[ad_1]

The world of cybercrime is shifting rapidly. Threat actors, ransomware gangs, malware builders, and others are more and more and quickly shifting off of the “conventional” darkish net (Tor websites) and onto illicit Telegram channels specializing in cybercrime.
This Flare article will look at the the explanation why risk actors are shifting from Tor and supply detailed steerage for finest practices in monitoring Telegram channels.
Why Are Threat Actors Moving from Tor to Telegram?
Today we see a majority of cybercrime exercise occurring off of the normal darkish net and on fashionable social media functions.
There are a myriad of causes for the change together with the commodification of cybercrime, growing regulation enforcement scrutiny on Tor websites, and the final slowness of Tor. We’ll cowl every in flip.
Lack of Exit Scams
One of the most important upsides and disadvantages to conventional darkish net marketplaces is that {the marketplace} acts as a clearinghouse.
Typically, there’s a 14 day maintain on transactions by which {the marketplace} holds onto cryptocurrency and by which the customer can request recourse if they’re scammed.
The problem turns into that in lots of circumstances market homeowners could also be holding thousands and thousands of {dollars} in crypto at any given time, creating a powerful incentive to exit rip-off and steal the cash being held.
Amenities of Modern Social Media
Compared to Tor websites, Telegram has a bonus in these following areas:
- Telegram is quick, and has most of the facilities that fashionable social media functions have reminiscent of emojis, direct personal chats, a cellphone software, and different good to haves
- Level of technical proficiency to seek out cybercrime channels and efficiently make purchases is even decrease than Tor, making a democratization of cybercrime information
- Many channels exist which give free “samples” of credentials, stealer logs, information from breaches, and different information which may present a simple manner for customers to “validate” the effectiveness of the distributors choices
Perceived Anonymity
It’s no secret that Tor marketplaces, boards, and websites are closely monitored by regulation enforcement organizations. Users know once they make a discussion board put up or market itemizing will probably be seen by enterprise safety groups, dozens of regulation enforcement companies, and plenty of others.
Conversely Telegram offers perceived anonymity given the 1000’s of channels specializing in cybercrime, the dearth of IP monitoring out there to safety and LE professionals, and the seeming ephemeral nature of messages.
Types of Cybercrime Telegram Channels
Compared to legacy darkish net marketplaces, Telegram channels are inclined to focus on one specific kind of legal exercise. A darkish net market could provide a legal the power to purchase medicine, weapons, bank card numbers, combolists and dozens of different illicit items.
Telegram channels by contract act as a single store for a single kind of products and could be categorized based mostly on what they’re providing.
The following classes we’ve recognized will not be exhaustive:
Stealer Log Distribution
Stealer logs signify information from units contaminated with infostealer malware. They sometimes embody the browser fingerprint, saved passwords within the browser, clipboard information, bank card information saved within the browser, cryptocurrency pockets data, and related data.
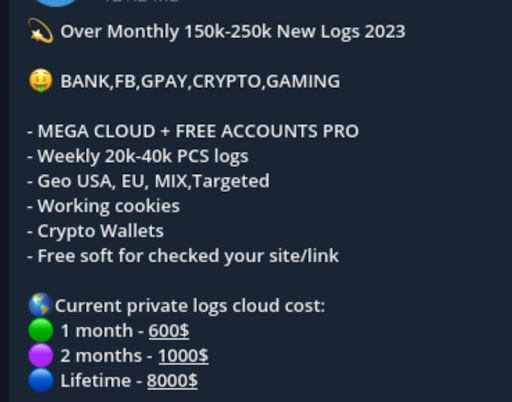
An particular person log ›represents information from one pc. Stealer log channels on Telegram are available in two sorts:
Open Access Stealer Log Channels
These channels routinely distribute megabyte-gigabyte sized recordsdata that comprise a whole bunch, 1000’s, or in some circumstances a whole bunch of 1000’s of particular person stealer logs.
These could be seen as an prolonged commercial for personal, invite solely log channels and as a manner for the distributors to show that the logs they’re offering are high-quality and comprise beneficial credentials.
VIP Stealer Log Channels
VIP stealer logs channels present a restricted variety of risk actors entry to “premium” logs that are supposedly immediately from the supply and untouched by different risk actors. Typically the value for entry to those channels ranges from $200-$400 a month paid in Monero.
We suspect that many preliminary entry brokers sift by way of logs posted in these channels to determine particular logs which have company entry, validate the entry, after which resell the entry on top-tier cybercrime boards reminiscent of Exploit or XSS.
Financial Fraud
Another kind of channel we generally see are monetary fraud channels by which checking account, bank card, and refund data is given out in bulk. These channels sometimes sub-specialize of their specific “kind” of crime for instance.
- Credit Card Numbers
- Bank Accounts
- Refunding Guides
- SIM Swapping
- Gift Card Fraud
Combolists & Credentials
Another frequent and demanding kind of channel to watch are channels offering combolists. Combolists are “curated” lists of stolen usernames and passwords, typically accompanied by names, emails and different figuring out data that criminals use to try account takeover assaults.
Combolists could be created based mostly on geography, trade, account entry and different options that make them high-value for risk actors.
In many circumstances usernames, emails, and passwords are pasted immediately into the Telegram chat. In different circumstances risk actors could present recordsdata that comprise 1000’s or tens of 1000’s of information factors (and infrequently are accompanied by malware).
Nation State Hacktivism
The final class of channels that’s notably related for cybersecurity groups are nation-state hacktivist channels. Channels reminiscent of Bloodnet, Killnet, Noname47, Anonymous Sudan, and others have exploded in reputation, notably because the starting of the struggle in Ukraine.
These channels sometimes decide particular targets, typically important infrastructure in NATO international locations and try and deface web sites, DDoS very important providers, and leak information from corporations.
Concerned about Telegram? Flare Can Help
Flare’s Threat Exposure Management platform units up in half-hour and seamlessly screens the clear & darkish net for threats. We import a couple of million stealer logs per week, monitor a whole bunch of marketplaces and boards on Tor, and likewise detect threats throughout 1000’s of illicit Telegram channels.
In addition Flare mechanically detects publicity as a result of human error reminiscent of leaked API keys & credentials on GitHub, information publicity on pastebin, and different clear net sources of threat.
Sign up for a free Trial in 5-minutes.
Sponsored and written by Flare
