[ad_1]
Carding — the underground enterprise of stealing, promoting and swiping stolen cost card information — has lengthy been the dominion of Russia-based hackers. Happily, the broad deployment of safer chip-based cost playing cards within the United States has weakened the carding market. But a flurry of innovation from cybercrime teams in China is respiratory new life into the carding business, by turning phished card information into cellular wallets that can be utilized on-line and at essential avenue shops.
An picture from one Chinese phishing group’s Telegram channel exhibits varied toll street phish kits obtainable.
If you personal a cell phone, the probabilities are wonderful that sooner or later up to now two years it has acquired a minimum of one phishing message that spoofs the U.S. Postal Service to supposedly gather some excellent supply price, or an SMS that pretends to be a neighborhood toll street operator warning of a delinquent toll price.
These messages are being despatched via subtle phishing kits bought by a number of cybercriminals based mostly in mainland China. And they aren’t conventional SMS phishing or “smishing” messages, as they bypass the cellular networks fully. Rather, the missives are despatched via the Apple iMessage service and thru RCS, the functionally equal know-how on Google telephones.
People who enter their cost card information at one among these websites shall be informed their monetary establishment must confirm the small transaction by sending a one-time passcode to the client’s cellular gadget. In actuality, that code shall be despatched by the sufferer’s monetary establishment to confirm that the person certainly needs to hyperlink their card info to a cellular pockets.
If the sufferer then gives that one-time code, the phishers will hyperlink the cardboard information to a brand new cellular pockets from Apple or Google, loading the pockets onto a cell phone that the scammers management.
CARDING REINVENTED
Ford Merrill works in safety analysis at SecAlliance, a CSIS Security Group firm. Merrill has been learning the evolution of a number of China-based smishing gangs, and located that the majority of them function useful and informative video tutorials of their gross sales accounts on Telegram. Those movies present the thieves are loading a number of stolen digital wallets on a single cellular gadget, after which promoting these telephones in bulk for a whole lot of {dollars} apiece.
“Who says carding is dead?,” stated Merrill, who offered about his findings on the M3AAWG safety convention in Lisbon earlier right this moment. “This is the best mag stripe cloning device ever. This threat actor is saying you need to buy at least 10 phones, and they’ll air ship them to you.”
