[ad_1]

A brand new hacking group has leaked the configuration recordsdata, IP addresses, and VPN credentials for over 15,000 FortiGate units free of charge on the darkish internet, exposing a substantial amount of delicate technical data to different cybercriminals.
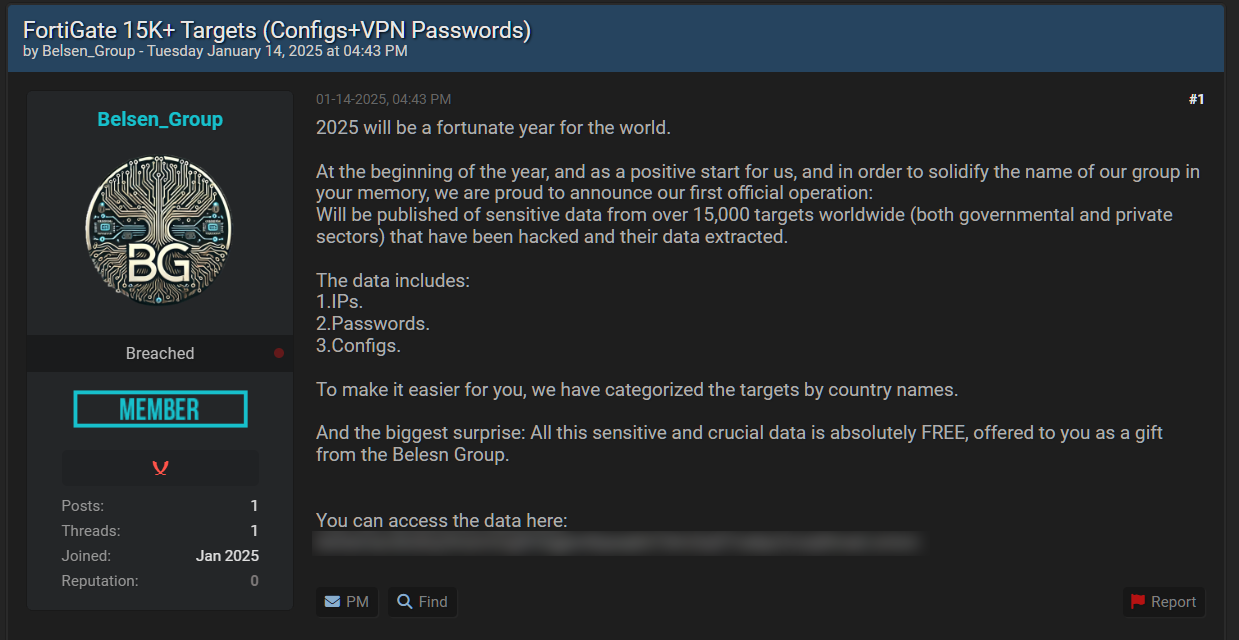
The knowledge was leaked by the “Belsen Group,” a brand new hacking group first showing on social media and cybercrime boards this month. To promote themselves, the Belsen Group has created a Tor web site the place they launched the FortiGate knowledge dump free of charge for use by different risk actors.
“At the start of the 12 months, and as a optimistic begin for us, and in an effort to solidify the title of our group in your reminiscence, we’re proud to announce our first official operation: Will be revealed of delicate knowledge from over 15,000 targets worldwide (each governmental and personal sectors) which were hacked and their knowledge extracted,” reads a hacking discussion board put up.
