[ad_1]
Since 2016, OSS-Fuzz has been on the forefront of automated vulnerability discovery for open supply tasks. Vulnerability discovery is a vital a part of holding software program provide chains safe, so our crew is continually working to enhance OSS-Fuzz. For the previous few months, we’ve examined whether or not we may increase OSS-Fuzz’s efficiency utilizing Google’s Large Language Models (LLM).
This weblog submit shares our expertise of efficiently making use of the generative energy of LLMs to enhance the automated vulnerability detection approach often called fuzz testing (“fuzzing”). By utilizing LLMs, we’re in a position to enhance the code protection for vital tasks utilizing our OSS-Fuzz service with out manually writing further code. Using LLMs is a promising new approach to scale safety enhancements throughout the over 1,000 tasks presently fuzzed by OSS-Fuzz and to take away obstacles to future tasks adopting fuzzing.
LLM-aided fuzzing
We created the OSS-Fuzz service to assist open supply builders discover bugs of their code at scale—particularly bugs that point out safety vulnerabilities. After greater than six years of working OSS-Fuzz, we now help over 1,000 open supply tasks with steady fuzzing, freed from cost. As the Heartbleed vulnerability confirmed us, bugs that might be simply discovered with automated fuzzing can have devastating results. For most open supply builders, establishing their very own fuzzing answer may price time and assets. With OSS-Fuzz, builders are in a position to combine their challenge totally free, automated bug discovery at scale.
Since 2016, we’ve discovered and verified a repair for over 10,000 safety vulnerabilities. We additionally imagine that OSS-Fuzz may probably discover much more bugs with elevated code protection. The fuzzing service covers solely round 30% of an open supply challenge’s code on common, which means that a big portion of our customers’ code stays untouched by fuzzing. Recent analysis means that the simplest approach to enhance that is by including further fuzz targets for each challenge—one of many few elements of the fuzzing workflow that isn’t but automated.
When an open supply challenge onboards to OSS-Fuzz, maintainers make an preliminary time funding to combine their tasks into the infrastructure after which add fuzz targets. The fuzz targets are features that use randomized enter to check the focused code. Writing fuzz targets is a project-specific and guide course of that’s much like writing unit checks. The ongoing safety advantages from fuzzing make this preliminary funding of time value it for maintainers, however writing a complete set of fuzz targets is an robust expectation for challenge maintainers, who are sometimes volunteers.
But what if LLMs may write further fuzz targets for maintainers?
“Hey LLM, fuzz this project for me”
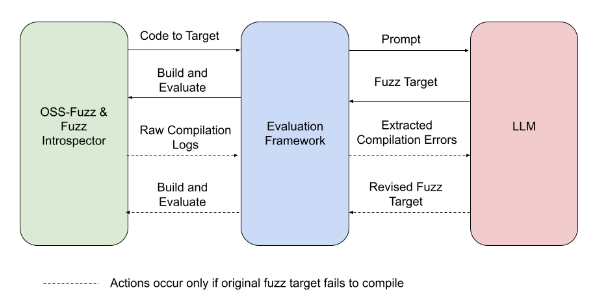
To uncover whether or not an LLM may efficiently write new fuzz targets, we constructed an analysis framework that connects OSS-Fuzz to the LLM, conducts the experiment, and evaluates the outcomes. The steps appear like this:
-
OSS-Fuzz’s Fuzz Introspector software identifies an under-fuzzed, high-potential portion of the pattern challenge’s code and passes the code to the analysis framework.
-
The analysis framework creates a immediate that the LLM will use to put in writing the brand new fuzz goal. The immediate contains project-specific data.
-
The analysis framework takes the fuzz goal generated by the LLM and runs the brand new goal.
-
The analysis framework observes the run for any change in code protection.
-
In the occasion that the fuzz goal fails to compile, the analysis framework prompts the LLM to put in writing a revised fuzz goal that addresses the compilation errors.
Experiment overview: The experiment pictured above is a completely automated course of, from figuring out goal code to evaluating the change in code protection.
At first, the code generated from our prompts wouldn’t compile; nevertheless, after a number of rounds of immediate engineering and making an attempt out the brand new fuzz targets, we noticed tasks achieve between 1.5% and 31% code protection. One of our pattern tasks, tinyxml2, went from 38% line protection to 69% with none interventions from our crew. The case of tinyxml2 taught us: when LLM-generated fuzz targets are added, tinyxml2 has nearly all of its code lined.
Example fuzz targets for tinyxml2: Each of the 5 fuzz targets proven is related to a unique a part of the code and provides to the general protection enchancment.
To replicate tinyxml2’s outcomes manually would have required no less than a day’s value of labor—which might imply a number of years of labor to manually cowl all OSS-Fuzz tasks. Given tinyxml2’s promising outcomes, we need to implement them in manufacturing and to increase related, computerized protection to different OSS-Fuzz tasks.
Additionally, within the OpenSSL challenge, our LLM was in a position to mechanically generate a working goal that rediscovered CVE-2022-3602, which was in an space of code that beforehand didn’t have fuzzing protection. Though this isn’t a brand new vulnerability, it means that as code protection will increase, we are going to discover extra vulnerabilities which are presently missed by fuzzing.
Learn extra about our outcomes via our instance prompts and outputs or via our experiment report.
The objective: totally automated fuzzing
In the following few months, we’ll open supply our analysis framework to permit researchers to check their very own computerized fuzz goal technology. We’ll proceed to optimize our use of LLMs for fuzzing goal technology via extra mannequin finetuning, immediate engineering, and enhancements to our infrastructure. We’re additionally collaborating intently with the Assured OSS crew on this analysis with a purpose to safe much more open supply software program utilized by Google Cloud prospects.
Our long term targets embody:
-
Adding LLM fuzz goal technology as a completely built-in characteristic in OSS-Fuzz, with steady technology of recent targets for OSS-fuzz tasks and 0 guide involvement.
-
Extending help from C/C++ tasks to further language ecosystems, like Python and Java.
-
Automating the method of onboarding a challenge into OSS-Fuzz to remove any want to put in writing even preliminary fuzz targets.
We’re working in the direction of a way forward for customized vulnerability detection with little guide effort from builders. With the addition of LLM generated fuzz targets, OSS-Fuzz may also help enhance open supply safety for everybody.