One promotional video exhibits stacks of milk crates stuffed stuffed with telephones on the market. A better inspection reveals that every cellphone is affixed with a handwritten notation that usually references the date its cellular wallets have been added, the variety of wallets on the gadget, and the initials of the vendor.
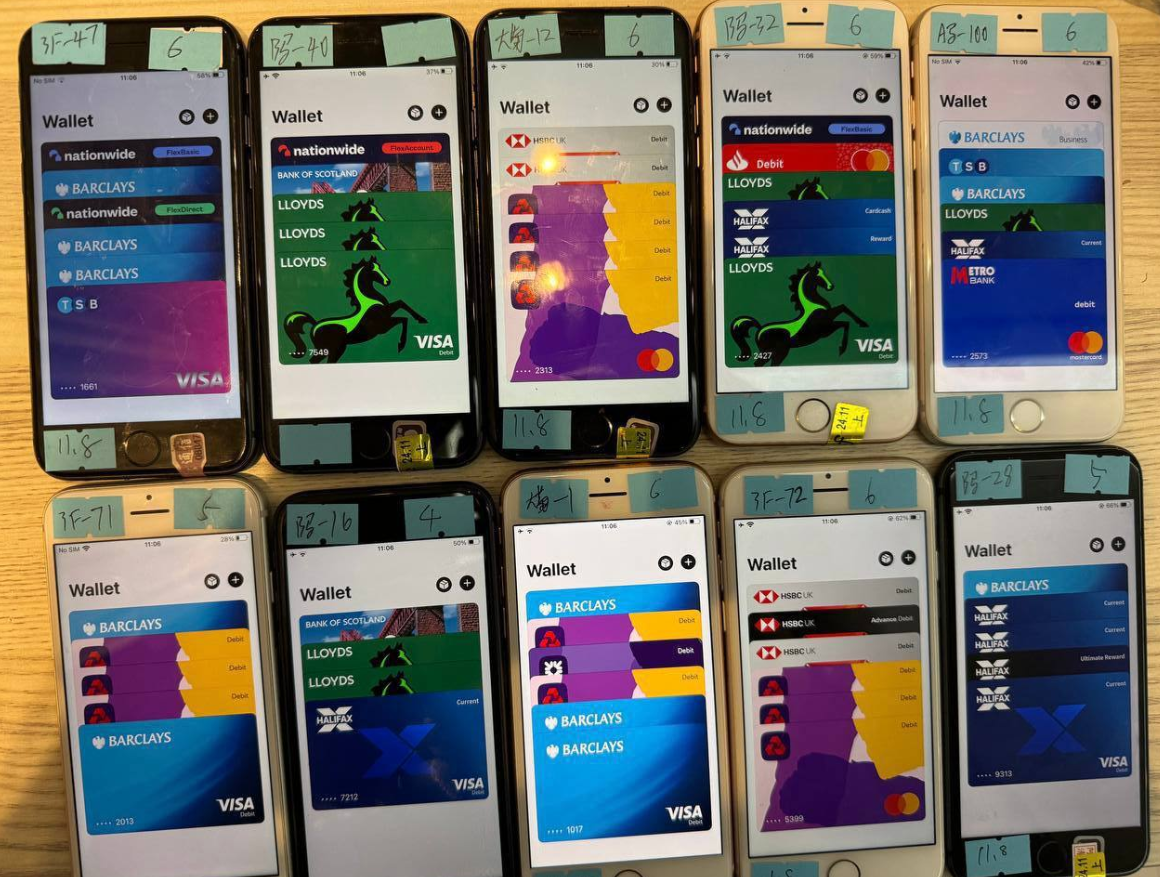
An picture from the Telegram channel for a preferred Chinese smishing equipment vendor exhibits 10 cellphones on the market, every loaded with 4-6 digital wallets from totally different UK monetary establishments.
Merrill stated one frequent means legal teams in China are cashing out with these stolen cellular wallets includes establishing pretend e-commerce companies on Stripe or Zelle and operating transactions via these entities — usually for quantities totaling between $100 and $500.
Merrill stated that when these phishing teams first started working in earnest two years in the past, they might wait between 60 to 90 days earlier than promoting the telephones or utilizing them for fraud. But today that ready interval is extra like simply seven to 10 days, he stated.
“When they first installed this, the actors were very patient,” he stated. “Nowadays, they only wait like 10 days before [the wallets] are hit hard and fast.”
GHOST TAP
Criminals can also money out cellular wallets by acquiring actual point-of-sale terminals and utilizing tap-to-pay on cellphone after cellphone. But in addition they supply a extra cutting-edge cellular fraud know-how: Merrill discovered that a minimum of one of many Chinese phishing teams sells an Android app known as “ZNFC” that may relay a sound NFC transaction to anyplace on the earth. The person merely waves their cellphone at a neighborhood cost terminal that accepts Apple or Google pay, and the app relays an NFC transaction over the Internet from a cellphone in China.
“The software can work from anywhere in the world,” Merrill stated. “These guys provide the software for $500 a month, and it can relay both NFC enabled tap-to-pay as well as any digital wallet. The even have 24-hour support.”
The rise of so-called “ghost tap” cellular software program was first documented in November 2024 by safety specialists at ThreatFabric. Andy Chandler, the corporate’s chief business officer, stated their researchers have since recognized a lot of legal teams from totally different areas of the world latching on to this scheme.
Chandler stated these embrace organized crime gangs in Europe which might be utilizing related cellular pockets and NFC assaults to take cash out of ATMs made to work with smartphones.
