[ad_1]

Victor De Schwanberg/Science Photo Library through Getty Images
Despite greater than a decade of reminding, prodding, and downright nagging, a shocking variety of builders nonetheless can’t convey themselves to maintain their code freed from credentials that present the keys to their kingdoms to anybody who takes the time to search for them.
The lapse stems from immature coding practices wherein builders embed cryptographic keys, safety tokens, passwords, and different types of credentials instantly into the supply code they write. The credentials make it straightforward for the underlying program to entry databases or cloud providers crucial for it to work as meant. I printed one such PSA in 2013 after discovering easy searches that turned up dozens of accounts that appeared to expose credentials securing computer-to-server SSH accounts. One of the credentials appeared to grant entry to an account on Chromium.org, the repository that shops the supply code for Google’s open supply browser.
In 2015, Uber realized the laborious approach simply how damaging the observe may be. One or extra builders for the journey service had embedded a singular safety key into code after which shared that code on a public GitHub web page. Hackers then copied the important thing and used it to entry an inside Uber database and, from there, steal delicate information belonging to 50,000 Uber drivers.
Uber attorneys argued on the time that “the contents of these internal database files are closely guarded by Uber,” however that rivalry is undermined by means the corporate took in safeguarding the information, which was no higher than stashing a home key beneath a door mat.
The variety of research printed since following the revelations underscored simply how frequent the observe had been and remained within the years instantly following Uber’s cautionary story. Sadly, the negligence continues even now.
Researchers from safety agency GitGuardian this week reported discovering virtually 4,000 distinctive secrets and techniques stashed inside a complete of 450,000 tasks submitted to PyPI, the official code repository for the Python programming language. Nearly 3,000 tasks contained at the very least one distinctive secret. Many secrets and techniques had been leaked greater than as soon as, bringing the whole variety of uncovered secrets and techniques to virtually 57,000.
“Exposing secrets in open-source packages carries significant risks for developers and users alike,” GitGuardian researchers wrote. “Attackers can exploit this information to gain unauthorized access, impersonate package maintainers, or manipulate users through social engineering tactics.”
The credentials uncovered offered entry to a spread of sources, together with Microsoft Active Directory servers that provision and handle accounts in enterprise networks, OAuth servers permitting single sign-on, SSH servers, and third-party providers for buyer communications and cryptocurrencies. Examples included:
- Azure Active Directory API Keys
- GitHub OAuth App Keys
- Database credentials for suppliers comparable to MongoDB, MySQL, and PostgreSQL
- Dropbox Key
- Auth0 Keys
- SSH Credentials
- Coinbase Credentials
- Twilio Master Credentials.
Also included within the haul had been API keys for interacting with varied Google Cloud providers, database credentials, and tokens controlling Telegram bots, which automate processes on the messenger service. This week’s report mentioned that exposures in all three classes have steadily elevated previously 12 months or two.
The secrets and techniques had been uncovered in varied varieties of information printed to PyPI. They included major .py information, README information, and take a look at folders.
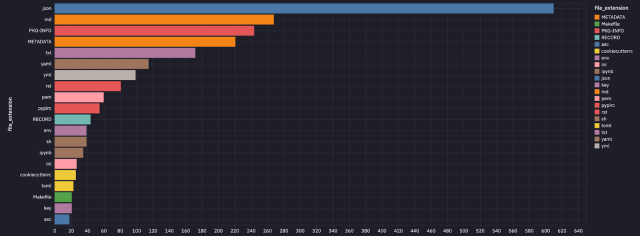
GitGuardian
GitGuardian examined the uncovered credentials and located that 768 remained energetic. The threat, nonetheless, can prolong effectively past that smaller quantity. GitGuardian defined:
It is necessary to notice that simply because a credential cannot be validated doesn’t imply it needs to be thought of invalid. Only as soon as a secret has been correctly rotated can you recognize whether it is invalid. Some varieties of secrets and techniques GitGuardian remains to be working towards routinely validating embrace Hashicorp Vault Tokens, Splunk Authentication Tokens, Kubernetes Cluster Credentials, and Okta Tokens.
There are not any good causes to show credentials in code. The report mentioned the most typical trigger is by chance.
“In the course of outreach for this project, we discovered at least 15 incidents where the publisher was unaware they had made their project public,” the authors wrote. “Without naming any names, we did want to mention some of these were from very large companies that have robust security teams. Accidents can happen to anyone.”
Over the previous decade, varied mechanisms have change into accessible for permitting code to securely entry databases and cloud sources. One is .env information which might be saved in non-public environments exterior of the publicly accessible code repository. Others are instruments such because the AWS Secrets Manager, Google Cloud’s Secret Manager, or the Azure Key Vault. Developers may make use of scanners that examine code for credentials inadvertently included.
The examine examined PyPI, which is only one of many open supply repositories. In years previous, code hosted in different repositories comparable to NPM and RubyGems has additionally been rife with credential publicity, and there’s no cause to suspect the observe doesn’t proceed in them now.
[ad_2]
