[ad_1]
A cybercrook who has been organising web sites that mimic the self-destructing message service privnote.com by accident uncovered the breadth of their operations lately once they threatened to sue a software program firm. The disclosure revealed a worthwhile community of phishing websites that behave and appear like the actual Privnote, besides that any messages containing cryptocurrency addresses might be routinely altered to incorporate a special cost handle managed by the scammers.
The actual Privnote, at privnote.com.
Launched in 2008, privnote.com employs expertise that encrypts every message in order that even Privnote itself can’t learn its contents. And it doesn’t ship or obtain messages. Creating a message merely generates a hyperlink. When that hyperlink is clicked or visited, the service warns that the message might be gone ceaselessly after it’s learn.
Privnote’s ease-of-use and recognition amongst cryptocurrency lovers has made it a perennial goal of phishers, who erect Privnote clones that operate kind of as marketed but additionally quietly inject their very own cryptocurrency cost addresses when a word is created that incorporates crypto wallets.
Last month, a brand new consumer on GitHub named fory66399 lodged a grievance on the “issues” web page for MetaMask, a software program cryptocurrency pockets used to work together with the Ethereum blockchain. Fory66399 insisted that their web site — privnote[.]co — was being wrongly flagged by MetaMask’s “eth-phishing-detect” checklist as malicious.
“We filed a lawsuit with a lawyer for dishonestly adding a site to the block list, damaging reputation, as well as ignoring the moderation department and ignoring answers!” fory66399 threatened. “Provide evidence or I will demand compensation!”
MetaMask’s lead product supervisor Taylor Monahan replied by posting a number of screenshots of privnote[.]co exhibiting the location did certainly swap out any cryptocurrency addresses.
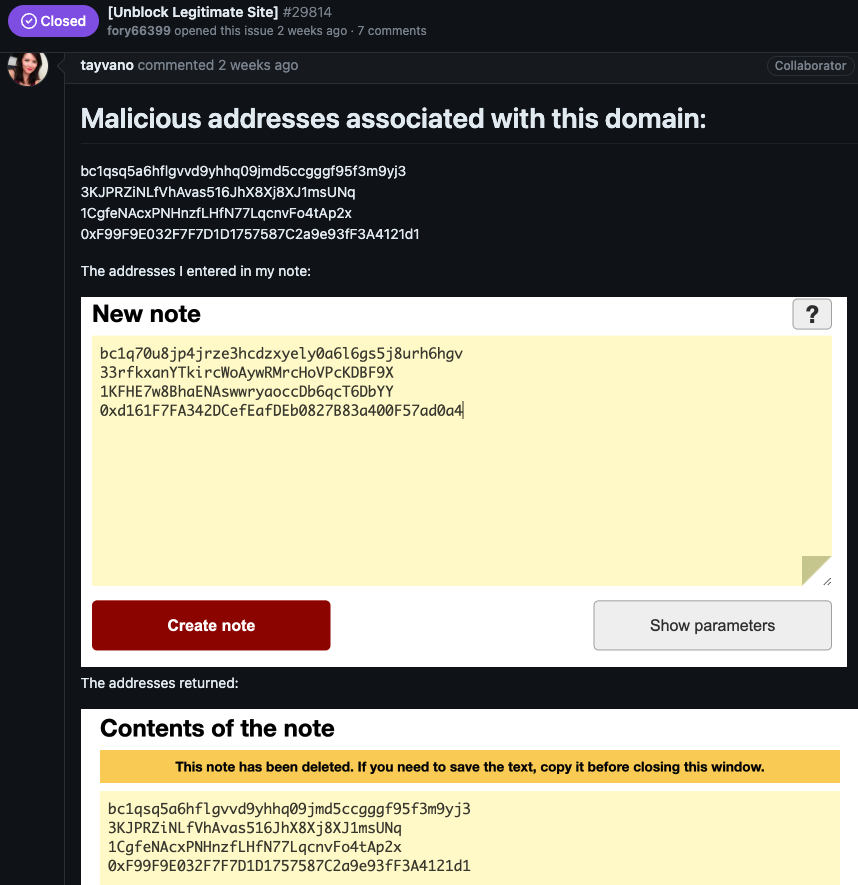
After being instructed the place they may ship a replica of their lawsuit, Fory66399 appeared to turn into flustered, and proceeded to say a variety of different fascinating domains:
You despatched me screenshots from another website! It’s purple!!!!