“No one is talking about it, but we’re now seeing ten different methodologies using the same modus operandi, and none of them are doing it the same,” Chandler stated. “This is much bigger than the banks are prepared to say.”
A November 2024 story within the Singapore each day The Straits Times reported authorities there arrested three international males who have been recruited of their residence international locations by way of social messaging platforms, and given ghost faucet apps with which to buy costly gadgets from retailers, together with cellphones, jewellery, and gold bars.
“Since Nov 4, at least 10 victims who had fallen for e-commerce scams have reported unauthorised transactions totaling more than $100,000 on their credit cards for purchases such as electronic products, like iPhones and chargers, and jewelry in Singapore,” The Straits Times wrote, noting that in one other case with the same modus operandi, the police arrested a Malaysian man and girl on Nov 8.

Three people charged with utilizing ghost faucet software program at an electronics retailer in Singapore. Image: The Straits Times.
ADVANCED PHISHING TECHNIQUES
According to Merrill, the phishing pages that spoof the USPS and varied toll street operators are powered by a number of improvements designed to maximise the extraction of sufferer information.
For instance, a would-be smishing sufferer may enter their private and monetary info, however then determine the entire thing is rip-off earlier than really submitting the information. In this case, something typed into the information fields of the phishing web page shall be captured in actual time, no matter whether or not the customer really clicks the “submit” button.
Merrill stated individuals who submit cost card information to those phishing websites usually are then informed their card can’t be processed, and urged to make use of a special card. This method, he stated, generally permits the phishers to steal multiple cellular pockets per sufferer.
Many phishing web sites expose sufferer information by storing the stolen info instantly on the phishing area. But Merrill stated these Chinese phishing kits will ahead all sufferer information to a back-end database operated by the phishing equipment distributors. That means, even when the smishing websites get taken down for fraud, the stolen information remains to be secure and safe.
Another necessary innovation is the usage of mass-created Apple and Google person accounts via which these phishers ship their spam messages. One of the Chinese phishing teams posted photographs on their Telegram gross sales channels displaying how these robotic Apple and Google accounts are loaded onto Apple and Google telephones, and organized snugly subsequent to one another in an expansive, multi-tiered rack that sits instantly in entrance of the phishing service operator.

The ashtray says: You’ve been phishing all night time.
In different phrases, the smishing web sites are powered by actual human operators so long as new messages are being despatched. Merrill stated the criminals seem to ship just a few dozen messages at a time, doubtless as a result of finishing the rip-off takes guide work by the human operators in China. After all, most one-time codes used for cellular pockets provisioning are typically solely good for a couple of minutes earlier than they expire.
Notably, not one of the phishing websites spoofing the toll operators or postal providers will load in a daily Web browser; they are going to solely render in the event that they detect {that a} customer is coming from a cellular gadget.
“One of the reasons they want you to be on a mobile device is they want you to be on the same device that is going to receive the one-time code,” Merrill stated. “They also want to minimize the chances you will leave. And if they want to get that mobile tokenization and grab your one-time code, they need a live operator.”
Merrill discovered the Chinese phishing kits function one other innovation that makes it easy for patrons to show stolen card particulars right into a cellular pockets: They programmatically take the cardboard information provided by the phishing sufferer and convert it right into a digital picture of an actual cost card that matches that sufferer’s monetary establishment. That means, trying to enroll a stolen card into Apple Pay, for instance, turns into as simple as scanning the fabricated card picture with an iPhone.
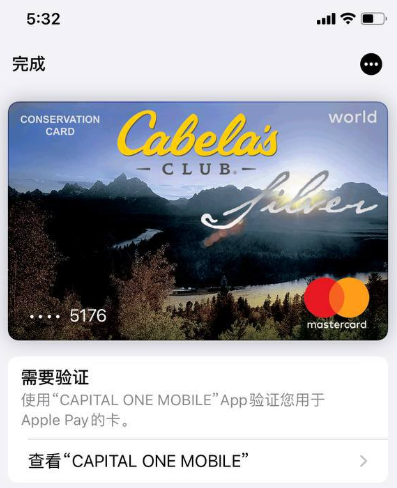
An advert from a Chinese SMS phishing group’s Telegram channel displaying how the service converts stolen card information into a picture of the stolen card.
