[ad_1]

Cisco Talos found a new Microsoft Windows coverage loophole that enables a risk actor to signal malicious kernel-mode drivers executed by the working system. The risk actor takes benefit of a particular compatibility coverage from Microsoft to allow the signing of malicious kernel-mode drivers. Then, the RedDriver malware, which is likely to be developed by a Chinese-speaking risk actor, targets browsers used primarily in China.
Malicious kernel-mode drivers symbolize a extreme risk versus user-mode drivers. Learn extra about these drivers, what RedDriver malware does and who’s focused, and the right way to preserve your enterprise protected.
Jump to:
Why malicious kernel-mode drivers are a extreme risk
Microsoft Windows working techniques deal with two sorts of drivers: user-mode drivers and kernel-mode drivers. The latter are rather more highly effective than the user-mode drivers for a number of causes. Kernel-mode drivers:
- Run at a low stage within the working system, making them more durable to detect than user-mode functions and permitting the execution of code with the very best privileges.
- Can stay persistent, being executed each time the working system begins.
- Can be used to bypass safety as a result of they’ve direct entry to {hardware} and system elements, corresponding to firewalls or antimalware software program.
- Can embed rootkit functionalities to cover their presence or the presence of different software program corresponding to malware on the system.
Microsoft has deployed measures to guard techniques and struggle the specter of malicious kernel-mode drivers based mostly on certificates. Kernel-mode drivers must be digitally signed with a certificates coming from a verified certificates authority. From Windows 10 model 1607 on, Microsoft up to date the signing coverage to now not permit new kernel-mode drivers that haven’t been submitted to and signed by its Developer Portal.
The loophole that’s being exploited
In order to take care of the performance and compatibility of older drivers, Microsoft created just a few exceptions for the next instances:
- The pc was upgraded from an earlier launch of Windows to Windows 10 model 1607.
- The safe boot parameter is about to off within the pc’s BIOS or UEFI firmware.
- Drivers signed with an end-entity certificates issued previous to July 29, 2015 that chains to a supported cross-signed Certificate Authority.
A loophole exists right here in the best way a newly compiled driver could be “signed with non-revoked certificates issued prior or expired before July 29th 2015, provided that the certificate chains to a supported cross-signed CA,” as written by Cisco Talos.
Therefore, a number of open-source instruments have began exploiting this loophole to allow builders to signal drivers efficiently.
Tools exist to assist builders exploit this Windows coverage loophole; Cisco Talos mentions Fu**CertVerifyTimeValidity (precise identify is within the Cisco Talos report) and HookSignTool, each of which can be found at no cost on the web (Figure A). Fu**CertVerifyTimeValidity has been obtainable since 2018 on Chinese boards, whereas HookSignTool appeared in 2019.
Figure A
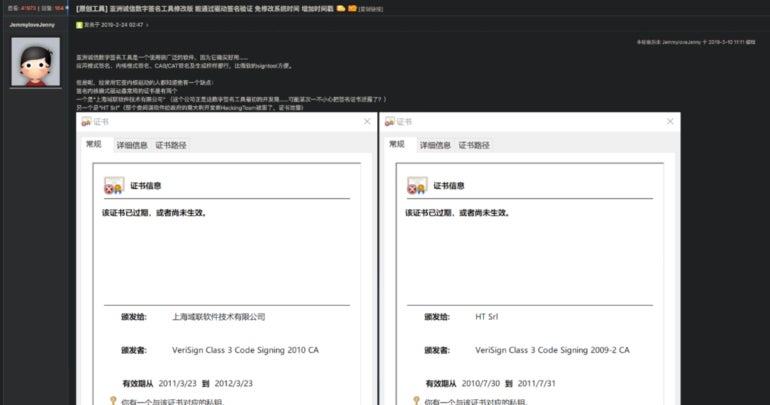
Those instruments use the Microsoft Detours package deal, which was made for monitoring and instrumenting API calls on Windows, to cross a customized time within the “pTimeToVerify” parameter, permitting an invalid time to be verified. Detour can be used to alter the signing timestamp throughout execution.
