[ad_1]
The Minnesota-based Internet supplier U.S. Internet Corp. has a enterprise unit referred to as Securence, which makes a speciality of offering filtered, safe e-mail companies to companies, academic establishments and authorities companies worldwide. But till it was notified final week, U.S. Internet was publishing greater than a decade’s price of its inner e-mail — and that of hundreds of Securence shoppers — in plain textual content out on the Internet and only a click on away for anybody with a Web browser.
Headquartered in Minnetonka, Minn., U.S. Internet is a regional ISP that gives fiber and wi-fi Internet service. The ISP’s Securence division payments itself “a leading provider of email filtering and management software that includes email protection and security services for small business, enterprise, educational and government institutions worldwide.”
U.S. Internet/Securence says your e-mail is safe. Nothing could possibly be farther from the reality.
Roughly per week in the past, KrebsOnSecurity was contacted by Hold Security, a Milwaukee-based cybersecurity agency. Hold Security founder Alex Holden mentioned his researchers had unearthed a public hyperlink to a U.S. Internet e-mail server itemizing greater than 6,500 domains, every with its personal clickable hyperlink.
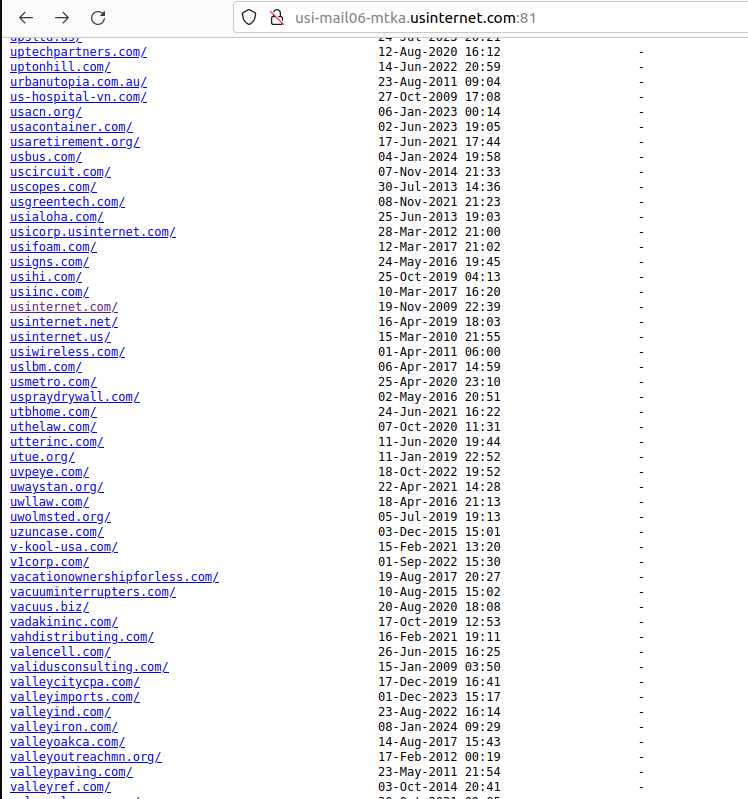
A tiny portion of the greater than 6,500 prospects who trusted U.S. Internet with their e-mail.
Drilling down into these particular person area hyperlinks revealed inboxes for every worker or consumer of those uncovered host names. Some of the emails dated again to 2008; others had been as current as the current day.
Securence counts amongst its prospects dozens of state and native governments, together with: nc.gov — the official web site of North Carolina; stillwatermn.gov, the web site for town of Stillwater, Minn.; and cityoffrederickmd.gov, the web site for the federal government of Frederick, Md.
Incredibly, included on this large index of U.S. Internet buyer emails had been the inner messages for each present and former worker of U.S. Internet and its subsidiary USI Wireless. Since that index additionally included the messages of U.S. Internet’s CEO Travis Carter, KrebsOnSecurity forwarded considered one of Mr. Carter’s personal current emails to him, together with a request to grasp how precisely the corporate managed to screw issues up so spectacularly.