The tornote.io web site has a special coloration altogether
The privatenote,io web site additionally has a special coloration! What’s fallacious?????
A search at DomainTools.com for privatenote[.]io exhibits it has been registered to 2 names over as a few years, together with Andrey Sokol from Moscow and Alexandr Ermakov from Kiev. There is not any indication these are the actual names of the phishers, however the names are helpful in pointing to different websites focusing on Privnote since 2020.
DomainTools says different domains registered to Alexandr Ermakov embody pirvnota[.]com, privatemessage[.]web, privatenote[.]io, and tornote[.]io.
A screenshot of the phishing area privatemessage dot web.
The registration information for pirvnota[.]com at one level have been up to date from Andrey Sokol to “BPW” because the registrant group, and “Tambov district” within the registrant state/province area. Searching DomainTools for domains that embody each of those phrases reveals pirwnote[.]com.
Other Privnote phishing domains that additionally phoned residence to the identical Internet handle as pirwnote[.]com embody privnode[.]com, privnate[.]com, and prevnóte[.]com. Pirwnote[.]com is at present promoting safety cameras made by the Chinese producer Hikvision, through an Internet handle primarily based in Hong Kong.
It seems somebody has gone to nice lengths to make tornote[.]io appear to be a professional web site. For instance, this account at Medium has authored greater than a dozen weblog posts prior to now yr singing the praises of Tornote as a safe, self-destructing messaging service. However, testing exhibits tornote[.]io may also exchange any cryptocurrency addresses in messages with their very own cost handle.
These malicious word websites appeal to guests by gaming search engine outcomes to make the phishing domains seem prominently in search outcomes for “privnote.” A search in Google for “privnote” at present returns tornote[.]io because the fifth end result. Like different phishing websites tied to this community, Tornote will use the identical cryptocurrency addresses for roughly 5 days, after which rotate in new cost addresses.
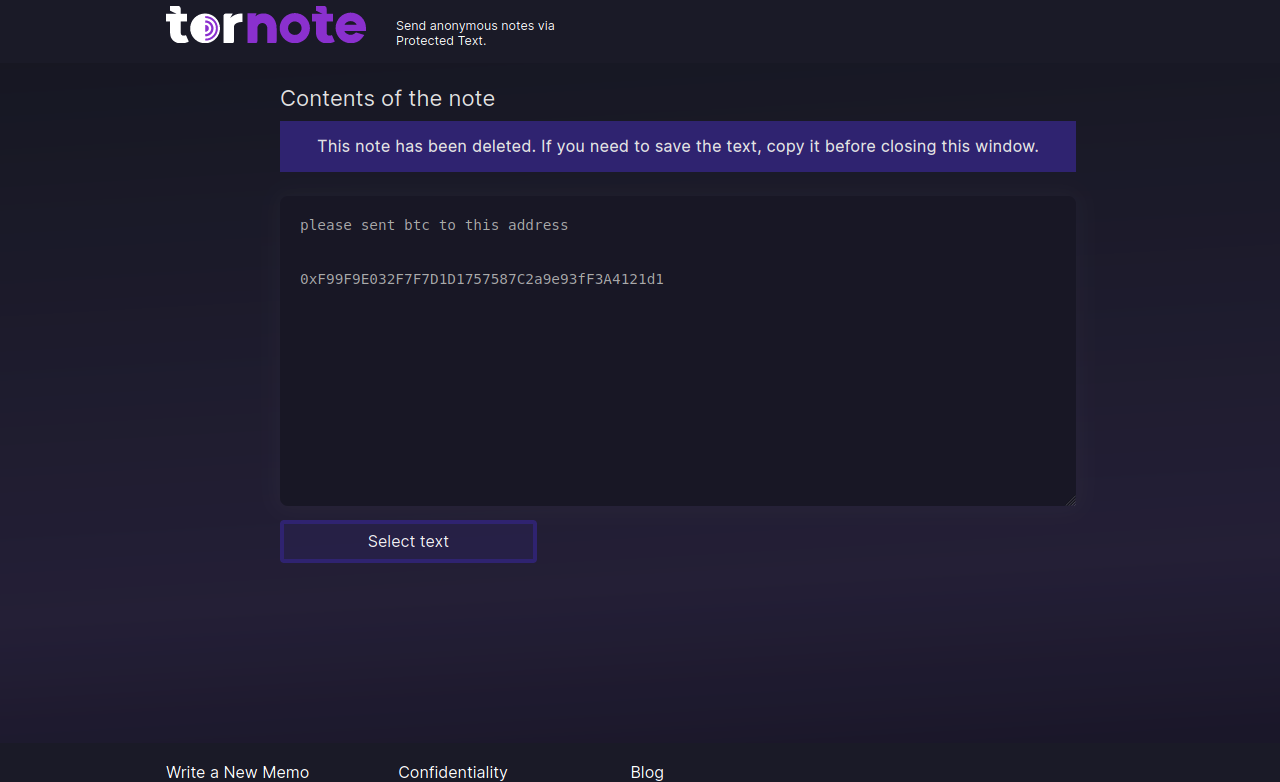
Tornote modified the cryptocurrency handle entered right into a take a look at word to this handle managed by the phishers.