Source: BleepingComputer
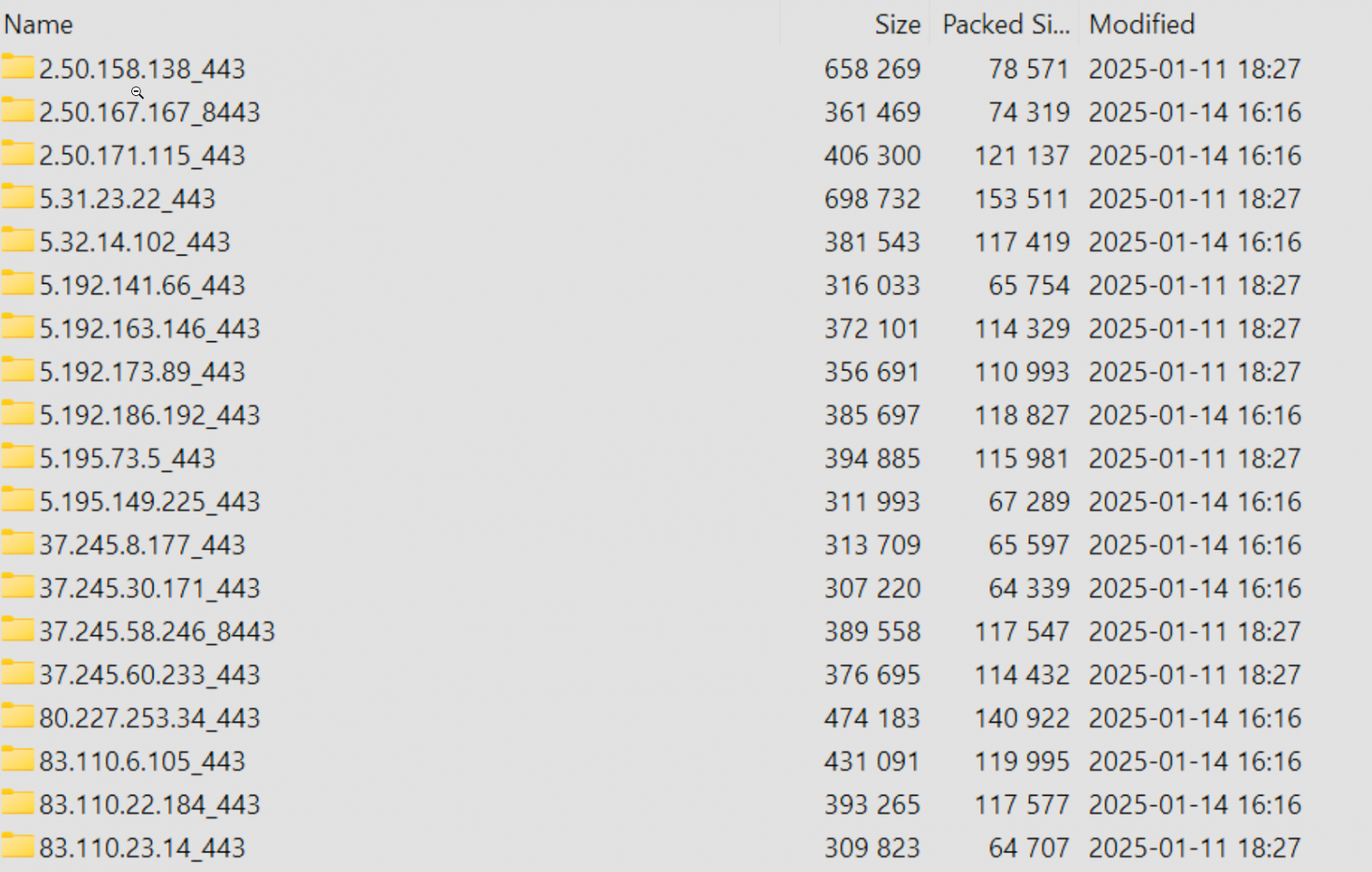
The FortiGate leak consists of a 1.6 GB archive containing folders ordered by nation. Each folder comprises additional subfolders for every FortiGate’s IP deal with in that nation.
Source: Beaumont
According to cybersecurity professional Kevin Beaumont, every IP deal with has a configuration.conf (Fortigate config dump) and a vpn-passwords.txt file, with a number of the passwords in plain textual content. The configs additionally comprise delicate data, equivalent to personal keys and firewall guidelines.
In a weblog put up in regards to the FortiGate leak, Beaumont says that the leak is believed to be linked to a 2022 zero-day tracked as CVE-2022–40684 that was exploited in assaults earlier than a repair was launched.
