[ad_1]
Microsoft’s determination to block Visual Basic for Applications (VBA) macros by default for Office recordsdata downloaded from the web has led many risk actors to improvise their assault chains in current months.
Now in keeping with Cisco Talos, superior persistent risk (APT) actors and commodity malware households alike are more and more utilizing Excel add-in (.XLL) recordsdata as an preliminary intrusion vector.
Weaponized Office paperwork delivered through spear-phishing emails and different social engineering assaults have remained one of many extensively used entry factors for felony teams seeking to execute malicious code.
These paperwork historically immediate the victims to allow macros to view seemingly innocuous content material, solely to activate the execution of malware stealthily within the background.
To counter this misuse, the Windows maker enacted an important change beginning in July 2022 that blocks macros in Office recordsdata connected to e mail messages, successfully severing an important assault vector.
While this blockade solely applies to new variations of Access, Excel, PowerPoint, Visio, and Word, unhealthy actors have been experimenting with alternative an infection routes to deploy malware.
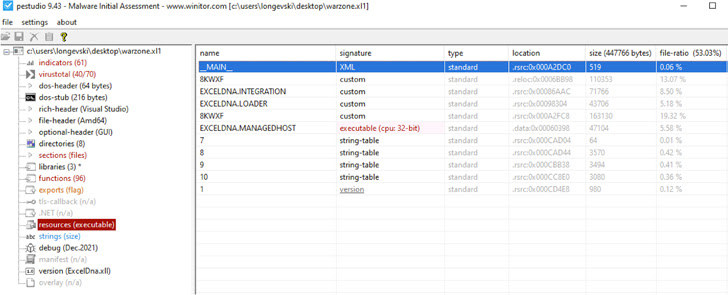
One such technique seems to be XLL recordsdata, which is described by Microsoft as a “kind of dynamic hyperlink library (DLL) file that may solely be opened by Excel.”
“XLL recordsdata might be despatched by e mail, and even with the standard anti-malware scanning measures, customers might be able to open them not understanding that they could comprise malicious code,” Cisco Talos researcher Vanja Svajcer mentioned in an evaluation revealed final week.
The cybersecurity agency mentioned risk actors are using a mixture of native add-ins written in C++ in addition to these developed utilizing a free device known as Excel-DNA, a phenomenon that has witnessed a big spike since mid-2021 and continued to this yr.
That mentioned, the primary publicly documented malicious use of XLL is alleged to have occurred in 2017 when the China-linked APT10 (aka Stone Panda) actor utilized the approach to inject its backdoor payload into reminiscence through course of hollowing.
Other identified adversarial collectives embrace TA410 (an actor with hyperlinks to APT10), DoNot Team, FIN7, in addition to commodity malware households equivalent to Agent Tesla, Arkei, Buer, Dridex, Ducktail, Ekipa RAT, FormBook, IcedID, Vidar Stealer, and Warzone RAT.
The abuse of the XLL file format to distribute Agent Tesla and Dridex was beforehand highlighted by Palo Alto Networks Unit 42, noting that it “could point out a brand new development within the risk panorama.”
“As increasingly more customers undertake new variations of Microsoft Office, it’s doubtless that risk actors will flip away from VBA-based malicious paperwork to different codecs equivalent to XLLs or depend on exploiting newly found vulnerabilities to launch malicious code within the course of house of Office purposes,” Svajcer mentioned.
Malicious Microsoft Publisher macros push Ekipa RAT
Ekipa RAT, apart from incorporating XLL Excel add-ins, has additionally obtained an replace in November 2022 that enables it to benefit from Microsoft Publisher macros to drop the distant entry trojan and steal delicate info.
“Just as with different Microsoft workplace merchandise, like Excel or Word, Publisher recordsdata can comprise macros that can execute upon the opening or closing [of] the file, which makes them fascinating preliminary assault vectors from the risk actor’s standpoint,” Trustwave famous.
It’s value noting that Microsoft’s restrictions to impede macros from executing in recordsdata downloaded from the web doesn’t prolong to Publisher recordsdata, making them a possible avenue for assaults.
“The Ekipa RAT is a superb instance of how risk actors are constantly altering their methods to remain forward of the defenders,” Trustwave researcher Wojciech Cieslak mentioned. “The creators of this malware are monitoring modifications within the safety trade, like blocking macros from the web by Microsoft, and shifting their techniques accordingly.”