Throughout 2023, Tornote was hosted with the Russian supplier DDoS-Guard, on the Internet handle 186.2.163[.]216. A evaluation of the passive DNS information tied to this handle exhibits that aside from subdomains devoted to tornote[.]io, the primary different area at this handle was hkleaks[.]ml.
In August 2019, a slew of internet sites and social media channels dubbed “HKLEAKS” started doxing the identities and private info of pro-democracy activists in Hong Kong. According to a report (PDF) from Citizen Lab, hkleaks[.]ml was the second area that appeared because the perpetrators started to increase the checklist of these doxed.
HKleaks, as listed by The Wayback Machine.
DomainTools exhibits there are greater than 1,000 different domains whose registration information embody the group title “BPW” and “Tambov District” as the placement. Virtually all of these domains have been registered by means of considered one of two registrars — Hong Kong-based Nicenic and Singapore-based WebCC — and virtually all seem like phishing or pill-spam associated.
Among these is rustraitor[.]data, an internet site erected after Russia invaded Ukraine in early 2022 that doxed Russians perceived to have helped the Ukrainian trigger.
An archive.org copy of Rustraitor.
In preserving with the general theme, these phishing domains seem targeted on stealing usernames and passwords to a few of the cybercrime underground’s busiest retailers, together with Brian’s Club. What do all of the phished websites have in widespread? They all settle for cost through digital currencies.
It seems MetaMask’s Monahan made the proper resolution in forcing these phishers to tip their hand: Among the web sites at that DDoS-Guard handle are a number of MetaMask phishing domains, together with metarrnask[.]com, meternask[.]com, and rnetamask[.]com.
How worthwhile are these personal word phishing websites? Reviewing the 4 malicious cryptocurrency cost addresses that the attackers swapped into notes handed by means of privnote[.]co (as pictured in Monahan’s screenshot above) exhibits that between March 15 and March 19, 2024, these handle raked in and transferred out practically $18,000 in cryptocurrencies. And that’s simply considered one of their phishing web sites.
