[ad_1]
The content material of this publish is solely the accountability of the writer. AT&T doesn’t undertake or endorse any of the views, positions, or info offered by the writer on this article.
Beyond its basic port scanning capabilities, Nmap presents a set of superior strategies designed to uncover vulnerabilities, bypass safety measures, and collect precious insights about goal techniques. Let’s check out these strategies:
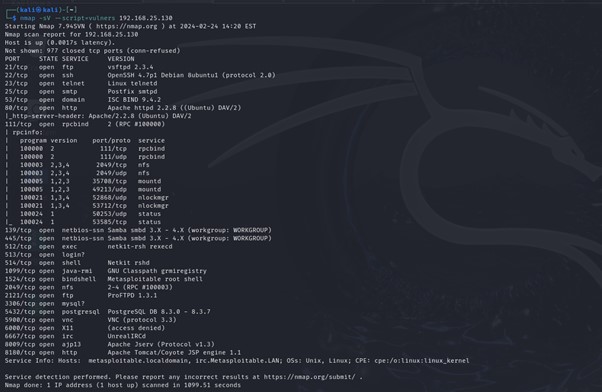
1. Vulnerability Detection
Syntax: nmap -sV –script=vulners
Nmap’s vulnerability detection function, facilitated by the ‘vulners’ script, permits customers to determine outdated providers vulnerable to recognized safety vulnerabilities. By querying a complete vulnerability database, Nmap supplies precious insights into potential weaknesses inside goal techniques.
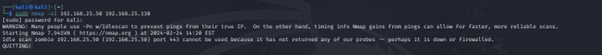
2. Idle Scanning
Syntax: nmap -sI
Idle scanning represents a stealthy method to port scanning, leveraging a “zombie” host to obfuscate the origin of scan requests. By monitoring modifications within the zombie host’s IP identification quantity (IP ID) in response to packets despatched to the goal, Nmap infers the state of the goal’s ports with out direct interplay.
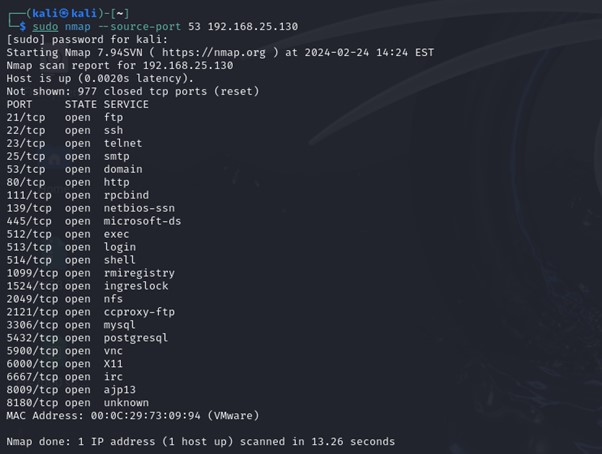
3. Firewall Testing (Source Port Spoofing)
Syntax: nmap –source-port
This approach entails testing firewall guidelines by sending packets with uncommon supply ports. By spoofing the supply port, safety professionals can consider the effectiveness of firewall configurations and determine potential weaknesses in community defenses.
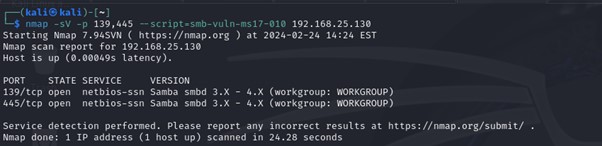
4. Service-Specific Probes (SMB Example)
Syntax: nmap -sV -p 139,445 –script=smb-vuln*
Nmap’s service-specific probes allow detailed examination of providers, such because the Server Message Block (SMB) protocol generally utilized in Windows environments. By leveraging specialised scripts, analysts can determine vulnerabilities and assess the safety posture of goal techniques.
5. Web Application Scanning (HTTP title seize)
Syntax: nmap -sV -p 80 –script=http-title
Web utility scanning with Nmap permits customers to assemble details about internet servers, probably aiding in vulnerability identification and exploitation.
By analyzing HTTP response headers, Nmap extracts precious insights about goal internet purposes and server configurations.
Nmap Scripting Engine:
One of the standout options of Nmap is its strong scripting engine (NSE), which permits customers to increase the instrument’s performance by way of customized scripts and plugins. NSE scripts allow customers to automate duties, carry out specialised scans, collect further info, and even exploit vulnerabilities in goal techniques.
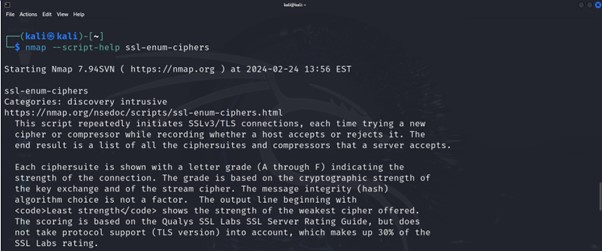
nmap –script-help scriptname Shows assist about scripts. For every script matching the given specification, Nmap prints the script title, its classes, and its description. The specs are the identical as these accepted by –script; so, for instance if you need assist in regards to the ssl-enum-ciphers script, you’d run nmap –script-help ssl-enum-ciphers
Users can leverage present NSE scripts or develop customized scripts tailor-made to their particular necessities. For instance, to carry out an online vulnerability scan utilizing Nmap’s NSE, one may use the next command:
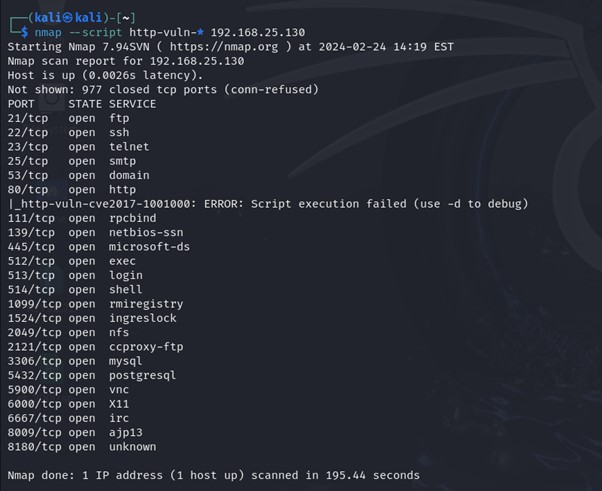
Syntax: nmap –script http-vuln-* target_ip
Nmap’s superior strategies signify a classy toolkit for community reconnaissance and vulnerability evaluation. From uncovering outdated providers to bypassing safety measures, these strategies empower safety professionals to evaluate and defend community infrastructures successfully. However, it’s crucial to make use of these strategies responsibly and ethically, making certain compliance with authorized and moral tips. By mastering Nmap’s superior capabilities, safety professionals can improve their means to detect and mitigate potential threats, thereby strengthening the general safety posture of networked environments. As the cybersecurity panorama continues to evolve, Nmap stays a steadfast companion within the ongoing battle towards rising threats and vulnerabilities.