[ad_1]
Quantum computer systems are altering the cryptography guidelines
Under Data Encryption, the CISA Zero Trust Maturity Model v2.0 cites the criticality of “cryptographic agility” on the third (out of 4) stage of maturity. Cryptographic agility is the flexibility to alter the underlying cryptographic algorithms in functions and communications channels. I imagine this highlights the significance for organizations to have the ability to pivot their encryption algorithms to a post-quantum cryptographic world. As quantum computing turns into extra extensively obtainable, the flexibility to crack robust encryption turns into weaker.
In August 2016, NIST revealed a request for touch upon necessities and standards for submission for nominations for Public-key Post-quantum Cryptographic (PQC) Algorithms. That signifies that 7 years in the past, the hunt for a PQC began. In 2024, that is anticipated to be finalized. However, there are steps that organizations must be taking now to arrange for this. To perceive why PQC is so essential, you will need to comply with the evolution of public-key cryptography.
Public-key cryptography
Public-key cryptography is what permits safe connections similar to over the Internet. Without these safe connections, there can be no on-line banking, procuring, or personal messaging. Public-key cryptography depends on algorithms which are primarily unbreakable with at this time’s expertise.
This wasn’t all the time the case. Due to more and more extra highly effective computer systems, older algorithms grew to become extra inclined to brute-force assaults. For occasion, RC5-64 was cracked in just below 5 years utilizing 2002 expertise –that’s primarily an Intel Pentium II working Windows NT– with teams of individuals donating private laptop cycles. Comparing present expertise vs. 2002, we will simply throw a lot processing energy, together with renting from a cloud present, that the auto-generated abstract from that comparability hyperlink is astonishing:
“In single core, the difference is 8100%. In multi-core, the difference in terms of gap is 42425%.”
This is without doubt one of the causes we moved from SSL to TLS1.0 and have continued to advance to TLS1.3. Older legacy algorithms turn into deprecated and are not in use.
Public-key cryptography isn’t simply used for net servers for SSL/TLS. They are used to safe electronic mail, SSH/SFTP connections, digital signatures, Cryptocurrencies, and anyplace PKI (Public Key Infrastructure) is used together with Microsoft Active Directory. If the present set of algorithms may be breached by way of brute power assault, the Internet might collapse, and this is able to have a devastating impact on the worldwide financial system and even cut back the effectiveness of navy communications.
Fortunately, with many present “classical” applied sciences, we’ve got been ready so as to add extra bits in algorithms to make them tougher, making brute power assaults tougher over time. For occasion, SHA-2 went from 224 to 256 to 384 all the way in which to 512 earlier than being largely changed by SHA-3, which is safer with similar variety of bits. At least, this was the trail ahead earlier than quantum computing grew to become a brand new viable option to crack these legacy algorithms.
What is a quantum laptop?
You could also be aware of Diffie-Hellman key alternate, the RSA (Rivest-Shamir-Adleman) cryptosystem, and elliptic curve cryptosystems at present in use at this time. The safety of those is determined by the problem of sure quantity theoretic issues similar to Integer Factorization or the Discrete Log Problem over varied teams.
In 1994, Shor’s algorithm was developed that might effectively remedy every of those applied sciences. However, this algorithm relied on a very completely different structure: quantum computer systems. In the final 29 years, work has progressed to not solely create new quantum algorithms however the precise {hardware} to run them on (preliminary quantum computer systems had been emulated utilizing classical computer systems and really gradual). Recently, Google has developed a 70-qubit quantum laptop. A qubit is the quantum laptop equal of classical laptop 1’s and 0’s, and extra qubits imply a extra highly effective system. This Google system known as the Sycamore Quantum Computer can remedy a fancy benchmark in just a few seconds. The world’s present quickest classical supercomputer, known as Frontier from Hewlett Packard, would take 47 years on that very same benchmark.
While this can be a extremely particular take a look at, it did exhibit “quantum supremacy”: that quantum computer systems can outpace classical computing methods. If you aren’t involved as a result of these computer systems are costly, know that cloud suppliers have already got choices you should use at this time: Azure Quantum, IBM and AWS Braket allow you to hire time at below $100 an hour. Google Quantum Computing Service seems to solely enable entry from an authorized checklist, not (but) giving entry to the general public. Recently. the Gemini Mine, which is a 2-qubit quantum laptop, grew to become obtainable to purchase instantly for about $5,000. This will not be a strong machine however could possibly be used to invisibly develop and take a look at malicious quantum software program.
