[ad_1]
In Verizon’s just-released 2023 Data Breach Investigations Report, cash is king, and denial of service and social engineering nonetheless maintain sway.

Verizon’s just-released 2023 Data Breach Investigations Report reveals the continued effectiveness of enterprise e-mail compromises. The examine, which tracked incidents occurring between November 1, 2021 and October 31, 2022, discovered that BEC assaults doubled and represented greater than 50% of social engineering assaults. The international examine included incidents within the Asia-Pacific areas, EMEA, North America, and Latin America.
BECs have developed to incorporate a number of subtle gambits, together with one lately reported by Avanan, a unit of Check Point Software, involving using reputable companies, like Dropbox, to cover malware.
The examine supplied a broad have a look at actors, actions, traits and incidents throughout industries, noting that public administration (3,270 incidents), info (2,105), finance (1,829) and manufacturing (1,814) are the sectors that skilled the very best numbers of incidents over the interval.
The report supplied these main findings:
- 74% of all breaches included the human ingredient, with folks being concerned both through error, privilege misuse, use of stolen credentials or social engineering.
- 83% of breaches concerned exterior actors, and the first motivation for assaults continues to be overwhelmingly financially pushed (95%).
- The three major methods through which attackers entry a company are stolen credentials, phishing and exploitation of vulnerabilities.
Jump to:
Social engineering pretexts trick customers into dropping credentials
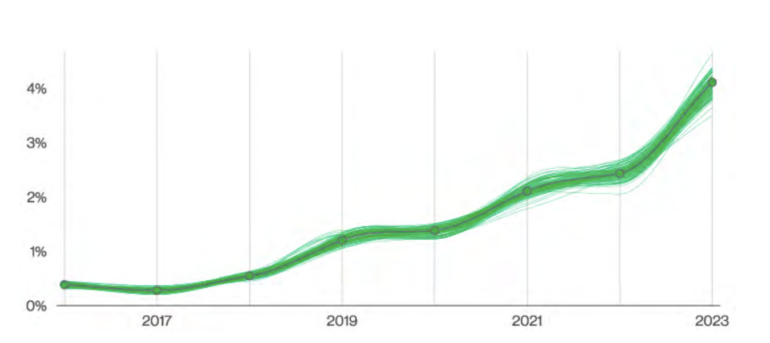
Built upon evaluation of 953,894 incidents, of which 254,968 are confirmed breaches, the Verizon examine discovered that fifty% of all social engineering incidents through the examine interval used pretexting, a phishing tactic that includes tricking somebody into giving up info that will end in a breach. According to the examine, the follow, which is usually utilized in BEC assaults, doubled in quantity in comparison with the prior yr’s.
Verizon reported 1,700 social engineering incidents total, with attackers most frequently utilizing it to steal credentials (Figure A).
Figure A
SEE: Half of firms tracked in a new examine had been hit by spearphishing campaigns (TechRepublic)
Financial achieve trumps politics in exploits
An uptick in espionage and state-aligned actors however, the Verizon examine reported that monetary motives had been behind 94.6% of breaches, with organized crime being probably the most prevalent menace actor.
The authors of the examine additionally reported a fourfold improve this yr within the variety of breaches involving cryptocurrency in comparison with the prior yr’s recorded breaches. “That is a far cry from the days of innocence in 2020 and earlier, when we got one or two cases maximum each year,” they wrote.
Verizon reported the chances of financially motivated assaults by class:
- System intrusions: 97%, with solely 3% geared toward espionage.
- Social engineering exploits: 89%, with 11% geared toward espionage.
- Basic internet software assaults: 95%, with 4% geared toward espionage.
- Lost and stolen property: 100% monetary achieve.
DDoS tops the record of assault patterns
Verizon reported 6,248 distributed denial of service incidents. The examine’s authors famous the brute drive DDoS tactic referred to as DNS water torture reportedly grew in prevalence (Figure B).
Figure B
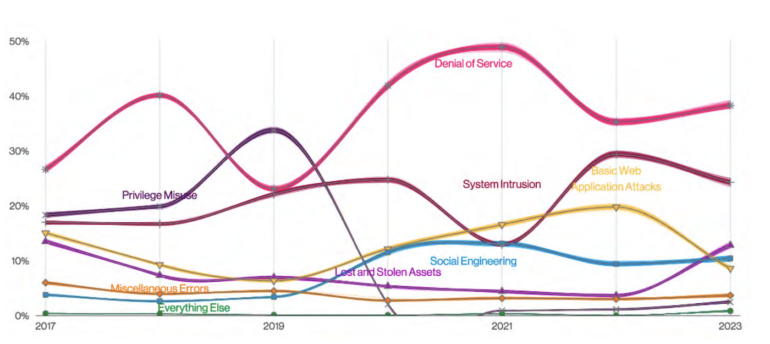
“A point of attention that some of our partners brought to us was the growth of distributed DNS Water Torture attacks in, you guessed it, shared DNS infrastructure,” the examine authors wrote, noting the assaults are a useful resource exhaustion assault completed by querying random identify prefixes on the DNS cache server so it at all times misses and forwards it to the authoritative server.
According to the examine, there have been 3,966 system intrusion incidents involving assaults utilizing malware to breach organizations, which frequently resulted within the supply of ransomware. In 34% of instances, information compromised was private in nature, adopted by system information, and eventually inner information.
SEE: Web customers should not very conscious of their information footprints. (TechRepublic)
Use of stolen credentials drives internet software assaults
About one quarter of Verizon’s dataset for its examine concerned primary internet software assaults, 86% of them utilizing stolen credentials, which attackers make use of to achieve entry to enterprises. The examine reported 1,404 such incidents over its interval of commentary, with 86% geared toward credential theft, 72% for private information and 41% in search of inner information.
Verizon additionally recorded 602 miscellaneous errors that embody misconfigurations usually dedicated by system directors and builders. The examine reported that 99% of those errors had been inner, with 89% of compromises involving private information.
Insiders, sure, however largely exterior actors
Attackers on the skin had been liable for 83% of breaches, whereas inner actors (intentionally or inadvertently) accounted for 19% of breaches, based on Verizon. The report’s authors mentioned 62% of all incidents had been dedicated by organized crime.
Stolen credentials: The commonest motion
Nearly half of breaches within the examine interval concerned theft of credentials, with supply of ransomware being the central motion in simply over 20% of breaches. Phishing was the motion attackers took in 12% of exterior assaults, adopted by breaches, through which the actions attackers centered on had been:
- Pretexting
- Exploiting vulnerabilities
- Creating misdeliveries
- Abusing privilege
- Installing a backdoor
- Exfiltrating information
- Scanning networks
Attacked property led by internet servers
The overwhelming majority of assaults tracked by Verizon (83%) affected servers. Only 20% of assaults affected folks immediately. A decreasingly small share of assaults impacted media, kiosks and terminals, networks and embedded methods.
