[ad_1]
In February, we expanded Google Workspace client-side encryption (CSE) capabilities to incorporate Gmail and Calendar along with Drive, Docs, Slides, Sheets, and Meet.
CSE in Gmail was designed to supply business and public sector organizations an extra layer of confidentiality and knowledge integrity safety past the prevailing encryption provided by default in Workspace. When CSE is enabled, electronic mail messages are protected utilizing encryption keys which are totally beneath the shopper’s management. The knowledge is encrypted on the shopper machine earlier than it’s despatched to Google servers that wouldn’t have entry to the encryption keys, which implies the info is indecipherable to us–we’ve got no technical means to entry it. The complete course of occurs within the browser on the shopper machine, with out the necessity to set up desktop purposes or browser extensions, which signifies that customers get the identical intuitive productiveness and collaboration experiences that they get pleasure from with Gmail as we speak. Let’s take a deeper look into the way it works.
How we constructed Client-side Encryption for Workspace
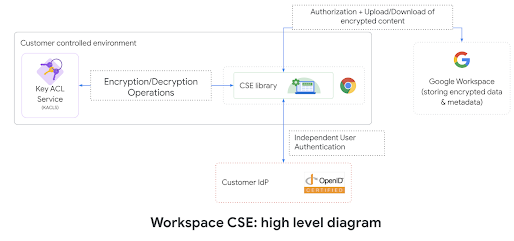
We invented and designed a brand new service known as, Key Access Control List Service (KACLS), that’s used throughout all important Workspace purposes. Then, we labored straight with prospects and companions to make it safe, dependable, and easy to deploy. KACLS performs cryptographic operations with encryption keys after validating end-user authentication and authorization. It runs in a buyer’s managed setting and supplies the important thing administration API known as by the CSE-enabled Workspace shoppers. We have a number of companions offering software program implementations of the KACLS API that can be utilized by our prospects.
At a excessive degree, Workspace shopper code takes benefit of envelope encryption to encrypt and decrypt the consumer content material on the shopper with a Data Encryption Key (DEK) and leverage the KACLS to encrypt and decrypt the DEK. In order to supply separation of obligation, we use the shopper’s OpenID Connect (OIDC) IdP to authenticate end-users and supply a JSON Web Token assertion with a declare figuring out the consumer (3P_JWT). For each encryption/decryption request despatched to KACLS, the applying (e.g. Gmail) supplies a JSON Web Token assertion with a declare authorizing the present end-user operation (G_JWT). KACLS validates these authentication and authorization tokens earlier than returning, for instance, a decrypted DEK to the consumer’s shopper machine.
More particulars on KACLS can be found in Google Workspace Encryption Whitepaper and CSE reference API.
How we constructed CSE into Gmail
Google Workspace Engineering groups have been exhausting at work over a number of years to ship to our prospects the flexibility to have their knowledge protected with client-side encryption. This journey required us to work intently with prospects and companions to supply a functionality that was safe, straightforward to make use of, intuitive and simply deployable. It was additionally necessary for CSE to work seamlessly throughout the Workspace merchandise: you’ll be able to create a Meet CSE scheduled assembly in Calendar CSE and follow-up with Gmail CSE emails containing hyperlinks to Drive CSE information.
Client-side encryption in Gmail was constructed with openness and interoperability in thoughts. The underlying expertise getting used is S/MIME, an open commonplace for sending encrypted messages over electronic mail. S/MIME is already supported in most enterprise electronic mail shoppers, so customers are capable of talk securely, outdoors of their area, no matter what supplier the recipient is utilizing to learn their mail, with out forcing the recipients to log right into a proprietary portal. S/MIME makes use of uneven encryption. The public key and the e-mail of every consumer are included within the consumer’s S/MIME certificates. Similarly to TLS used for HTTPS, every certificates is digitally signed by a sequence of certificates authorities as much as a broadly trusted root certificates authority. The certificates acts as a digital enterprise card, enabling anybody getting it to encrypt emails for that consumer. The consumer’s non-public keys are stored safe beneath buyer management and are utilized by customers for decryption of incoming emails and digital signature of outgoing emails.
