[ad_1]
In May 2023, we introduced the overall availability of Routing intent and routing insurance policies for all Virtual WAN prospects. This characteristic is powered by the Virtual WAN routing infrastructure and allows Azure Firewall prospects to arrange insurance policies for personal and web visitors. We are additionally extending the identical routing capabilities to all Firewall options deployed inside Azure Virtual WAN together with Network Virtual Appliances and software-as-a-service (SaaS) options that present Firewall capabilities.
Routing Intent additionally completes two secured hub use instances whereby customers can safe visitors between Virtual WAN hubs in addition to examine visitors between completely different on-premises (department/SpecificRoute/SD-WAN) that transits by means of Virtual WAN hubs.
Azure Virtual WAN (vWAN), networking-as-a-service, brings networking, safety, and routing functionalities collectively to simplify networking in Azure. With ease of use and ease inbuilt, vWAN is a one-stop store to attach, defend, route visitors, and monitor your extensive space community.
In this weblog, we are going to first describe routing intent use instances, product experiences, and summarize with some extra issues and assets for utilizing routing intent with Virtual WAN.
Use instances for Virtual WAN
You can use Routing Intent to engineer visitors inside Virtual WAN in a number of methods. Here are the primary use instances:
Apply routing insurance policies for Virtual Networks and on-premises
Customers implementing hub-and-spoke community architectures with massive numbers of routes usually discover their networks exhausting to grasp, preserve, and troubleshoot. In Virtual WAN, these routes will be simplified for visitors between Azure Virtual Networks and on-premises (SpecificRoute, VPN, and SD-WAN).
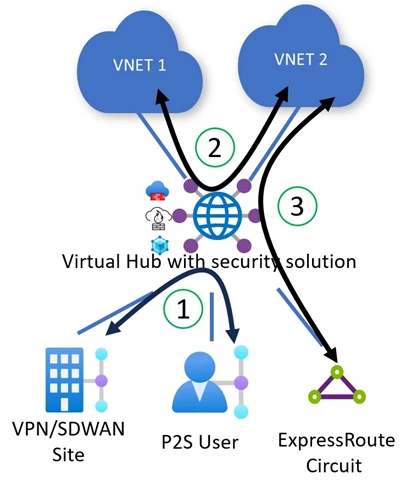