“The phone isn’t smart enough to know whether it’s a real card or just an image,” Merrill stated. “So it scans the card into Apple Pay, which says okay we need to verify that you’re the owner of the card by sending a one-time code.”
PROFITS
How worthwhile are these cellular phishing kits? The finest guess to this point comes from information gathered by different safety researchers who’ve been monitoring these superior Chinese phishing distributors.
In August 2023, the safety agency Resecurity found a vulnerability in a single widespread Chinese phish equipment vendor’s platform that uncovered the private and monetary information of phishing victims. Resecurity dubbed the group the Smishing Triad, and located the gang had harvested 108,044 cost playing cards throughout 31 phishing domains (3,485 playing cards per area).
In August 2024, safety researcher Grant Smith gave a presentation on the DEFCON safety convention about monitoring down the Smishing Triad after scammers spoofing the U.S. Postal Service duped his spouse. By figuring out a special vulnerability within the gang’s phishing equipment, Smith stated he was capable of see that folks entered 438,669 distinctive bank cards in 1,133 phishing domains (387 playing cards per area).
Based on his analysis, Merrill stated it’s affordable to anticipate between $100 and $500 in losses on every card that’s became a cellular pockets. Merrill stated they noticed almost 33,000 distinctive domains tied to those Chinese smishing teams through the 12 months between the publication of Resecurity’s analysis and Smith’s DEFCON discuss.
Using a median variety of 1,935 playing cards per area and a conservative lack of $250 per card, that comes out to about $15 billion in fraudulent fees over a 12 months.
Merrill was reluctant to say whether or not he’d recognized further safety vulnerabilities in any of the phishing kits bought by the Chinese teams, noting that the phishers rapidly fastened the vulnerabilities that have been detailed publicly by Resecurity and Smith.
FIGHTING BACK
Adoption of touchless funds took off within the United States after the Coronavirus pandemic emerged, and plenty of monetary establishments within the United States have been desirous to make it easy for patrons to hyperlink cost playing cards to cellular wallets. Thus, the authentication requirement for doing so defaulted to sending the client a one-time code by way of SMS.
Experts say the continued reliance on one-time codes for onboarding cellular wallets has fostered this new wave of carding. KrebsOnSecurity interviewed a safety government from a big European monetary establishment who spoke on situation of anonymity as a result of they weren’t licensed to talk to the press.
That professional stated the lag between the phishing of sufferer card information and its eventual use for fraud has left many monetary establishments struggling to correlate the causes of their losses.
“That’s part of why the industry as a whole has been caught by surprise,” the professional stated. “A lot of people are asking, how this is possible now that we’ve tokenized a plaintext process. We’ve never seen the volume of sending and people responding that we’re seeing with these phishers.”
To enhance the safety of digital pockets provisioning, some banks in Europe and Asia require prospects to log in to the financial institution’s cellular app earlier than they’ll hyperlink a digital pockets to their gadget.
Addressing the ghost faucet risk might require updates to contactless cost terminals, to higher determine NFC transactions which might be being relayed from one other gadget. But specialists say it’s unrealistic to anticipate retailers shall be keen to interchange current cost terminals earlier than their anticipated lifespans expire.
And after all Apple and Google have an elevated position to play as nicely, provided that their accounts are being created en masse and used to blast out these smishing messages. Both corporations may simply inform which of their gadgets abruptly have 7-10 totally different cellular wallets added from 7-10 totally different individuals around the globe. They may additionally advocate that monetary establishments use safer authentication strategies for cellular pockets provisioning.
Neither Apple nor Google responded to requests for touch upon this story.