However, the long run is obvious: Quantum computing breaks the present cryptographic algorithms.
What is a PQC and why do I would like to make use of it?
Post-quantum Cryptography (PQC) relies on algorithms that can resist each classical and quantum computer systems. Since the present algorithms should not PQC, they’re going to be focused by dangerous actors and something utilizing them will not be successfully encrypted.
While quantum computer systems are nonetheless of their infancy, you may suppose you can sit again after which after they go mainstream, merely transfer to a PQC algorithm when the chance turns into excessive sufficient. However, there’s a want to maneuver to a PQC as quickly as doable: any encrypted information similar to web transmissions may be saved, after which later decrypted. Organizations should assume that something utilizing present encryption algorithms must be handled as cleartext.
Using PQC will then set up a line within the sand: even when transmissions are recorded or encrypted drives are stolen, they won’t be able to be decrypted by quantum computer systems or classical supercomputers. Backups utilizing outdated algorithms? Assume they’re cleartext and erase them. Any secrets and techniques that had been despatched over the web? Assume they’re now within the public area.
While governments have lengthy remoted communications channels so even encrypted communications are laborious to smell, most personal organizations don’t – and may try to maneuver to PQC as quickly as doable.
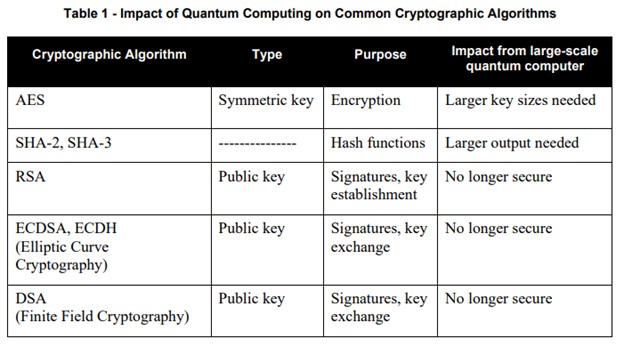
Table 1 from NIST IR 8105 exhibits the most well-liked cryptographic algorithms and the impression quantum computer systems may have on them.
NOTE: This was revealed in April 2016.
How ought to my group put together?
Although a PQC algorithm isn’t anticipated till 2024, organizations ought to put together and take steps to make the migration a fast course of:
- Inventory all cryptographic algorithms at present in use.
- What methods are used?
- Is this information at relaxation or in transmission?
- Prioritize this stock in order that when your group must implement it, the high-risk sources are addressed first – similar to Internet-facing methods or methods that home your most delicate information.
- Document for every system kind the method required to switch the in-use algorithm.
- Do we have to improve the important thing size (AES and SHA2 or SHA-3) or substitute the algorithm solely (RSA, ECDSA, ECDH, DSA)
- System updates or PQC algorithm set up
- Configuration file modification
- Restarting important providers
- Testing course of to make sure PQC algorithms are most popular/prioritized between methods when they’re negotiating which algorithm to make use of.
- Review your provide chain and perceive the place you want third events to ship PQC.
- For occasion, if you’re working accounting software program SaaS, you need to have the ability to hook up with it out of your workstation securely. You are reliant on that SaaS to help PQC and must be asking for that as quickly as doable. Depending on the chance profile, you could wish to tackle that in any contractual negotiations to assist guarantee it occurs.
These preparation steps ought to both be added to your regular governance processes or made right into a mission. Decide if you should use inside sources or for those who ought to herald a 3rd celebration like AT&T Cybersecurity to assist. In any case, be sure that that is in your radar prefer it now could be on mine. Once post-quantum cryptographic algorithms turn into obtainable, all organizations must be trying to implement them.
Resources to study extra:
DHS: Preparing for Post-Quantum Cryptography Infographic (dhs.gov)
NIST: Report on Post-Quantum Cryptography (nist.gov)
CISA: Quantum-Readiness: Migration to Post-Quantum Cryptography (cisa.gov)
NSA: The Commercial National Security Algorithm Suite 2.0 and Quantum Computing FAQ (protection.gov)