Virtual WAN makes this simpler for patrons by permitting prospects to configure easy and declarative personal routing insurance policies. It is assumed that personal routing insurance policies can be utilized for all Azure Virtual Networks and on-premises networks linked to Virtual WAN. Further customizations for Virtual Network and on-premises prefixes are at the moment not supported. Private routing insurance policies instruct Virtual WAN to program the underlying Virtual WAN routing infrastructure to allow transit between two completely different on-premises (1) by way of a safety answer deployed within the Virtual Hub. It additionally allows visitors transiting between two Azure Virtual Networks (2) or between an Azure Virtual Network and an on-premises endpoint (3) by way of a safety answer deployed within the Virtual Hub. The similar visitors use instances are supported for Azure Firewall, Network Virtual Appliances, and software-as-a-service options deployed within the hub.
Apply routing insurance policies for web visitors
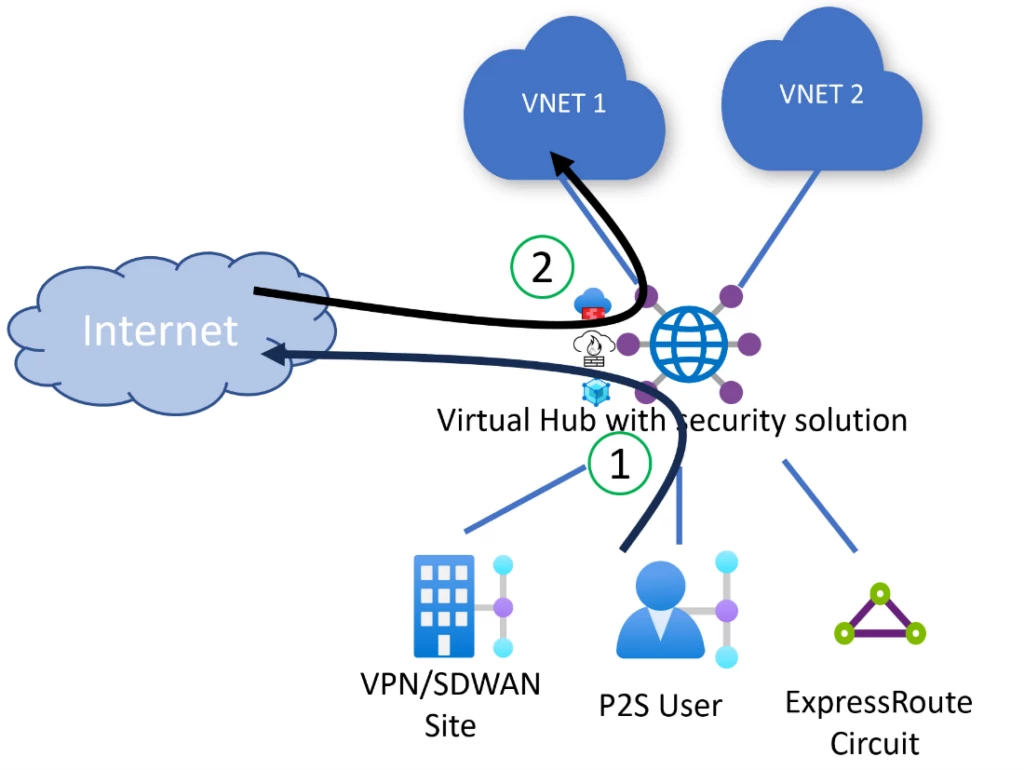
Virtual WAN helps you to arrange routing insurance policies for web visitors with the intention to promote a default (0.0.0.0/0) path to your Azure Virtual Networks and on-premises. Internet visitors routing configurations assist you to configure Azure Virtual Networks and on-premises networks to ship web outbound visitors (1) to safety home equipment within the hub. You may also leverage Destination-Network Address Translation (DNAT) options of your safety equipment if you wish to present exterior customers entry to purposes in an Azure Virtual Network or on-premises (2).
Apply routing insurance policies for inter-hub cross-region visitors
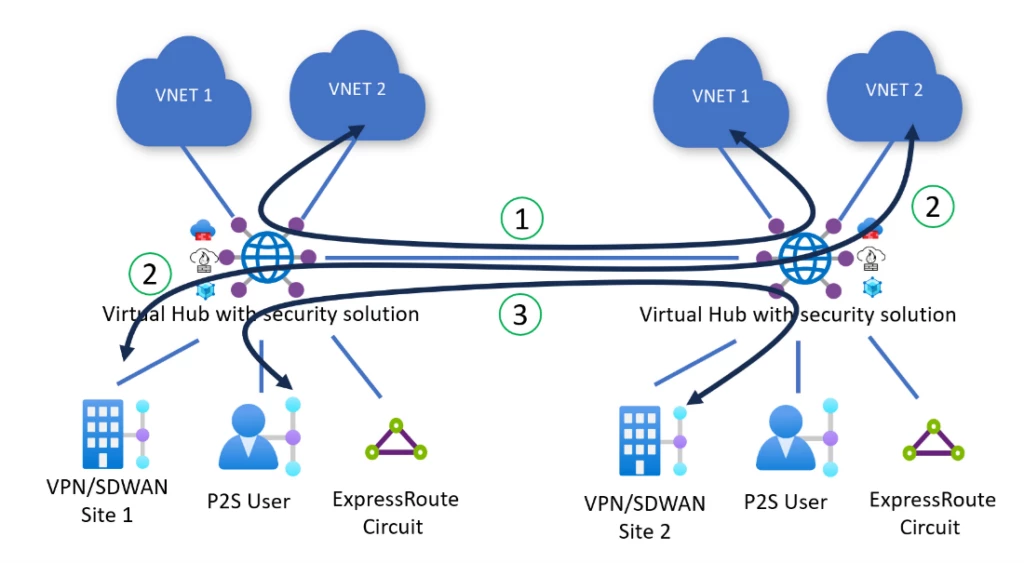
Virtual WAN robotically deploys all Virtual Hubs throughout your Virtual WAN in a full mesh, offering zero-touch any-to-any connectivity region-to-region and hub-to-hub utilizing the Microsoft international spine. Routing insurance policies program Virtual WAN to examine inter-hub and inter-region visitors between two Azure Virtual Networks (1), between two on-premises (2), and between Azure Virtual Networks and on-premises (3) linked to completely different hubs. Every packet getting into or leaving the hub is routed to the safety answer deployed within the Virtual Hub earlier than being routed to its remaining vacation spot.