“I’ve achieved incident response on one gadget at a sufferer org, and exploitation was certainly by way of CVE-2022–40684 based mostly on artefacts on the gadget. I’ve additionally been capable of confirm the usernames and password seen within the dump matches the small print on the gadget,” explains Beaumont.
“The knowledge seems to have been assembled in October 2022, as a zero day vuln. For some motive, the info dump of config has been launched in the present day, simply over 2 years later.”
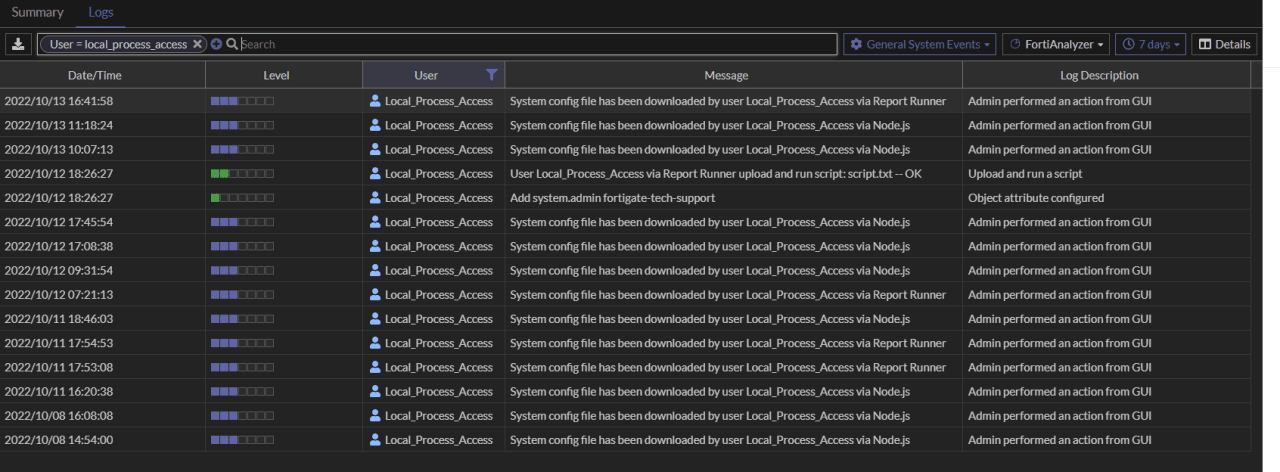
In 2022, Fortinet warned that risk actors had been exploiting a zero-day tracked as CVE-2022–40684 to obtain config recordsdata from focused FortiGate units after which add a malicious super_admin account known as ‘fortigate-tech-support’.
Source: Fortinet
German information website Heise analyzed the info leak and likewise stated that it was gathered in 2022, with all units using FortiOS firmware 7.0.0-7.0.6 or 7.2.0-7.2.2.
“All units had been geared up with FortiOS 7.0.0-7.0.6 or 7.2.0-7.2.2, most with model 7.2.0. We didn’t discover any FortiOS model within the knowledge trove that was newer than model 7.2.2, launched on October 3, 2022,” Heise reported.
However, FortiOS 7.2.2 mounted the CVE-2022–40684 flaw, so it will be unclear how units working that model might be exploited with this vulnerability.
Even although these configuration recordsdata had been collected in 2022, Beaumont warns that they nonetheless expose a whole lot of delicate details about a community’s defenses.
This contains firewall guidelines and credentials that, if not modified on the time, ought to be modified instantly now that the info has been launched to a broader pool of risk actors.
Beaumont says that he plans to launch a listing of the IP addresses within the leak so FortiGate admins can know if the leak impacted them.
In 2021, a risk actor leaked virtually 500,000 Fortinet VPN credentials that had been collected utilizing the CVE-2018-13379 vulnerability.
BleepingComputer additionally reached out to each the risk actors and Fortinet with questions in regards to the leak and can replace the story if we obtain a response.
