[ad_1]

Europol, the European Union’s company for legislation enforcement cooperation, launched its yearly Internet Organised Crime Threat Assessment report, which supplies key findings and rising cybersecurity threats that impression governments, companies and people in Europe; nevertheless, these threats can have an effect on folks worldwide. The essential themes of the report are cybercriminals are more and more codependent, the basics of cybercrime, technically talking, stay the identical and there’s a fixed use of cryptocurrencies and an elevated use of mixers.
Jump to:
Increase in cybercriminals’ experience makes them extra codependent
According to Europol, the panorama of cybercrime has advanced into a fancy internet of interdependence amongst cybercriminals.
As laptop safety and protection evolves, cybercrime does, too. Different kinds of laptop information are wanted for working fraud on the web. For occasion, relying on the fraud, a cybercriminal may want malware that isn’t detected by antivirus and safety options, a safe web connection that may’t be traced again to them, preliminary entry to firms’ networks or mailboxes, environment friendly social engineering content material, fraudulent content material internet hosting and extra.
All of these wants require deep information in several fields, which is a cause why numerous cybercriminals have determined to promote their information as a service to different cybercriminals.
Initial entry brokers promote the compromised accesses they accumulate to different cybercriminals who use it for on-line fraud schemes. IABs are additionally “pivotal for ransomware attacks,” wrote Europol, as they promote preliminary entry to ransomware teams who then use it to penetrate company programs to maneuver inside their community earlier than executing the ransomware.
Crypter builders cover malicious payloads and malware in order that they’re tougher for safety options to detect.
Counter AntiVirus companies are very talked-about amongst cybercriminals. Malware builders and crypter companies frequently use CAV companies to scan their binaries in opposition to a number of antivirus options. This permits them to determine which elements of their code are flagged as malicious by antivirus engines.
Virtual personal networks are offered by cybercriminals to keep away from identification. Several VPN options can be found within the cybercriminal underground market, providing anonymity by encrypting site visitors from end-to-end and by not offering any cooperation with requests for info from legislation enforcement entities.
Bulletproof internet hosting is central to loads of cybercrimes and is utilized by many criminals. Europol said that these internet hosting companies “… do not engage in extensive customer monitoring practices such as Know-Your-Customer procedures and storing of customer and metadata facilitating criminal activities.” Bulletproof internet hosting companies don’t present buyer info to legislation enforcement apart from an automatic affirmation of an e mail tackle. Finally, internet hosting issues might be tough, because it’s usually a fancy worldwide enterprise the place servers are sometimes in a number of areas worldwide.
Andy Zollo, regional vp for EMEA at cybersecurity firm Imperva, talked with TechRepublic.
“The fact that so many cybercriminals are now operating co-dependent services is further evidence of how complex the cybercrime industry has become, and demonstrates the need for organisations to have cohesive security strategies in place that can protect applications, APIs, and their sensitive data. However, the flip side is that the growing co-dependency among cybercriminals means that if businesses are able to disrupt any part of the cybercrime supply chain, it can make a significant difference to their overall security posture. Even one solution or initiative, if well-targeted, can be enough to help break the cycle.”
Modus operandi doesn’t change, strategies improve in sophistication
All kinds of cybercriminals use the identical strategies of reaching their targets in some unspecified time in the future. The most used approach is phishing; it’s usually at all times the place to begin of economic fraud or cyberespionage operations.
From a technical perspective, the modus opérandi doesn’t change, however the way in which to realize it will get extra subtle and will increase in quantity. European Union regulatory developments have made fraud with compromised bank card info tougher, which has the impact of turning cybercriminals extra onto the customers than the digital programs.
Remote Desktop Protocol brute-forcing and VPN vulnerability exploitation are the most typical intrusion ways utilized by cybercriminals, based on Europol. Phishing kits have additionally develop into more and more accessible for cybercriminals, no matter their degree of group and technical experience.
SEE: TechRepublic Premium’s Brute Force and Dictionary Attacks: A Guide for IT Leaders
Obfuscated cryptocurrencies actions
When potential, cybercriminals use cryptocurrencies. Ransomware teams all request cryptocurrencies, paid immediately on devoted crypto wallets. Payments between cybercriminals for various companies are additionally at all times made in cryptocurrencies.
