[ad_1]

Recent variations of the Raspberry Robin malware are stealthier and implement one-day exploits which can be deployed solely on programs which can be prone to them.
One-day exploits discuss with code that leverages a vulnerability that the developer of the impacted software program patched lately however the repair has both not been deployed to all purchasers or it has not been utilized on all weak programs.
From the second the seller discloses the vulnerability, which often comes with publishing a patch, risk actors rush to create an exploit and use it earlier than the repair propagates to numerous programs.
According to a report from Check Point, Raspberry Robin has lately used a minimum of two exploits for 1-day flaws, which signifies that the malware operator both has the potential to develop the code or has sources that present it.
Raspberry Robin background
Raspberry Robin is a worm that Red Canary, a managed detection and response firm, first recognized in 2021. It spreads primarily by detachable storage gadgets akin to USB drives to determine a foothold on contaminated programs and facilitate the deployment of extra payloads.
It has been related to risk actors like EvilCorp, FIN11, TA505, the Clop ransomware gang, and different malware operations, however its creators and maintainers are unknown.
Since its discovery, Raspberry Robin has repeatedly advanced, including new options, evasion methods, and adopting a number of distribution strategies. One instance of evasion trick it carried out was to drop pretend payloads to mislead researchers.
Check Point studies that it has noticed an uptick in Raspberry Robin’s operations beginning October 2023, with giant assault waves focusing on programs worldwide.
A notable swap in current campaigns is using the Discord platform to drop malicious archive information onto the goal, doubtless after emailing the hyperlinks to the goal.
The archives include a digitally signed executable (OleView.exe) and a malicious DLL file (aclui.dll) that’s side-loaded when the sufferer runs the executable, thus activating Raspberry Robin within the system.
Targeting n-day flaws
When Raspberry Robin is first run on a pc, it should mechanically try to elevate privileges on the gadget utilizing a wide range of 1-day exploits.
Check Point highlights that the brand new Raspberry Robin marketing campaign leverages exploits for CVE-2023-36802, and CVE-2023-29360, two native privilege escalation vulnerabilities in Microsoft Streaming Service Proxy and the Windows TPM Device Driver.
In each circumstances, the researchers say, Raspberry Robin began exploiting the issues utilizing a then-unknown exploit lower than a month after the safety points had been disclosed publicly, on June 13 and September 12, 2023.
As illustrated within the timeline diagram under, Raspberry Robin exploited the 2 flaws earlier than safety researchers first revealed proof of idea exploit code for the 2 flaws.

Specifically, relating to CVE-2023-36802, which allows attackers to escalate their privileges to the SYSTEM stage, Cyfirma reported that an exploit had been accessible for buy on the Dark Web since February 2023, a full seven months earlier than Microsoft acknowledged and addressed the problem.
This timeline means that Raspberry Robin acquires 1-day exploits from exterior sources virtually instantly after their disclosure, as their price as zero days is probably going an excessive amount of even for bigger cybercrime operations.
Check Point discovered proof that factors to this idea as effectively, because the exploits utilized by Raspberry Robin weren’t embedded into the principle 32-bit part, however deployed as exterior 64-bit executables, and in addition lack the heavy obfuscation sometimes seen with this malware.
New evasion mechanisms
Check Point’s report additionally highlights a number of developments within the newest Raspberry Robin variants, which embrace new anti-analysis, evasion, and lateral motion mechanisms.
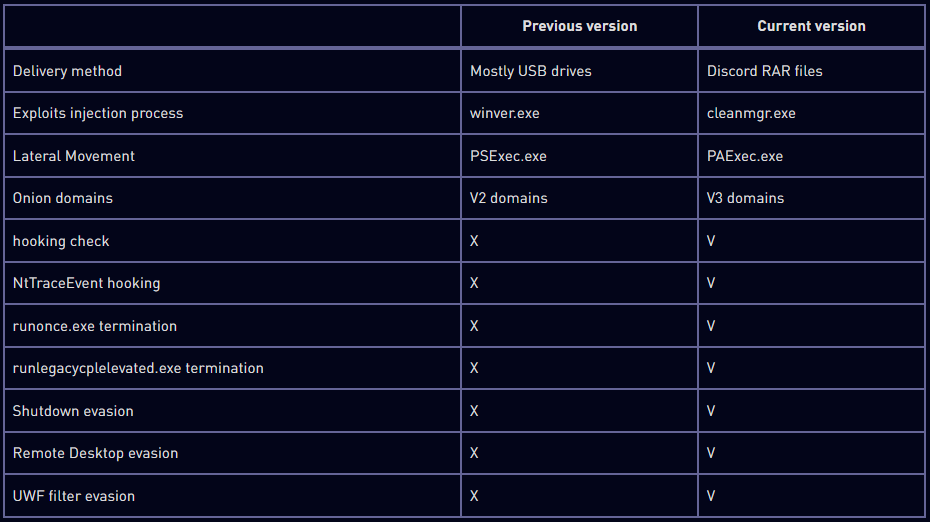
To evade safety instruments and OS defenses, the malware now makes an attempt to terminate particular processes like ‘runlegacycplelevated.exe,’ associated to Use Account Control (UAC), and patches the NtTraceEvent API to evade detection by Event Tracing for Windows (ETW).
Moreover, Raspberry Robin now checks if sure APIs, like ‘GetUserDefaultLangID’ and ‘GetModuleHandleW’, are hooked by evaluating the primary byte of the API operate to detect any monitoring processes by safety merchandise.
Another attention-grabbing new tactic is the implementation of routines that use APIs like ‘AbortSystemShutdownW’ and ‘ShutdownBlockReasonCreate’ to forestall system shutdowns that would interrupt the malware’s exercise.
To conceal the command and management (C2) addresses, the malware first randomly engages with one of many 60 hard-coded Tor domains pointing to well-known websites to make preliminary communications seem benign.
Finally, Raspberry Robin now makes use of PAExec.exe as an alternative of PsExec.exe to obtain the payload instantly from the internet hosting location. This resolution was doubtless made to extend its stealth, as PsExec.exe is thought to be misused by hackers.
The researchers imagine that Raspberry Robin will preserve evolving and add new exploits to its arsenal, searching for code that has not been launched publicly. Based on observations in the course of the malware evaluation, it’s doubtless that the operators of the malware doesn’t create is related to a developer that gives the exploit code.
Check Point’s report gives an inventory of indicators of compromise for Raspberry Robin, which consists in hashes for the malware, a number of domains in the Tor community, and Discord URLs for downloading the malicious archive.
[ad_2]
