[ad_1]
Multiple bugs affecting tens of millions of automobiles from 16 totally different producers could possibly be abused to unlock, begin, and monitor automobiles, plus influence the privateness of automotive house owners.
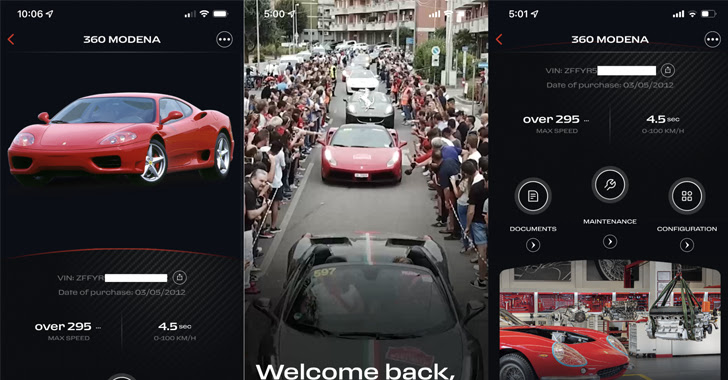
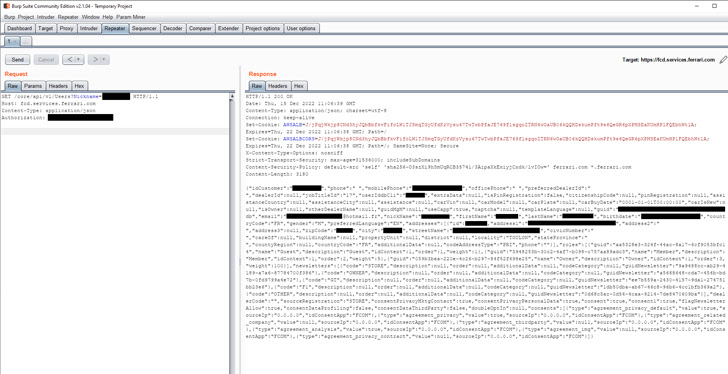
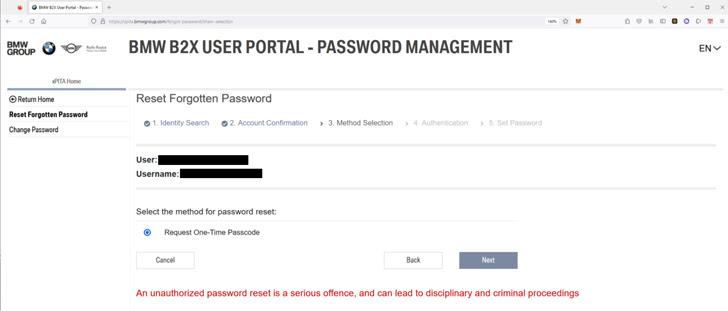
The safety vulnerabilities have been discovered within the automotive APIs powering Acura, BMW, Ferrari, Ford, Genesis, Honda, Hyundai, Infiniti, Jaguar, Kia, Land Rover, Mercedes-Benz, Nissan, Porsche, Rolls Royce, Toyota in addition to in software program from Reviver, SiriusXM, and Spireon.
The flaws run a large gamut, starting from those who give entry to inside firm methods and consumer data to weaknesses that may enable an attacker to remotely ship instructions to realize code execution.
The analysis builds on earlier findings from late final yr, when Yuga Labs researcher Sam Curry et al detailed safety flaws in a linked car service offered by SiriusXM that might doubtlessly put automobiles prone to distant assaults.
The most severe of the problems, which concern Spireon’s telematics resolution, might have been exploited to achieve full administrative entry, enabling an adversary to difficulty arbitrary instructions to about 15.5 million automobiles in addition to replace machine firmware.
“This would’ve allowed us to trace and shut off starters for police, ambulances, and regulation enforcement automobiles for numerous totally different massive cities and dispatch instructions to these automobiles,” the researchers mentioned.
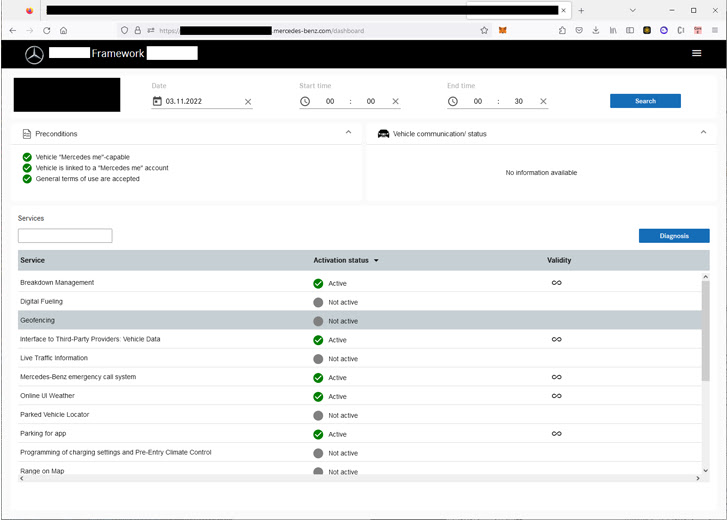
Vulnerabilities recognized in Mercedes-Benz might grant entry to inside functions through an improperly configured single sign-on (SSO) authentication scheme, whereas others might allow consumer account takeover and disclosure of delicate data.
Other flaws make it attainable to entry or modify buyer information, inside vendor portals, monitor car GPS areas in actual time, handle the license plate knowledge for all Reviver prospects, and even replace car standing as “stolen.”
While all the safety vulnerabilities have since been fastened by the respective producers following accountable disclosure, the findings spotlight the necessity for defense-in-depth technique to comprise threats and mitigate threat.
“If an attacker have been capable of finding vulnerabilities within the API endpoints that car telematics methods used, they may honk the horn, flash the lights, remotely monitor, lock/unlock, and begin/cease automobiles, fully remotely,” the researchers famous.
[ad_2]