[ad_1]
In the first weblog of our sequence on Azure Security, we mentioned our method to tackling cloud vulnerabilities. Our second weblog highlighted our use of variant looking to detect patterns and improve safety throughout our providers. The third weblog within the sequence launched game-changing structure to enhance built-in safety. In this installment, we share our built-in response technique which offers a steady studying mannequin, leveraging massive information, to enhance response, detections, preventative controls, and governance to measure and enhance effectiveness.
Azure Security’s “Integrated Response” is the perform of incorporating safety threat mitigation methods right into a sturdy safety program, seamlessly coordinating throughout federated safety capabilities to study, share, and adapt efficient methods to deal with high dangers and threats at hyper-scale. As new threats and safety dangers emerge from a wide range of sources, we deal with them by evaluating root causes and creating safety controls as a studying suggestions system. Our learnings from proactive and reactive evaluation flip into product updates and risk intelligence enhancements in our safety merchandise.
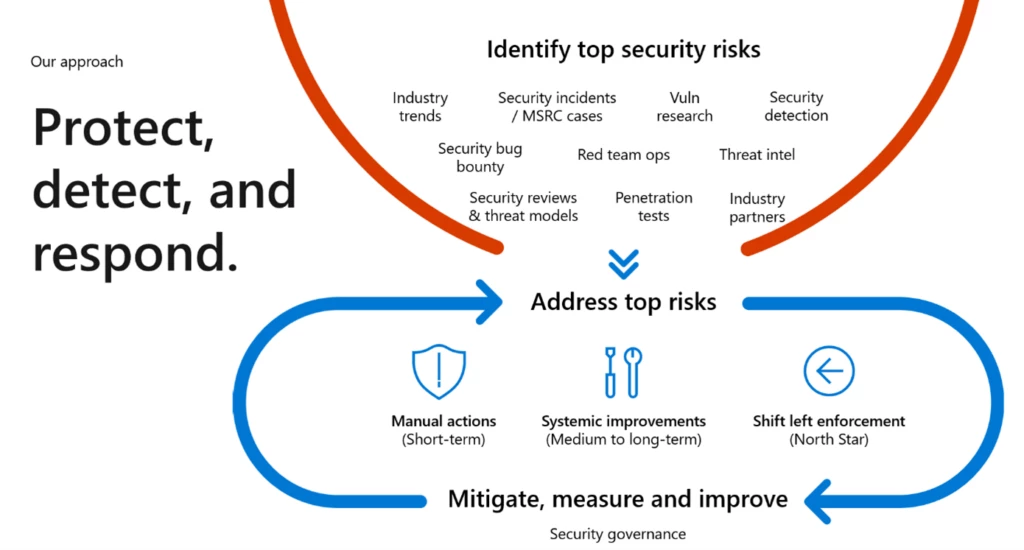
To preserve belief and speed up response timelines, our closed-loop suggestions cycle incorporates each inside and exterior threat drivers to enhance every stage of our safety response pipeline. Regularly reviewing safety incidents is vital to our potential to constantly enhance our agility and response time to mitigate safety dangers for our clients. Each of our institutional processes, such because the Security LiveSite Review (SLR), Security Health Reviews (SHR), and our Security Operation Reviews (SOR) spotlight and prioritize alternatives for enchancment in any respect ranges of Azure’s engineering organizations. Let’s dive into what every of those phases means and the way they join to one another.
Fostering a safe tradition: A deeper take a look at Azure’s rigorous complete safety and response
In a Cloud-First world, our clients belief us with their information, mental property, and demanding enterprise purposes. To meet these expectations, we take a holistic method to manipulate safety and create an Integrated Response which includes a suggestions cycle of figuring out threat drivers and guaranteeing we drive the suitable safety controls to correctly defend, detect and reply to threats. In addition, we guarantee all merchandise meet our safety requirements, equivalent to Microsoft Cloud Security benchmarks. Here are the elements of our Integrated Response:
First response on new threats: Microsoft Security Response Center (MSRC) and Cyber Defense Operations—Operating with an “Assume Breach” mindset, we’ve honed our potential to rapidly and successfully reply to safety incidents and drive speedy safety mitigation and enhancements. We have interaction clients, trade companions, and Microsoft product groups alike to work on this steady suggestions loop. MSRC is an built-in a part of the defender neighborhood working on the entrance line of safety response for our Azure clients and for different merchandise inside Microsoft. For greater than twenty years, MSRC has served to detect, reply, and recuperate from safety vulnerabilities. Our many years of expertise defending a variety of applied sciences have proven us that regularly studying and evolving, each in and out, is important to staying forward of the ever-changing risk panorama.