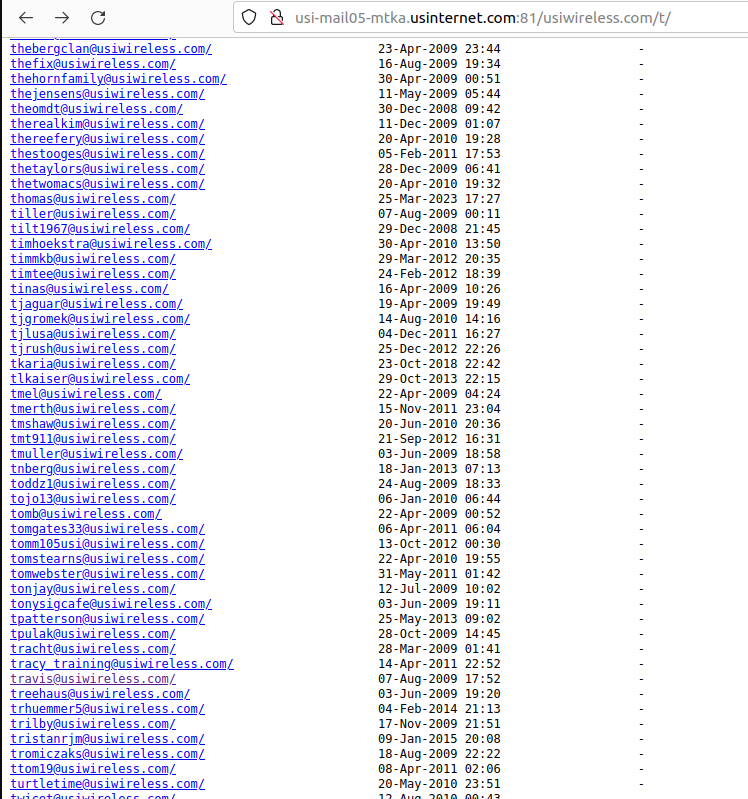
Individual inboxes of U.S. Wireless workers had been printed in clear textual content on the Internet.
Within minutes of that notification, U.S. Internet pulled all the printed inboxes offline. Mr. Carter responded and mentioned his workforce was investigating the way it occurred. In the identical breath, the CEO requested if KrebsOnSecurity does safety consulting for rent (I don’t).
[Author’s note: Perhaps Mr. Carter was frantically casting about for any expertise he could find in a tough moment. But I found the request personally offensive, because I couldn’t shake the notion that maybe the company was hoping it could buy my silence.]
Earlier this week, Mr. Carter replied with a extremely technical clarification that in the end did little to elucidate why or how so many inner and buyer inboxes had been printed in plain textual content on the Internet.
“The feedback from my team was a issue with the Ansible playbook that controls the Nginx configuration for our IMAP servers,” Carter mentioned, noting that this incorrect configuration was put in place by a former worker and by no means caught. U.S. Internet has not shared how lengthy these messages had been uncovered.
“The rest of the platform and other backend services are being audited to verify the Ansible playbooks are correct,” Carter mentioned.
Holden mentioned he additionally found that hackers have been abusing a Securence hyperlink scrubbing and anti-spam service referred to as Url-Shield to create hyperlinks that look benign however as a substitute redirect guests to hacked and malicious web sites.
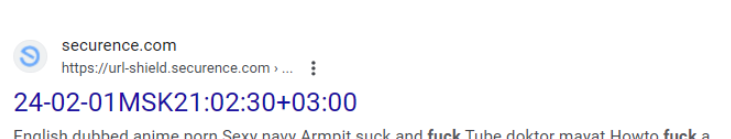
“The bad guys modify the malicious link reporting into redirects to their own malicious sites,” Holden mentioned. “That’s how the bad guys drive traffic to their sites and increase search engine rankings.”
