in a PowerShell script that is designed to retrieve recordsdata from a distant server for post-exploitation exercise, which commences solely after a ready interval that ranges from a few hours to so long as two days.
“This latency, which clearly separates the preliminary an infection stage from the second stage, is a particular function of Gootkit loader’s operation,” the researchers mentioned.
Once the wait time elapses, two extra payloads are dropped – msdtc.exe and libvlc.dll – the previous of which is a respectable VLC Media Player binary that is used to load the Cobalt Strike DLL part, adopted by downloading extra instruments to facilitate discovery.
“The malicious actors behind [Gootkit] are actively implementing their marketing campaign,” the researchers mentioned. “The threats concentrating on particular job sectors, industries, and geographic areas have gotten extra aggressive.”
[ad_2]