[ad_1]
ESET Research
ESET researchers reveal a rising sophistication in threats affecting the LATAM area by using evasion strategies and high-value concentrating on
17 Oct 2023
•
,
3 min. learn

Much just like the life and mysterious demise of Pharaoh Tutankhamun, often known as King Tut, the menace panorama in Latin America (LATAM) stays shrouded in thriller. This is primarily because of the restricted world consideration on the evolving malicious campaigns inside the area. While notable occasions like ATM assaults, the banking trojans born in Brazil, and the Machete cyberespionage operations have garnered media protection, we’re conscious that there’s extra to the story.
In a parallel to how archaeological excavations of King Tut’s tomb make clear historical Egyptian life, we launched into a journey to delve into less-publicized cyberthreats affecting Latin American nations. Our initiative, named Operation King TUT (The Universe of Threats), sought to discover this important menace panorama. On October fifth, we introduced the outcomes of our comparative evaluation on the Virus Bulletin 2023 convention: the total convention paper might be learn right here.
In the evaluation, we selected to look again at numerous publicly documented campaigns concentrating on the LATAM area between 2019 and 2023, as might be seen within the timeline beneath. All of those cybercriminal actions are detected completely in Latin America and will not be related to world crimeware. Since every of those operations has its personal distinctive traits and doesn’t seem linked to any recognized menace actor, it’s extremely doubtless that a number of actors are at play.
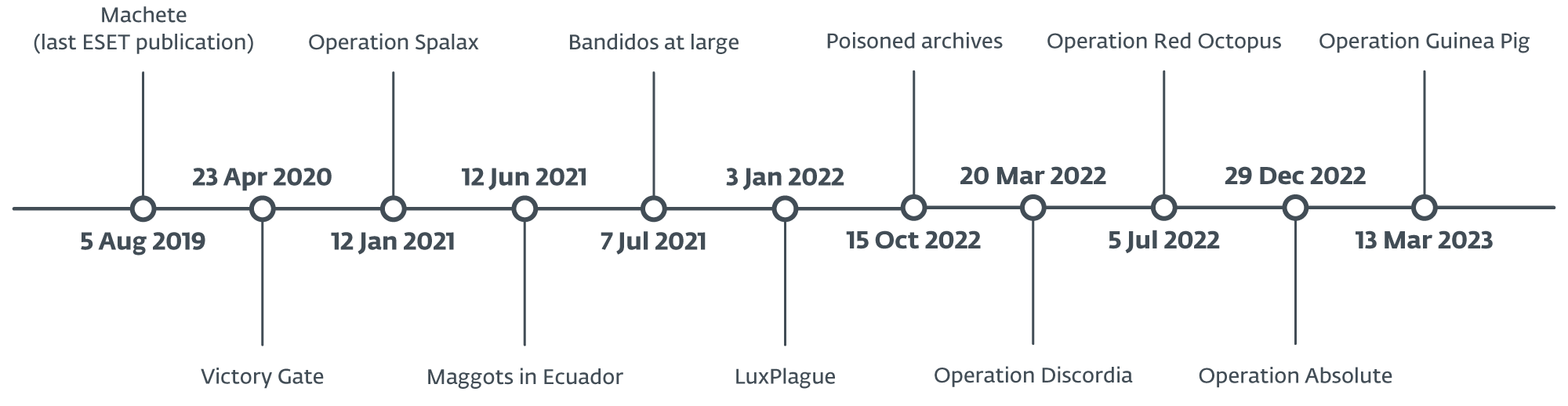
Our analysis revealed a notable shift from simplistic, opportunistic crimeware to extra complicated threats. Notably, we’ve got noticed a transition in concentrating on, shifting from a deal with most of the people to high-profile customers, together with companies and governmental entities. These menace actors frequently replace their instruments, introducing completely different evasion strategies to extend the success of their campaigns. Furthermore, they’ve expanded their crimeware enterprise past Latin America, mirroring the sample seen in banking trojans born in Brazil.
Our comparability additionally reveals that almost all of malicious campaigns seen within the area are directed at enterprise customers, together with authorities sectors, by using primarily spearphishing emails to achieve potential victims, usually masquerading as acknowledged organizations inside particular nations within the area, significantly authorities or tax entities.
The precision and specificity noticed in these assaults level to a excessive stage of concentrating on, indicating that the menace actors have detailed information about their supposed victims. In these campaigns, attackers make the most of malicious elements like downloaders and droppers, principally created in PowerShell and VBS.
Regarding the instruments utilized in these malicious operations in Latin America, our observations point out a desire for RATs, significantly from the njRAT and AsyncRAT households. Additionally, in campaigns primarily concentrating on authorities entities, we’ve got recognized using different malware households like Bandook and Remcos, albeit to a lesser extent.
Based on the conclusions ensuing from our comparability, we imagine that there’s greater than only one group behind the proliferation of these kind of campaigns and that these teams are actively wanting into completely different strategies and methods for his or her campaigns to be as profitable as potential. Additionally, we suspect that socioeconomic disparities prevalent in Latin America could affect the modus operandi of attackers on this area, though this specific side falls past the scope of our analysis. The full VB2023 convention paper about Operation King TUT is accessible right here.
Aggregated indicators of compromise (IoCs) can be found on our GitHub repository.
For any inquiries about our analysis printed on WeLiveSecurity, please contact us at threatintel@eset.com.
ESET Research provides non-public APT intelligence experiences and information feeds. For any inquiries about this service, go to the ESET Threat Intelligence web page.