Both instruments want a non-revoked code signing certificates that expired or was issued earlier than July 29, 2015 and its personal key and password to efficiently forge a digital signature. Cisco Talos researchers discovered a file hosted on GitHub in a fork of one of many instruments containing greater than a dozen expired code-signing certificates regularly used with each instruments.
Meet RedDriver malware
The assault chain begins with a single executable file named DnfClientShell32.exe that injects a DnfConsumer useful resource right into a distant course of. Then, DnfConsumer begins speaking with the risk actor’s command and management server (C2) to provoke the obtain of the RedDriver payload. DnfConsumer additionally opens a listening port on localhost (127.0.0.1).
According to Cisco Talos, RedDriver is an undocumented malicious kernel-mode driver whose identify comes from the binary itself, as its developer named it within the compilation undertaking file path. RedDriver has been signed utilizing the HookSignTool. Cisco Talos researchers discovered totally different variations of the malicious kernel signed with totally different certificates.
RedDriver, as soon as executed, permits browser hijacking based mostly on a hardcoded checklist of browsers, a lot of that are in style in China (Figure B). And, it provides a root certificates to the system.
Figure B
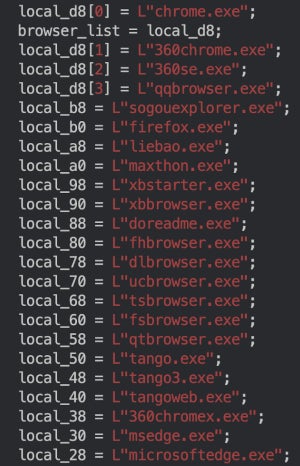
RedDriver redirects site visitors from these browsers to 127.0.0.1, but it’s unclear why. It nonetheless represents a excessive risk as RedDriver is ready to manipulate browser site visitors on the packet stage by utilizing the Windows Filtering Platform, which is a set of APIs and system providers that gives a platform for creating community filtering functions.
An earlier model of RedDriver was discovered by Cisco Talos researchers. That model has been lively since at the very least 2021 and contained a hardcoded checklist of names belonging to dozens of drivers, “many of which pertained to software that is Chinese in origin” and “focused on software that would be used in Internet cafes” in line with Cisco Talos, which additionally mentions that the concentrating on of web cafes in China by cybercrime teams is just not uncommon.
Chinese-speaking risk actors and victims
The builders of RedDriver have left various traces indicating they’re Chinese-speaking people.
For occasion, all domains related to RedDriver have been positioned in China. The RedDriver operation includes code from a number of open-source instruments largely originating from Chinese-speaking boards. An preliminary portion of the RedDriver code was initially posted on a Chinese discussion board.
Just because the RedDriver risk actor might be of Chinese origin, the targets of RedDriver are Chinese-speaking individuals. The checklist of focused browsers and the checklist of driver names focused by RedDriver are largely associated to Chinese software program. The preliminary an infection information beginning with “Dnf” are probably an try and masquerade as a extremely in style recreation in China, Dungeon Fighter Online, known as DNF.
How to guard your enterprise from this cybersecurity risk
Cisco Talos reported all of the certificates utilized by the risk actor to Microsoft. A drivers block checklist maintained inside Windows by Microsoft has been up to date to dam all these certificates.
Cisco Talos’s analysis doesn’t point out the preliminary methodology used to contaminate computer systems, which is likely to be web site compromise, phishing emails or different social engineering methods, so basic cybersecurity hygiene must be deployed.
For starters, all working techniques, firmware and software program must all the time be updated and patched. This will keep away from being compromised by frequent vulnerabilities.
Security options must be deployed to observe endpoints and networks for any suspicious conduct. Attached information in emails must be fastidiously analyzed.
Finally, employees must be skilled to detect fraud and an infection makes an attempt, particularly phishing.
Disclosure: I work for Trend Micro, however the views expressed on this article are mine.
[ad_2]
