[ad_1]

Microsoft has launched Sysmon 15, changing it right into a protected course of and including the brand new ‘FileExecutableDetected’ choice to log when executable recordsdata are created.
For these not accustomed to Sysmon (or System Monitor), it’s a free Microsoft Sysinternals instrument that may monitor and block malicious/suspicious exercise and log occasions to the Windows Event Log.
By default, Sysmon displays fundamental occasions equivalent to new course of creation and the termination of processes. However, it’s doable to create superior configuration recordsdata that allow you to monitor numerous conduct, equivalent to file deletions, Windows clipboard adjustments, and detecting and blocking the shredding of recordsdata.
Users can discover the whole record of directives within the Sysmon schema, which could be seen by working the sysmon -s command on the command line.
Yesterday, Microsoft launched Sysmon 15.0, which incorporates two new options – the hardening of this system by turning it right into a protected course of and the flexibility to detect when executable recordsdata are created on the monitored system.
Sysmon is now a protected course of
As Sysmon is often used to detect malicious conduct, it’s in risk actors’ greatest curiosity to tamper with or disable the software program.
With this launch, Microsoft transformed the Sysmon.exe executable right into a protected course of to forestall malicious code from being injected into the method.
“In Windows 8.1, a brand new idea of protected service has been launched to permit anti-malware user-mode companies to be launched as a protected service,” explains a Microsoft article concerning the characteristic.
“After the service is launched as protected, Windows makes use of code integrity to solely enable trusted code to load into the protected service. Windows additionally protects these processes from code injection and different assaults from admin processes.”
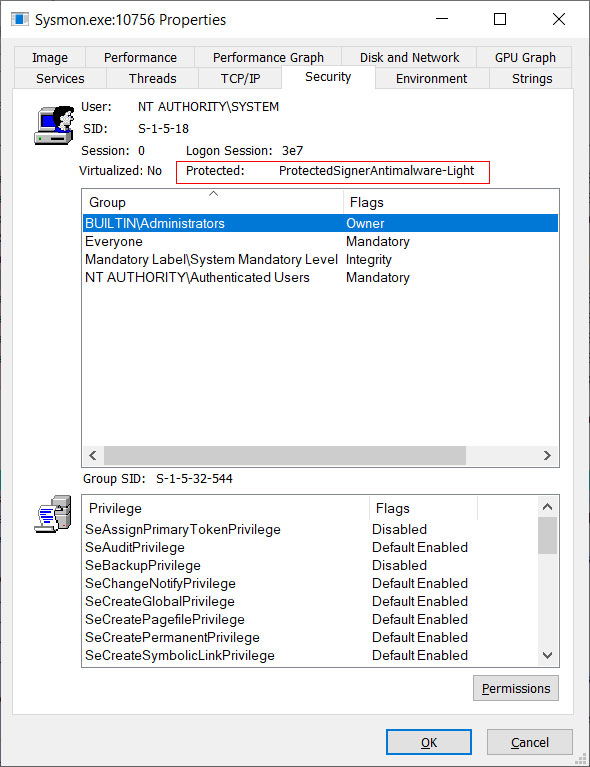
After Sysmon is launched, you possibly can see it’s a protected course of through the use of Process Explorer and analyzing its Security properties, as proven beneath.
Source: BleepingComputer
Based on Process Explorer, Sysmon is working as a PPL course of (PROTECTED_ANTIMALWARE_LIGHT), which is additional described in this text by Elastic.
Detecting new executables recordsdata
System 15.0 additionally upgrades the Sysmon schema to model 4.90, which now consists of the ‘FileExecutableDetected’ configuration choice to detect the creation of executable recordsdata on the monitored system.
<occasion identify="SYSMONEVENT_FILE_EXE_DETECTED" worth="29" degree="Informational" template="File Executable Detected" rulename="FileExecutableDetected" model="5">
<knowledge identify="RuleName" inType="win:UnicodeString" outType="xs:string" />
<knowledge identify="UtcTime" inType="win:UnicodeString" outType="xs:string" />
<knowledge identify="ProcessGuid" inType="win:GUID" />
<knowledge identify="ProcessId" inType="win:UInt32" outType="win:PID" />
<knowledge identify="User" inType="win:UnicodeString" outType="xs:string" />
<knowledge identify="Image" inType="win:UnicodeString" outType="xs:string" />
<knowledge identify="GoalFileidentify" inType="win:UnicodeString" outType="xs:string" />
<knowledge identify="Hashes" inType="win:UnicodeString" outType="xs:string" />
</occasion>
For instance, to make use of the brand new FileExecutableDetected directive to detect new executables created beneath the C:ProgramData and C:Users folders, you should utilize the next configuration file:
<Sysmon schemaversion="4.90">
<!-- Capture all hashes -->
<HashAlgorithms>MD5,SHA256</HashAlgorithms>
<EventFiltering>
<!-- Log executable file creations -->
<FileExecutableDetected onmatch="embrace">
<GoalFileidentify situation="start with">C:ProgramData</GoalFileidentify>
<GoalFileidentify situation="start with">C:Users</GoalFileidentify>
</FileExecutableDetected>
</EventFiltering>
</Sysmon>
To begin Sysmon and direct it to make use of the above configuration file, you’d execute the sysmon -i command and go the configuration file’s identify.