Learn from each Security Incident: Security Live Site Reviews (SLR)—Following a safety incident originating from MSRC or Red Team Operations, after the speedy remediation exercise concludes, we prioritize conducting SLRs to drive 5-why evaluation with product groups and govt management. Deeply focusing each single week from the Executive VP stage down on deconstructing incidents all the way down to their contributing root trigger(s) drives Microsoft’s methods on figuring out course of gaps, safety management updates, and product enhancements to enhance Azure’s safety posture. As mentioned earlier within the sequence, all through the investigation, we determine further patterns past the particular incident to make sure we deal with past the symptom to the holistic resolution. We monitor these restore objects by all phases of our product and repair growth lifecycle together with operations, engineering workflow, and safety governance processes.
Ensure safety tradition and enhance operational rigor: Security Operations Review (SOR)—To enhance safety for operational hygiene and foster a deep safety tradition, we conduct common SOR. These evaluations deliver collectively govt leaders and product groups to share greatest practices and evaluation behavioral tendencies, safety management efficiency, and reveal a confirmed potential to take care of safety SLAs as a proactive course of.
Understand and scale back holistic safety threat: Security Health and Risk Reviews (SHR)—Understanding the safety threat of assorted necessities are an necessary component to sustaining a correct security-first mindset. We rationalize management efficiency and threat within the mixture to conduct deep dives with product groups, making a joint security-review dialog to study and drive methods to deal with rising threats extra broadly. The SHR offers a deep hyperlink to rising threat by merging Azure Security views with strategic product enhancements to make sure we meet our clients’ wants now and into the long run, offering confidence that we’re investing in groundbreaking safety innovation for tomorrow’s threats.
Govern successfully and drive safety requirements: Azure Security Governance—Always following a development mindset, we drive safety governance at scale throughout greater than six thousand distinctive merchandise, driving safety baseline compliance, guaranteeing our clients have the suitable safety capabilities built-in into our merchandise earlier than launch as documented in Microsoft Cloud Security Benchmark (MCSB), which helps clients guarantee their service configurations of Azure and different clouds meet the safety specification outlined in frameworks such because the Center for Internet Security, the National Institute of Standards and Technology, and the Payment Card Industry. MCSB offers an environment friendly alignment method for purchasers to leverage as controls are pre-mapped to those trade benchmarks.
Internally, this governance perform measures and offers insights and tendencies round behavioral and safety management efficiency throughout our merchandise, integrating new controls in SDL to remain related and mitigating rising dangers, whereas additionally empowering leaders with safety optics to assist them perceive their safety posture and drive security-first tradition inside their groups. We monitor safety key efficiency Indicators (KPIs), at scale, and prioritize controls efficient at mitigating threats based mostly on real-world findings from root trigger evaluation of malicious assaults, RED Team discovery, MSRC findings, and trade incidents. Many are broadly recognized because the trade’s greatest practices and necessities of Microsoft Security Policy (SDL/OSA) in addition to regulatory compliance requirements. These safety KPIs are measured with Microsoft safety applied sciences which have expanded and matured over time.
Embracing continuous studying: How Azure’s Integrated Response technique innovates safety for a altering world
Our Integrated Response technique offers a holistic method to include threat drivers with safety controls and guarantee merchandise meet Microsoft Cloud Security benchmarks, leveraging measurement at scale and governance to determine and mitigate dangers end-to-end. Microsoft combines our sturdy inside safety response program with a broad and various ecosystem of safety companions to provide world-class safety for billions of shoppers and the broader market. We acknowledge that safety is a end result of product and course of and that Defense-in-Depth is a layered method to each. As such, we embrace suggestions and iterate enhancements by measuring for impact. Our many years of expertise defending a variety of applied sciences have proven us that regularly studying and evolving, each in and out, is important to staying forward of the ever-changing risk panorama.
Learn extra
- Read further blogs on this sequence to find out how Azure leverages cloud variant looking, safe multitenancy, Confidential Compute, and Rust to layer safety all through each part of design, growth, and deployment.
[ad_2]
