[ad_1]
Atomic Stealer malware advertises itself via ClearFake browser updates disguised as Google’s Chrome and Apple’s Safari.
Anti-malware software program supplier Malwarebytes has described a brand new variant of Atomic Stealer (often known as AMOS), which is malware concentrating on Apple customers. The new malware variant, distributed via the pretend browser replace supply mechanism ClearFake, advertises itself as updates for Apple’s Safari browser and Google’s Chrome browser. The malware is able to grabbing a person’s information and sending it to an attacker’s command and management server.
Jérôme Segura, senior director of risk intelligence at Malwarebytes, famous in his submit concerning the assault that ClearFake is actively being up to date and that its use of sensible contacts particularly makes it “one of the most prevalent and dangerous social engineering schemes.”
“Fake browser updates have been a common theme for Windows users for years, and yet up until now the threat actors didn’t expand onto MacOS in a consistent way,” Segura identified.
Jump to:
Timeline of Atomic Stealer malware
Atomic Stealer was first marketed as a malware supply possibility for risk actors in April 2023. Malwarebytes present in September 2023 that Atomic Stealer was concentrating on Mac customers via pretend software program updates marketed on Google searches. Atomic Stealer was significantly suited to grabbing passwords and Apple keychain codes used for bitcoin wallets. Atomic Stealer may raise bank card data.
While Atomic Stealer had been concentrating on Mac customers for a while, ClearFake was traditionally used solely in opposition to Windows machines. This is outstanding as a result of ClearFake is without doubt one of the first Windows social campaigns made for Windows that then expanded to not solely a unique geolocation however a unique working system. Security researcher Randy McEoin found ClearFake in August 2023.
Security researcher Ankit Anubhav identified on Nov. 17 that, whereas ClearFake had been seen concentrating on Windows, the Mac model is a brand new improvement.
How ClearFake poses as Safari and Chrome updates
ClearFake is a sequence of malicious web sites that purport to supply updates for Safari (Figure A) and Chrome (Figure B). Potential victims will see websites posing as respectable browser updates.
Figure A
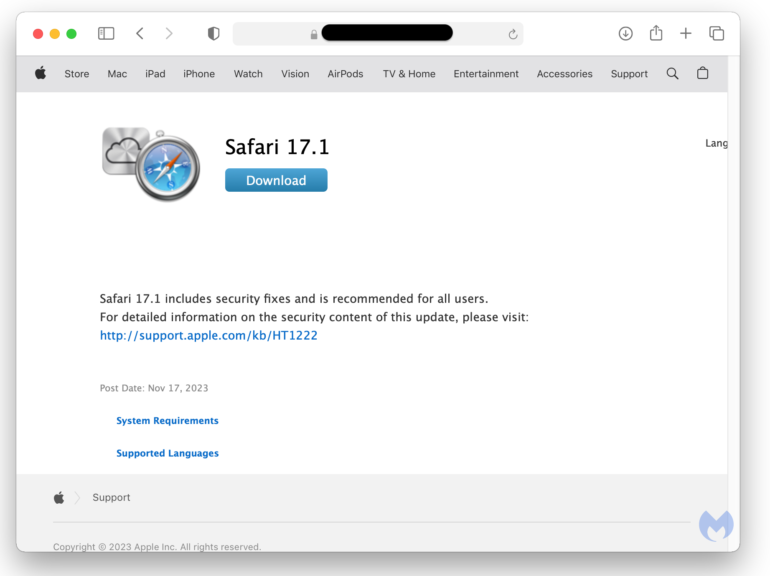
Figure B
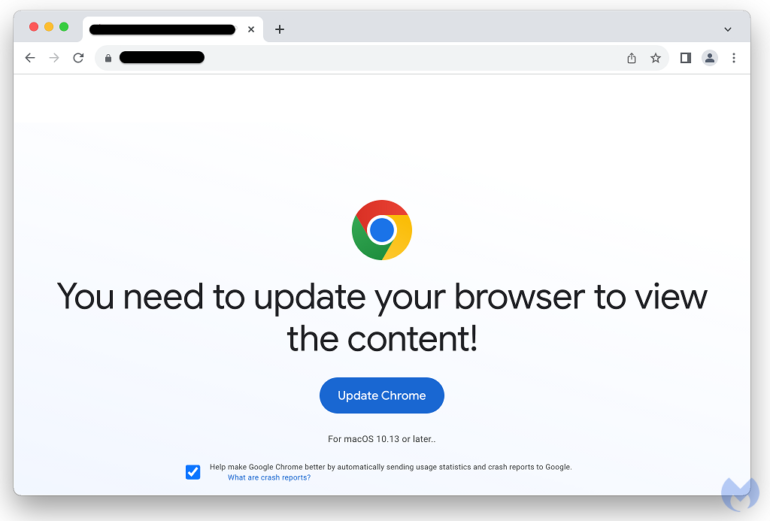
Then, the ClearFake rip-off will ship Atomic Stealer. Victims who click on via to the false updates will obtain a .dmg file that may steal passwords and extract information.
SEE: Some risk actors have used Apple units for surveillance during the last 12 months, and it’s a pattern that will proceed, based on Kaspersky. (TechRepublic)
Malwarebytes discovered that the next malicious domains are related to this risk:
- Longlakeweb [dot] com
- Chalomannoakhali [dot] com
- Jaminzaidad [dot] cm
- Royaltrustrbc [dot] com
The AMOS stealer could be recognized utilizing the next indicators:
- 4cb531bd83a1ebf4061c98f799cdc2922059aff1a49939d427054a556e89f464
- be634e786d5d01b91f46efd63e8d71f79b423bfb2d23459e5060a9532b4dcc7b
How to guard in opposition to this malware risk
Security admins or IT execs ought to preserve the next in thoughts to guard workers from ClearFake and Atomic Stealer:
- Keep your group’s net safety instruments updated.
- Remind workers to not obtain functions from untrusted websites. Mac customers ought to obtain functions solely from the Mac App Store or company-approved areas.
- Communicate clearly about anticipated browser updates and different software updates.