User expertise for routing intent
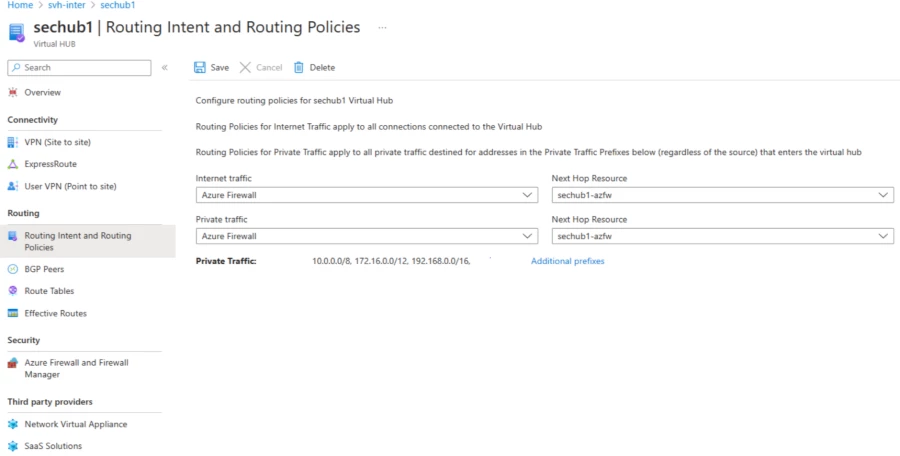
To use routing intent, navigate to your Virtual WAN hub. Under Routing, choose Routing Intent and routing insurance policies.
Configure an Internet or Private Routing Policy to ship visitors to a safety answer deployed within the hub by choosing the subsequent hop sort (Azure Firewall, Network Virtual Appliance, or SaaS answer) and corresponding subsequent hop useful resource.
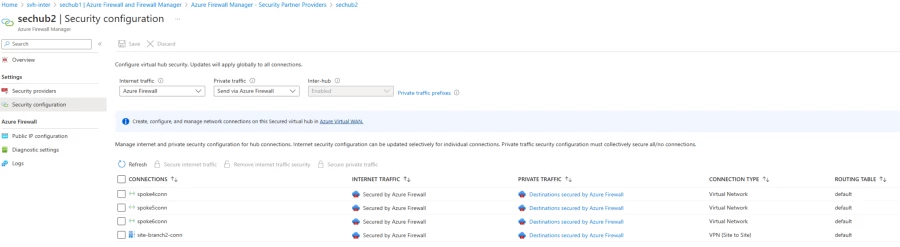
Azure Firewall prospects may also configure routing intent utilizing Azure Firewall Manager by enabling the ‘inter-hub’ setting.
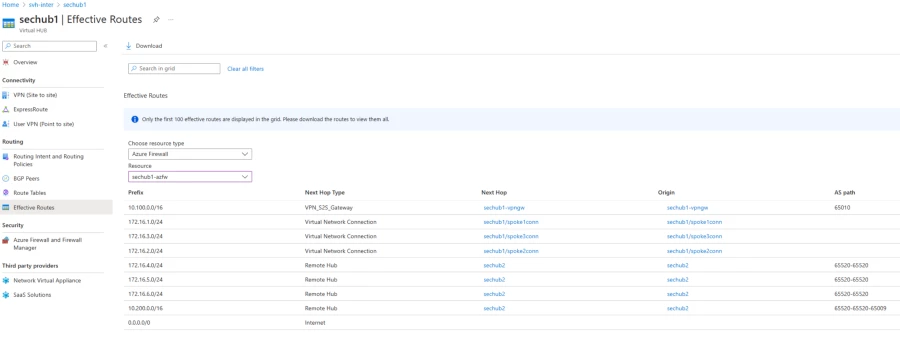
After configuring routing intent, you’ll be able to view the efficient routes of the safety answer by navigating to your Virtual Hub, then choose Routing, and click on Effective Routes. The efficient routes of the safety answer present extra visibility to troubleshoot how Virtual WAN routes visitors that has been inspected by the Virtual hub’s safety answer.
Before you get began with this characteristic, listed below are some key issues:
- The characteristic caters to customers that take into account Virtual Network and on-premises visitors as personal visitors. Virtual WAN applies personal routing insurance policies to all Virtual Networks and on-premises visitors.
- Routing intent is mutually unique with customized routing and static routes within the ‘defaultRouteTable’ pointing to Network Virtual Appliance (NVA) deployed in a Virtual Network spoke linked to Virtual WAN. As a consequence, use instances the place customers are utilizing customized route tables or NVA-in-spoke use instances are usually not relevant.
- Routing Intent advertises prefixes comparable to all connections to Virtual WAN in the direction of on-premises networks. Users might use Route Maps to summarize and combination routes and filter primarily based on outlined match circumstances.
Learn extra about Azure Virtual WAN
We stay up for persevering with to construct out Azure Virtual WAN and including extra capabilities sooner or later. We encourage you to check out the Routing Intent characteristic in Azure Virtual WAN and stay up for listening to extra about your experiences to include your suggestions into the product.
