[ad_1]
The content material of this publish is solely the accountability of the writer. AT&T doesn’t undertake or endorse any of the views, positions, or data offered by the writer on this article.
In our earlier weblog, we explored the importance of host discovery methods utilizing Nmap, Netdiscover, and Angry IP Scanner. Now, let’s dive deeper into the community reconnaissance and focus particularly on the highly effective options supplied by Nmap.
Renowned for its versatility and sturdy characteristic set, Nmap allows analysts to probe networked methods, map community topology, determine open ports, detect companies, and even decide working system particulars. Its command-line interface, coupled with a myriad of choices and scripting capabilities, makes it an indispensable asset for safety professionals, community directors, and moral hackers alike.
I’ve used a digital surroundings created primarily for demonstration functions to see these scanning methods in motion, Target machine for this demonstration is metasploitable2 (192.168.25.130), Attacker Machine is Kali Linux (192.168.25.128). We have already got seen tips on how to uncover hosts in a networked surroundings in our earlier weblog. Additionally, you’ll be able to confer with nmap.org for higher understanding of those methods.
Let’s check out completely different methods nmap affords:
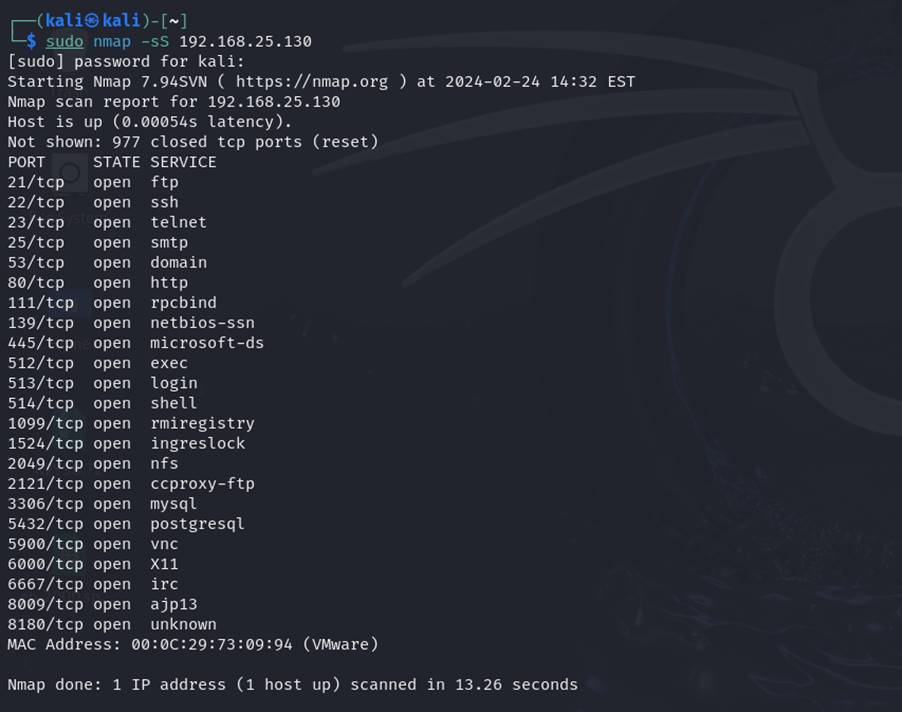
1. TCP SYN scan (-sS):
The TCP SYN scan, also called a half-open scan, sends SYN packets to focus on hosts and analyzes responses to find out if the host is alive. This approach is stealthy and environment friendly, because it doesn’t full the TCP handshake, thereby minimizing detection by intrusion detection methods (IDS).
Syntax: sudo nmap -sS target_ip
2. UDP scan (-sU):
The UDP scan sends UDP packets to focus on hosts and analyzes responses to determine open UDP ports. This approach is especially helpful for locating companies that will not reply to TCP probes.
Syntax: sudo nmap -sU target_ip
3. Comprehensive scan (-sC):
The complete scan possibility, denoted by -sC, allows customers to launch a battery of default scripts towards goal hosts. These scripts embody a variety of functionalities, together with service discovery, model detection, vulnerability evaluation, and extra.
Syntax: nmap -sC target_ip
Users can try to examine the output with aggressive scan and different scanning methods
Aggressive scan (-A):
The aggressive scan possibility, denoted by -A, combines varied scanning methods comparable to TCP SYN scanning, model detection, OS detection, and script scanning right into a single command. This scan offers complete insights into goal hosts however could improve the chance of detection.
Syntax: nmap -A target_ip
Above photos are partial snapshots of aggressive scan.
Best practices:
While Nmap affords unparalleled capabilities for community reconnaissance and safety auditing, it’s important to stick to greatest practices and moral tips:
Permission and authorization: Always guarantee that you’ve got express permission to conduct scans on track networks and methods. Unauthorized scanning can result in authorized repercussions and injury relationships with community house owners.
Scan timing and stealth: Adjust scan timing and methods to attenuate disruption and keep away from detection by intrusion detection methods (IDS) and firewalls. Use stealthy scanning choices, comparable to TCP SYN scans, to take care of a low profile.
Data interpretation: Analyze scan outcomes meticulously to determine potential safety dangers, prioritize remediation efforts, and validate safety configurations. Exercise warning whereas deciphering findings and keep away from making assumptions primarily based solely on scan outcomes.
Continuous studying and collaboration: Network reconnaissance and safety auditing are dynamic fields. Stay up to date with the most recent developments, collaborate with friends, and have interaction in knowledge-sharing actions to boost your experience and adapt to evolving threats.
Nmap’s wealthy characteristic set, scanning methods, and scripting capabilities empower analysts to navigate complicated networks, determine potential vulnerabilities, and fortify defenses towards rising threats.



