[ad_1]
In 2020, we built-in kCTF into Google’s Vulnerability Rewards Program (VRP) to help researchers evaluating the safety of Google Kubernetes Engine (GKE) and the underlying Linux kernel. As the Linux kernel is a key part not only for Google, however for the Internet, we began closely investing on this space. We prolonged the VRP’s scope and most reward in 2021 (to $50k), then once more in February 2022 (to $91k), and eventually in August 2022 (to $133k). In 2022, we additionally summarized our learnings thus far in our cookbook, and launched our experimental mitigations for the most typical exploitation strategies.
In this submit, we might wish to share our learnings and statistics in regards to the newest Linux kernel exploit submissions, how efficient our mitigations are towards them, what we do to guard our customers, and, lastly, how we’re altering our program to align incentives to the areas we’re most interested by.
Learnings and Statistics
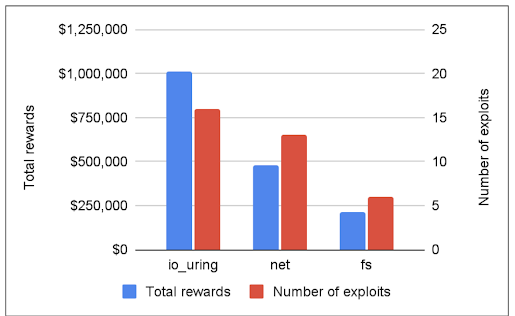
Since its inception, this system has rewarded researchers with a complete of 1.8 million USD, and up to now 12 months, there was a transparent pattern: 60% of the submissions exploited the io_uring part of the Linux kernel (we paid out round 1 million USD for io_uring alone). Furthermore, io_uring vulnerabilities had been utilized in all of the submissions which bypassed our mitigations.
Limiting io_uring
To shield our customers, we determined to restrict the utilization of io_uring in Google merchandise:
While io_uring brings efficiency advantages, and promptly reacts to safety points with complete safety fixes (like backporting the 5.15 model to the 5.10 secure tree), it’s a pretty new a part of the kernel. As such, io_uring continues to be actively developed, however it’s nonetheless affected by extreme vulnerabilities and in addition gives robust exploitation primitives. For these causes, we at the moment contemplate it protected just for use by trusted parts.
Transparency
Currently, we make vulnerability particulars public on our spreadsheet (which now additionally consists of CVE particulars), and we’ve got summarized completely different exploitation strategies in our cookbook. In the long run, to make our efforts extra clear and provides quicker suggestions to the neighborhood, we are going to ask researchers to open-source their submissions, together with the code they used.
Introducing kernelCTF
To higher align incentives with our areas of curiosity, we’re shifting our focus from GKE and kCTF to the newest secure kernel and our mitigations. As a consequence, beginning at the moment we are going to deal with kernel exploit submissions underneath a brand new identify, “kernelCTF,” with its personal reward construction and submission course of. The most complete payout for kernelCTF remains to be $133,337 per submission. While the precise GKE kernel configuration remains to be lined by the brand new kernelCTF, exploits affecting non-kernel parts like the total GKE stack (together with Kubernetes), the container runtime, and GKE itself, at the moment are individually eligible for vulnerability rewards underneath the kCTF VRP which is returning to its authentic reward quantities and situations.
Conclusion
Our aim stays the identical: we’re constructing a pipeline to research, experiment, measure, and construct safety mitigations to make the Linux kernel as protected as potential, with the assistance of the safety neighborhood. We hope that over time, we will implement safety mitigations that make it tougher to use Linux kernel vulnerabilities.
With the identify change, we’ve got moved our communication channel to #kernelctf on Discord, with a separate #kernelctf-announcements channel. Please be a part of us there for the newest updates concerning kernelCTF.
[ad_2]