[ad_1]

Japanese sport developer Ateam has confirmed {that a} easy Google Drive configuration mistake may end up in the potential however unlikely publicity of delicate data for almost a million folks over a interval of six years and eight months.
The Japanese agency is a cellular video games and content material creator, encompassing Ateam Entertainment, which has a number of video games on Google Play like War of Legions, Dark Summoner, Hatsune Miku – Tap Wonder, and instruments like Memory Clear | Game Boost Master, and Good Night’s Sleep Alarm.
Earlier this month, Ateam knowledgeable customers of its apps and providers, workers, and enterprise companions that on November 21, 2023, it found that it had incorrectly set a Google Drive cloud storage occasion to “Anyone on the web with the hyperlink can view” since March 2017.
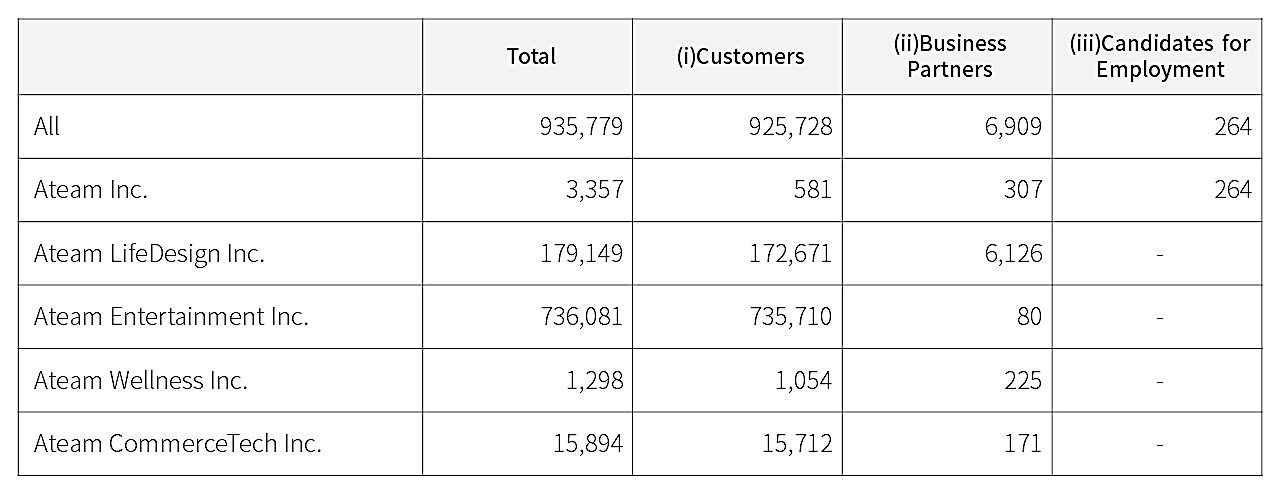
The insecurely configured Google Drive occasion contained 1,369 recordsdata with private data on Ateam clients, Ateam enterprise companions, former and present workers, and even interns and individuals who utilized for a place on the firm.
Ateam has confirmed that 935,779 people had their knowledge uncovered, with 98.9% being clients. For Ateam Entertainment particularly, 735,710 folks have been uncovered.
The knowledge uncovered by this misconfiguration varies relying on the kind of relationship every particular person had with the corporate and will embrace the next:
- Full names
- Email addresses
- Phone numbers
- Customer administration numbers
- Terminal (gadget) identification numbers
The firm says it has seen no concrete proof of risk actors having stolen the uncovered data however urges folks to stay vigilant for unsolicited and suspicious communications.
Secure your cloud providers
Setting Google Drive to “Anyone with the hyperlink can view” makes it viewable solely to these with the precise URL, sometimes reserved for collaboration between folks working with non-sensitive knowledge.
If an worker, or another person with the hyperlink, mistakenly uncovered it publicly, it may get listed by search engines like google and yahoo and grow to be broadly accessible.
While it is unlikely that anybody discovered an uncovered Google Drive URL on their very own, this notification demonstrates a necessity for firms to correctly safe their cloud providers to forestall knowledge from being mistakenly uncovered.
It is quite common for risk actors and researchers to search out uncovered cloud providers, akin to databases and storage buckets, and obtain the info contained in them.
While researchers normally responsibly disclose the uncovered knowledge, if risk actors discover it, it could possibly result in greater issues as they use it to extort firms or promote it to different hackers to make use of in their very own assaults.
In 2017, safety researcher Chris Vickery discovered misconfigured Amazon S3 buckets exposing databases containing 1.8 billion social and discussion board posts made by customers worldwide.
Ten days later, the identical researcher found one other misconfigured S3 bucket that uncovered what seemed to be labeled data from INSCOM.
While these breaches had been responsibly disclosed, different cloud service misconfigurations have led to the info being leaked or bought on hacker boards.
Misconfigured Amazon S3 buckets have grow to be a large enough drawback that researchers have launched instruments that scan for uncovered buckets.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has additionally launched steerage for firms on learn how to correctly safe cloud providers.
[ad_2]