In our instance, the configuration file’s identify is sysmon.conf, so we’d use the next command from an Administrative Command Prompt to begin Sysmon:
sysmon -i sysmon.confOnce began, Sysmon will set up its driver and quietly accumulate knowledge within the background.
All Sysmon occasions will probably be logged to ‘Applications and Services Logs/Microsoft/Windows/Sysmon/Operational‘ within the Event Viewer.
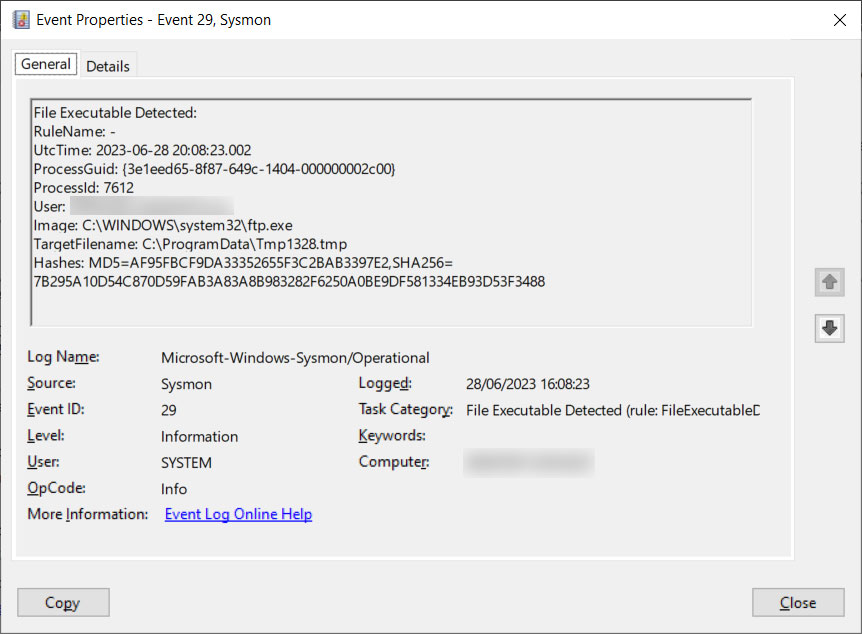
With the FileExecutableDetected characteristic enabled, when a brand new executable file is created beneath the C:ProgramData or C:Users folder (and any of their subfolders), Sysmon will generated an executable is created and matches a rule, Sysmon will block the file and generate an ‘Event 29, File Executable Detected’ entry in Event Viewer.
Source: BleepingComputer
The created Event Log entries will comprise quite a lot of precious info, defined beneath:
- UtcTime: Time the occasion was detected.
- ProcessID: The PID of the method making an attempt to create the executable file.
- User: The person related to the method creating the file.
- Image: The filename of this system creating the file.
- GoalFileidentify: The executable file that was created. Note: In our exams, the file was at all times displayed beneath a short lived file identify.
- Hash: The hash of the file that was being created. The displayed hashes will rely in your HashAlgorithms configuration setting.
For much more info and inventive tips about utilizing this new characteristic, it’s strongly beneficial that you just learn Olaf Hartong’s wonderful writeup on this new model of Sysmon.
For those that need a premade Sysmon configuration file that makes use of this characteristic to detect when identified malware or hack instrument executables are created, you should utilize safety researcher Florian Roth’s Sysmon config.
Learn extra about Sysmon
Sysmon is a complicated community monitoring instrument with a ton of directives that assist you to create configuration recordsdata that meet your group’s wants.
Due to this system’s complexity, it’s strongly suggested that you just learn the Sysmon documentation and mess around with configuration choices to see how the assorted directives work.
Unfortunately, Sysmon just isn’t a well-documented program, requiring customers to conduct trial and error to check options and see what occasions are written to the occasion log.
The excellent news is that Sysmon won’t load a misconfigured configuration file, so should you see a “Configuration file validated” message when loading Sysmon, you already know that you just’re not less than heading in the right direction.
You also needs to learn Olaf Hartong’s weblog posts about Sysmon, as he paperwork the brand new options as they’re launched.
Finally, admins can use or learn by way of the premade Sysmon configuration recordsdata from Florian Roth and SwiftOnSecurity to see how directives can be utilized to dam malware.