We determined to leverage the CSE paradigm used for Drive CSE and never preserve the non-public key on the machine, to maintain them as secure as potential. Instead, we prolonged our KACLS API to help uneven encryption and signature operations. This permits our prospects to centrally provision and allow S/MIME, on the KACLS, for all their customers with out having to deploy certificates individually to every consumer machine.
CSE in Gmail makes use of the end-user’s shopper current cryptographic functionalities (Web Crypto API for internet browsers as an illustration) to carry out native encryption operations and run client-side code to carry out all S/MIME message era.
Now let’s cowl the detailed consumer flows:
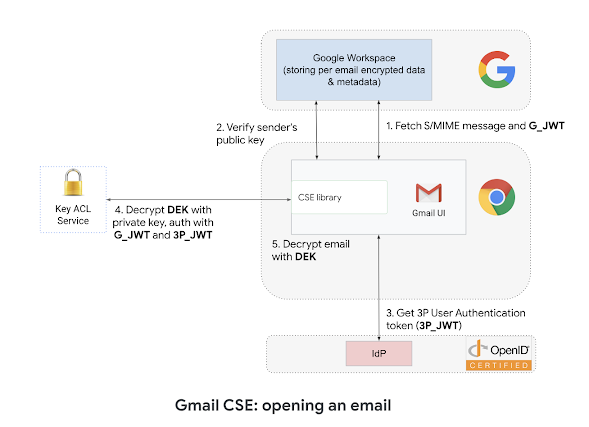
When sending an electronic mail, the Gmail shopper generates a MIME message, encrypts the message with a random Data Encryption Key (DEK) then makes use of the recipients’ public keys to encrypt the DEK, calls KACLS (with the consumer authenticated by buyer’s IdP and approved by Google) to digitally signal content material and at last sends the authenticated and encrypted S/MIME message, which accommodates each the encrypted electronic mail and the encrypted DEK, to Google servers for supply to the recipients.
When receiving an electronic mail, Gmail will confirm that the digital signature of the e-mail is legitimate and matches the sender’s identification, which protects the e-mail towards tampering. Gmail will belief digital identities signed by Root CA PKI in addition to customized area configurations. The Gmail shopper will name KACLS (with the authentication and authorization JWT) to decrypt the e-mail encryption key, then can decrypt the e-mail and render it to the end-user.
How we defend the applying
Workspace already makes use of the most recent cryptographic requirements to encrypt all knowledge at relaxation and in transit between its amenities for all companies. Additionally, Gmail makes use of Transport Layer Security (TLS) by default for communication with different electronic mail service suppliers. CSE in Gmail, nonetheless, supplies an extra layer of safety for delicate content material. The safety of Gmail CSE is paramount to us, and we developed new further mechanisms to make sure CSE content material could be locked right into a safe container. On the online, we’ve got been leveraging iframe origin isolation, strict postMessage API, and Content Security Policy to guard the consumer’s delicate knowledge. Those safety controls present a number of layers of security to make sure that CSE content material stays remoted from the remainder of the applying. See this simplified diagram protecting the isolation defending CSE emails throughout composition or show.
What’s subsequent for Client-side encryption and why it’s necessary
CSE in Gmail makes use of S/MIME to encrypt and digitally signal emails utilizing public keys equipped by prospects, which add an extra degree of confidentiality and integrity to emails. This is completed with intensive safety controls to guard consumer knowledge confidentiality, but additionally transparently built-in in Gmail UI to please our customers. However our work just isn’t finished, and we’re actively partnering with Google Research to additional develop client-side capabilities. You can see a few of our progress on this area with our presentation on the RSA Security Conference final 12 months the place we supplied perception into the challenges and the sensible methods to supply superior capabilities, equivalent to AI-driven phishing safety for CSE.