An intensive use of a number of layers of obfuscation strategies is mostly deployed by cybercriminals earlier than lastly cashing out their unlawful earnings. Cryptocurrency mixers, a service that blends the cryptocurrencies of many customers collectively, are sometimes used to obfuscate the origins and homeowners of the funds. These mixers make it tough for investigators to hint the cash trails successfully.
Another generally employed methodology is cryptocurrency swappers, which permit for fast buying and selling from one cryptocurrency to a different, additional complicating the method of figuring out the origin of the funds. In addition, change of nations and decentralized exchanges are used for obfuscation. These cryptocurrency obfuscation strategies require extremely expert investigators to observe the cash trails and conduct profitable investigations.
Europol exhibits a fancy cryptocurrency case the place mixers, cryptocurrency switches and splits are closely used (Figure A).
Figure A
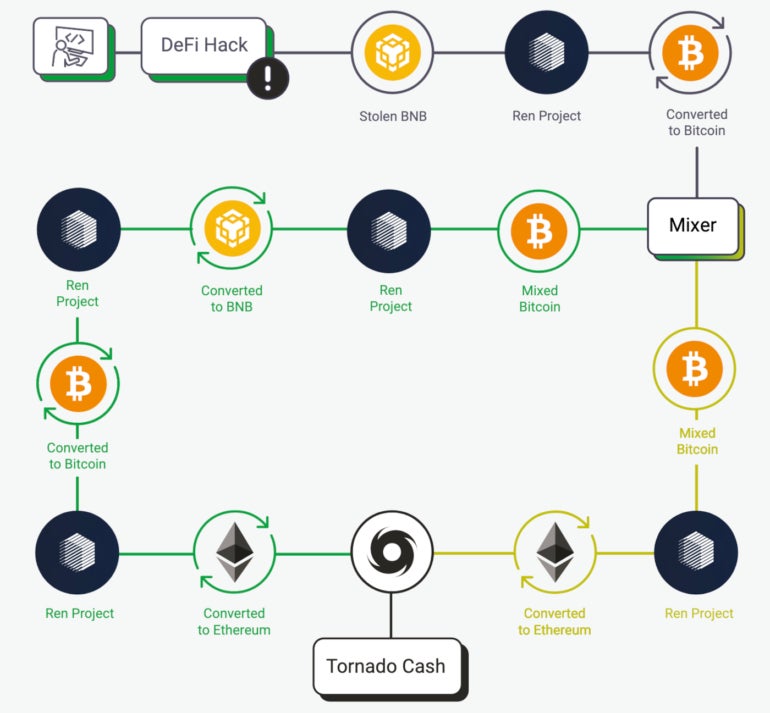
In the Decentralised Finance hack depicted in Figure A, the cryptocurrency, Binance Coin, is stolen and despatched to Ren Project, a protocol that permits motion of values throughout blockchains. Then, it’s transformed to Bitcoin earlier than going right into a mixer that splits the cash in two, going again to Ren Project. It’s transformed to BNB on one aspect and transformed to Ethereum on the opposite aspect. The Ethereum quantity goes via the Tornado Cash mixer earlier than being reconverted to Ethereum.
Good information for preventing cybercrime
The time when a cybercriminal was working all of their fraud alone is coming to an finish; cybercriminals need to be environment friendly, in order that they purchase the companies of extra expert friends moderately than do it themselves. This is sweet information for the battle in opposition to cybercrime as a result of arresting cybercriminals on one side of cybercrime usually impacts others and stops much more fraud.
For instance, Europol reported a number of profitable worldwide operations resulting in arrests. One occasion was the VPNLab takedown in 2022. Many customers of VPNLab used the service to connect with domains of firms being compromised by a ransomware group. This takedown demonstrated how bringing down one service might assist additional investigations.
Another instance is Operation Elaborate in 2022, which took down a full service that offered Automated Interactive Voice Response, interception of one-time passwords and reside monitoring of calls, resulting in the arrest of 142 suspects.
Disclosure: I work for Trend Micro, however the views expressed on this article are mine.
