[ad_1]
An attacker submitting modifications to an open supply repository on GitHub may trigger downstream software program initiatives that embody the most recent model of a part to compile updates with malicious code.
That’s in line with software program provide chain safety agency Legit Security, which stated in an advisory printed on Dec. 1 that this “artifact poisoning” weak spot may have an effect on software program initiatives that use GitHub Actions — a service for automating growth pipelines — by triggering the construct course of when a change is detected in a software program dependency.
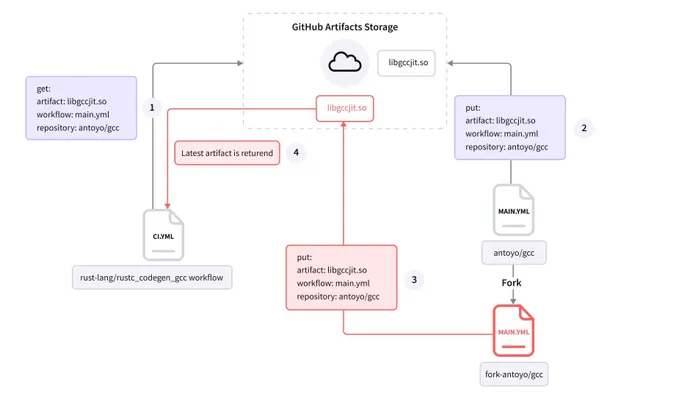
The vulnerability will not be theoretical: Legit Security simulated an assault on the challenge that manages Rust, inflicting the challenge to recompile utilizing a personalized — and malicious — model of the favored GCC software program library, the corporate acknowledged within the advisory.
The drawback probably impacts a lot of open supply initiatives as a result of maintainers usually will run checks on contributed code earlier than they really analyze the code themselves, says Liav Caspi, chief expertise officer of Legit Security.
“It is a typical sample at present,” he says. “A variety of open supply initiatives at present, upon a change request, they run a bunch of checks to validate the request as a result of the maintainer doesn’t wish to need to assessment the code first. Instead, it mechanically run checks.”
The assault takes benefit of the automated construct course of by GitHub Actions. In the case of the Rust programming language, the susceptible sample may have allowed an attacker to execute code in a privileged means as a part of the event pipeline, stealing repository secrets and techniques and probably tampering with code, Legit Security stated.
“To put it merely: in a susceptible workflow, any GitHub consumer can create a fork that builds an artifact,” the corporate acknowledged in its advisory. “Then inject this artifact into the unique repository construct course of and modify its output. This is one other type of a software program provide chain assault, the place the construct output is modified by an attacker.”
The vulnerability allows an assault much like the malware-insertion assault that focused CodeCov and, by that firm’s software program, its downstream prospects.
“[T]he lack of native GitHub implementation for cross-workflow artifacts communication led many initiatives and the GitHub Actions neighborhood to develop insecure options for cross-workflow communication and made this menace extremely prevalent,” Legit Security acknowledged within the advisory.
GitHub confirmed the difficulty and paid a bounty for the knowledge, whereas Rust mounted its susceptible pipeline, Legit Security acknowledged.
Software Supply Chain Needs Security
The vulnerability is the most recent safety situation to have an effect on software program provide chains. Industry and authorities companies have more and more sought to bolster the safety of open supply software program and software program supplied as a service.
In May 2021, for instance, the Biden administration launched its government order on Improving the Nation’s Cybersecurity, a federal rule that, amongst different necessities, mandates that the federal government will require baseline safety requirements for any software program its purchases. On the non-public business facet, Google and Microsoft have pledged billions of {dollars} to shore up safety within the open supply ecosystem, which supplies the code that includes greater than three-quarters of the common software’s codebase.
Logical, But Vulnerable
The safety situation belongs to a hard-to-find class of issues often called logic points, which embody points with permissions, the potential for forked repositories to be inserted right into a pipeline, and a scarcity of differentiation between forked and base repositories.
Because software program initiatives typically use automated scripts to examine code submissions earlier than forwarded them to the maintainers, pull requests will likely be run by automation earlier than any human checks them for malicious code. While the automation saves time, it additionally ought to be thought-about a means for attackers to insert malicious code into the pipeline.
“When you’re doing open supply growth, the issue is greater, since you are accepting contribution from anybody on the earth,” Caspi says. “You are executing issues that you just can’t belief.”
GitHub acknowledged the difficulty and expanded the methods of excluding submissions from exterior collaborators from being mechanically inserted into the Actions pipeline. The firm up to date its GetArtifact and ChecklistArtifacts APIs with the objective of offering extra info to assist decide whether or not an artifact might be trusted.
“Anyone that does something just like the Rust challenge did — trusting the enter from a 3rd get together — then they’re nonetheless susceptible,” Caspi says. “It is a logic drawback. GitHub simply made it simpler to jot down a safer script.”