For instance, clicking the Securence hyperlink proven within the screenshot immediately above leads one to a web site that tries to trick guests into permitting website notifications by couching the request as a CAPTCHA request designed to separate people from bots. After approving the misleading CAPTCHA/notification request, the hyperlink forwards the customer to a Russian internationalized area identify (рпроаг[.]рф).
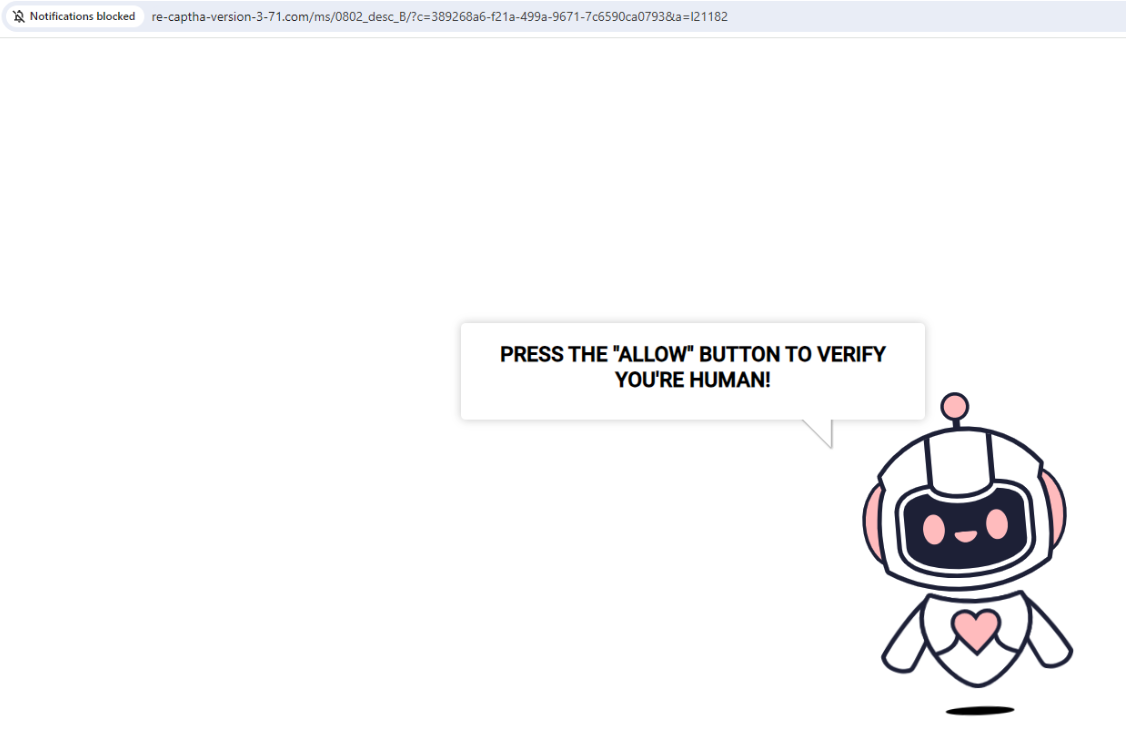
The hyperlink to this malicious and misleading web site was created utilizing Securence’s link-scrubbing service. Notification pop-ups had been blocked when this website tried to disguise a immediate for accepting notifications as a type of CAPTCHA.
U.S. Internet has not responded to questions on how lengthy it has been exposing all of its inner and buyer emails, or when the errant configuration modifications had been made. The firm additionally nonetheless has not disclosed the incident on its web site. The final press launch on the positioning dates again to March 2020.
KrebsOnSecurity has been writing about knowledge breaches for almost twenty years, however this one simply takes the cake by way of the extent of incompetence wanted to make such an enormous mistake unnoticed. I’m undecided what the correct response from authorities or regulators needs to be to this incident, however it’s clear that U.S. Internet shouldn’t be allowed to handle anybody’s e-mail until and till it may possibly reveal extra transparency, and show that it has radically revamped its safety.
[ad_2]
